We earn commission when you buy through affiliate links.
This does not influence our reviews or recommendations.Learn more.
Even a small vulnerability in your program or connection can lead to serious problems like DDoS attacks.

Learn thedifference between DoS and DDoS attack.
But first, lets understand the basics.
What Is a DDoS Attack?

It can exploit computers and other related data pipe resources, likeIoT devices.
The most targeted businesses are:
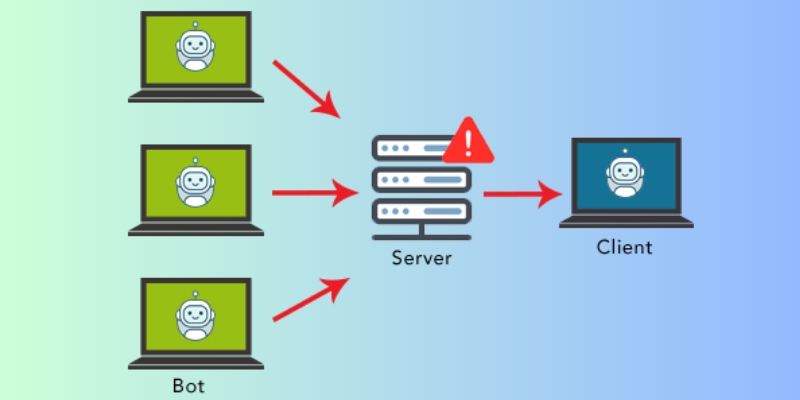
Generally, attackers use a Botnet to carry out such attacks.
Hackers use these online grid devices to send multiple requests to a server IP address or a target website.

Learn how tosecure router against Mirai Botnet attacks.
How Does a DDoS Attack Happen?
Attackers use internet-connected zombie machines to carry out DDoS attacks.
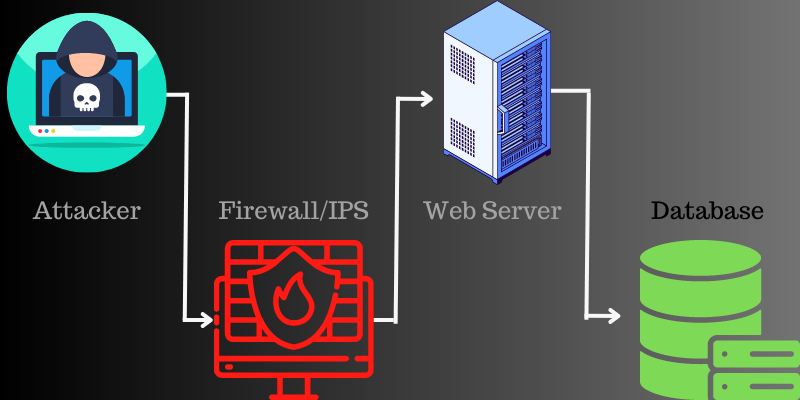
These individual devices are known as bots, and a set of bots is known as a botnet.
Since each bot is a single internet unit, it is difficult to separate normal traffic from attack traffic.
This fetching and packaging process happens on this layer.

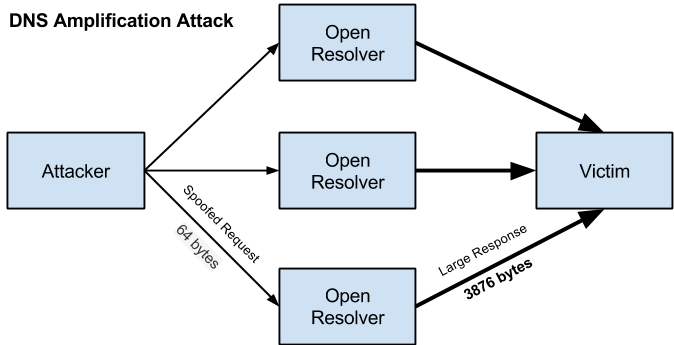
The most common attack that attackers use is the DNS amplification attack.
The DNS server sends the response to the server targeted by the attackers.
When two computers initiate a communication channel, they do a TCP handshake.
This means two parties exchange their preliminary information.
The server will respond to every packet, requesting to complete the handshake.
This can slow down the performance of the server.
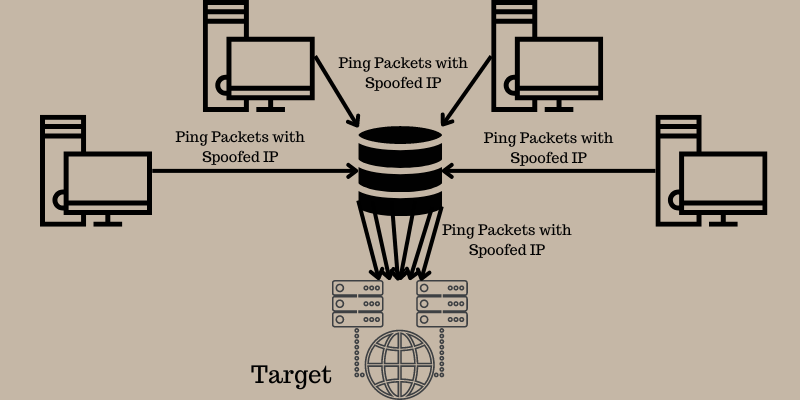
Lets discuss them and how they can impact your business.
You should check out how to protect from Smurf attacks.
An HTTP flood is a key in of DDoS attack coming under volumetric attacks.
These are specially designed to overload the targeted server with too many HTTP requests.
#2.DNS Flood
Domain Name Systems (DNS) are like the phonebooks of the internet.
A similar thing happens in the DNS Flood scenario.
Hence, a website will be compromised, and it wont be able to respond to legitimate traffic.
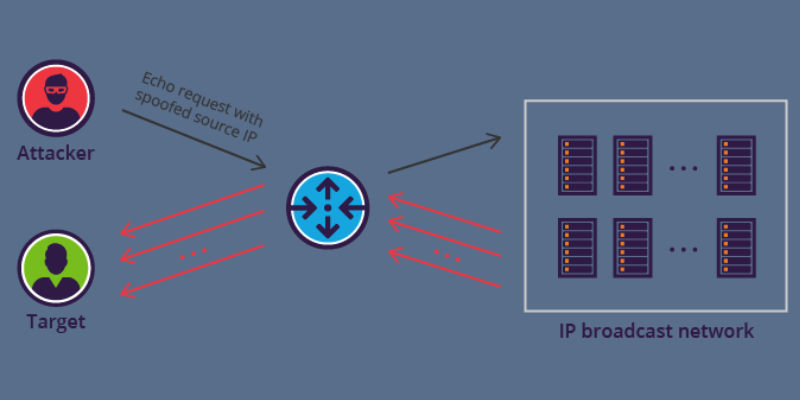
In the Ping Flood attack, the hacker attempts to overload a targeted machine with echo-request packets.
This makes the target incapable of accessing normal heavy traffic.
When fake traffic comes from numerous devices, the attack forms a DDoS attack.
By continuously sending initial connection request packets, the hacker can overload all the ports on the server machine.
This enables the gear to respond to legal traffic sluggishly or yield no response at all.

The firewall becomes exhausted, resulting in a DDoS attack.
This makes the server, along with its surrounding infrastructure, inaccessible.
Every amplification attacks exploit a discrepancy in the consumption of bandwidth between the targeted web source and an attacker.
As a result, the web link becomes clogged with fake traffic, causing DDoS attacks.
XML-RPC pingback is a common functionality of the WordPress module.
This can lead to many different attacks as it exposes your site to attract various attacks.
Some attacks are Brute Force attacks, Cross-site port attacks, Patsy proxy attacks, and more.
ExploreBrute-force attack toolsfor pen test.
It comes under an app layer attack that occurs by using partial HTTP requests.
This pop in of attack requires low bandwidth and aims to use server resources.
#9.Smurf DDoS Attack
A Smurf attack occurs at the web link level.
This name came forward after malware, DDoS.Smurf, that enables attackers to execute the attack.
The attackers aim to target bigger companies so you can take them down.
Hackers take advantage of the vulnerability and execute the attack easily.
Once this vulnerability becomes public, it is called a one-day or n-day vulnerability.
Now that we know about different types of attacks, lets discuss some solutions to mitigate them.
It offers zero-day vulnerability protections.
According to leading analysts, Cloudflare is an software security expert.
#1.Cloudflare
Get industry-leading DDoS prevention fromCloudflareto safeguard your website and prevent losing customers and their trust.
Its 197 Tbps data pipe blocks more than 112 billion daily threats.
The global data pipe of Cloudflare spans 285+ cities and 100+ countries to prevent attacks.
Doing this can mitigate website, system, and web connection DDoS attacks.
It maintains your websites health even during massive DDoS attacks and high traffic spikes.
Sucurican easily block spoofed requests and traffic from various malicious bots without disturbing legal traffic sources.
Its high-quality technology and hardware perform 24/7 to protect your website from malicious activities.
Discussed above are some of the best solutions to fight against app, volumetric, and protocol attacks.
They help prevent unwanted traffic coming from different sources to retain the bandwidth and eliminate downtimes.