We earn commission when you buy through affiliate links.
This does not influence our reviews or recommendations.Learn more.
Kaspersky Cybermap Highlights
2.
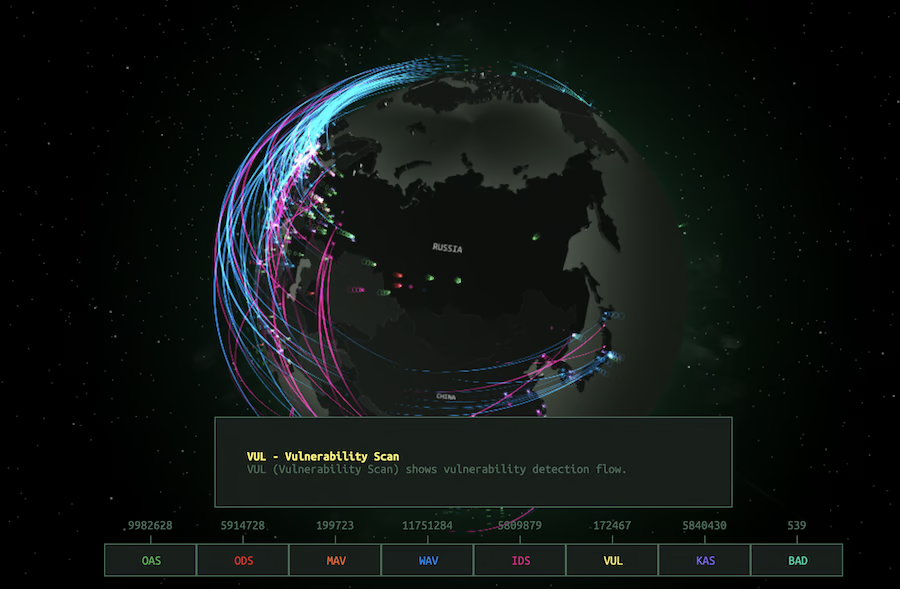
Threatbutt Highlights
3.
The map provides visibility that teams can use to evaluate andimprove security postureand resource allocation.
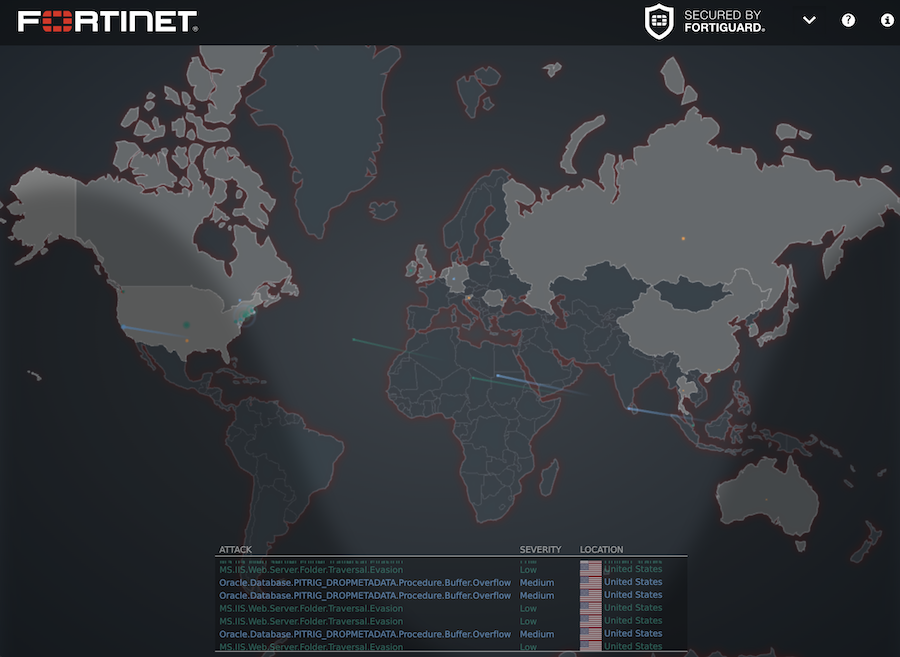
FortiGuard Threatmap Highlights
4.
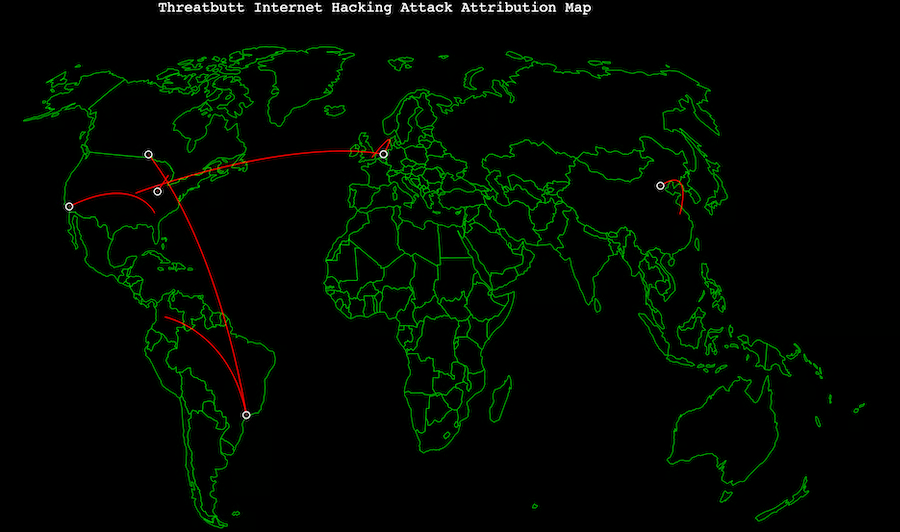
Digital Attack Maps
Digital Attack Map displays daily DDoS attacks worldwide.
Security teams can also use the threat intelligence from the maps to deploy or enhance theirDDoS protection services.
Digital Attack Maps Highlights
5.
Checkpoint Threatmap
The Checkpoints Threatmap displays DDoS attacks in real-time.
It color-codes the attacks by severity to help security teams easily identify and focus on the critical threats.
Checkpoint Threatmap Highlights
6.
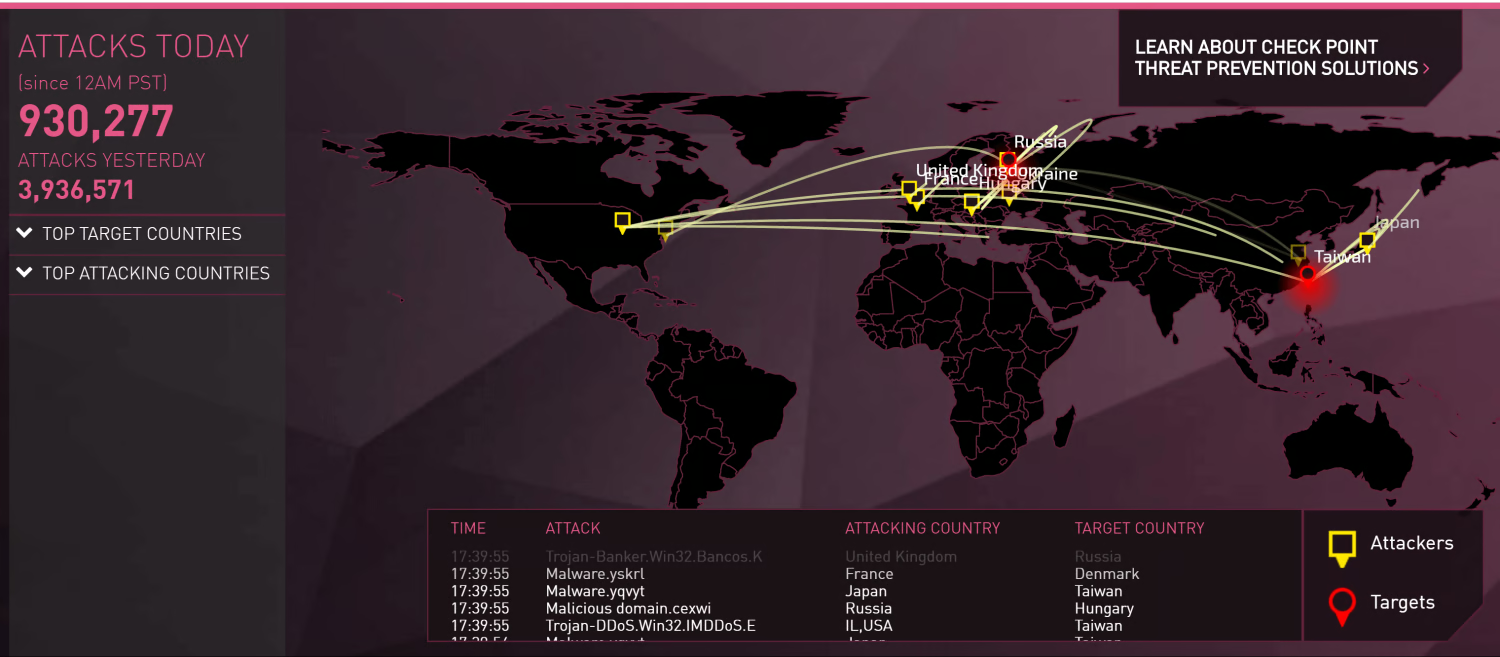
Bitdefender Real-Timethreat Map
Bitdefender threat map provides infections, attacks, and spam.
Bitdefender claims that the threat map displays attacks in real-time.
Bitdefender Threat Map Highlights
7.
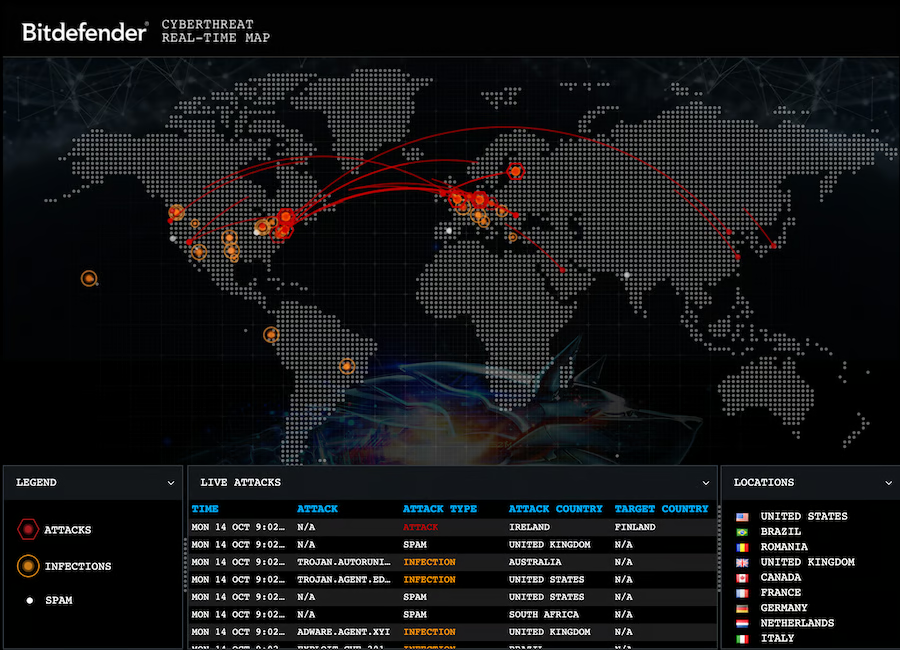
Data is collected from Cisco and third-party feeds worldwide.
Talos Cyber Attack Map Highlights
8.
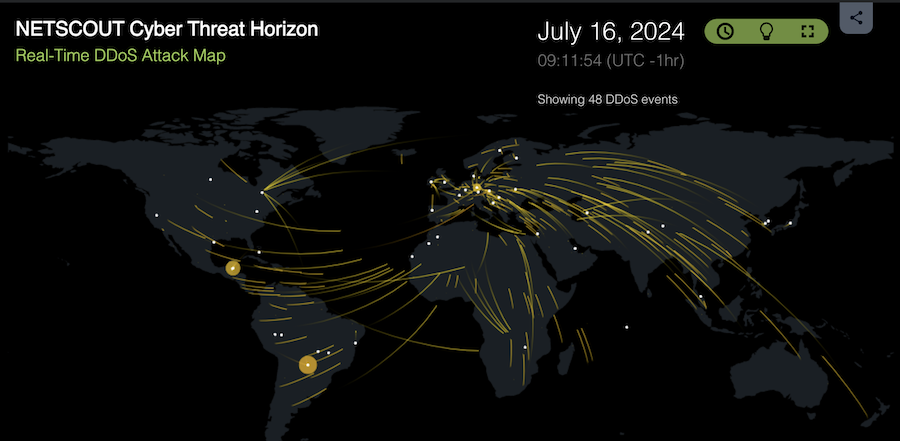
NetScout Cyber Threat Horizon Highlights
9.
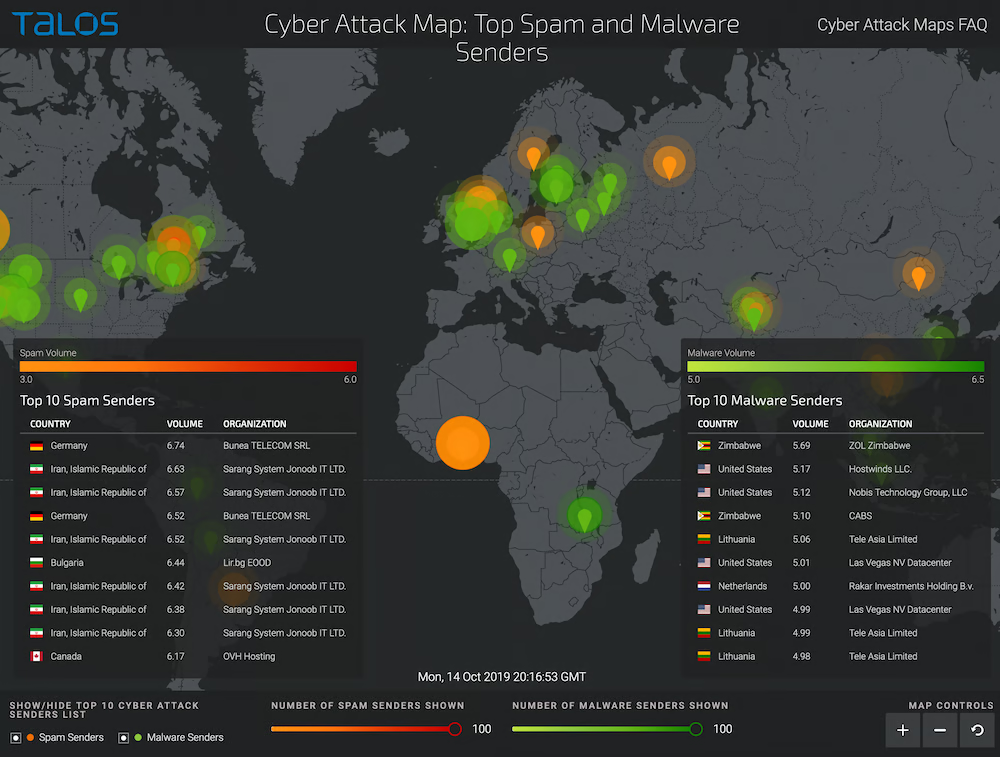
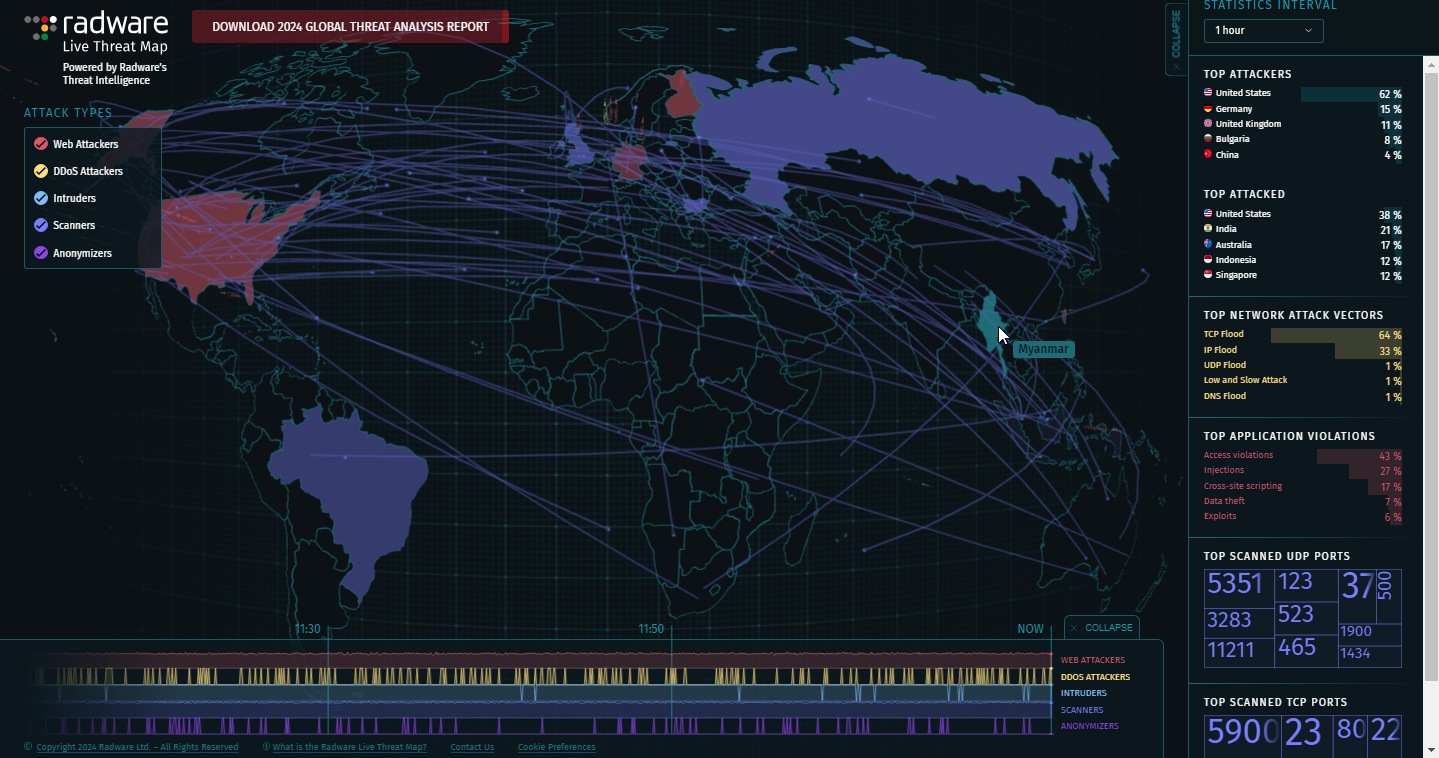
The map provides statistics for the top 5 attackers and victims including their countries and percentage share.
Radware Live Threat Map Highlights
10.
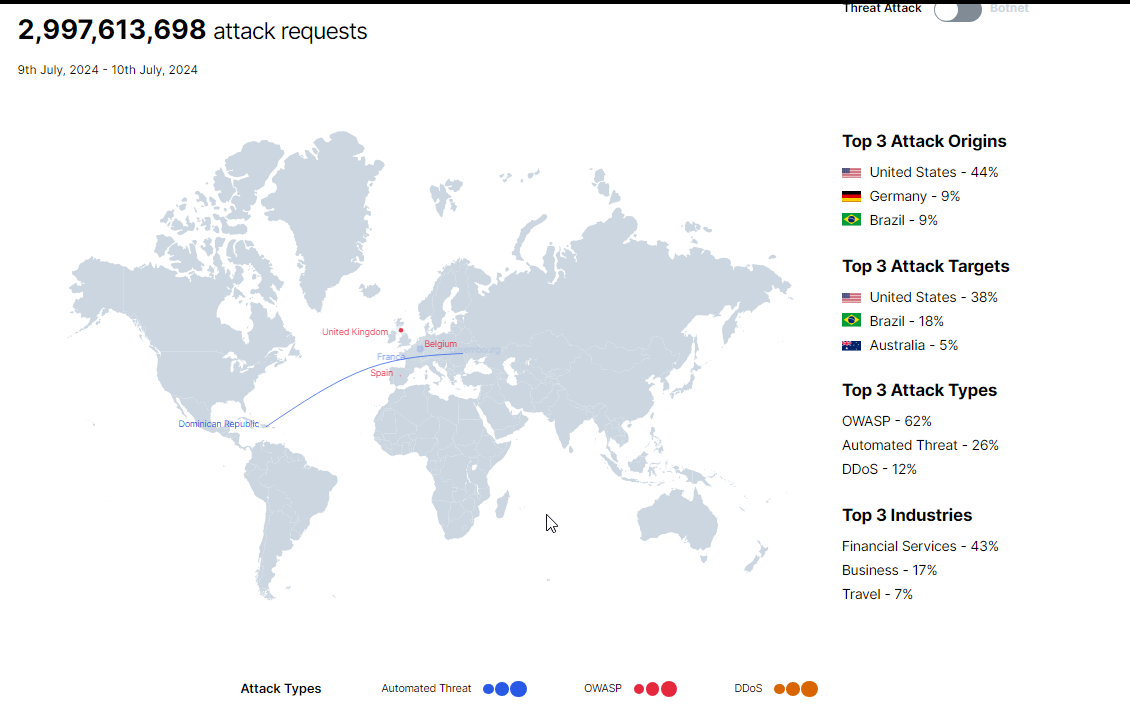
Available options include automated threat, DDoS, and OWASP displays.
Imberva Cyber Threat Attack Map Highlights
11.
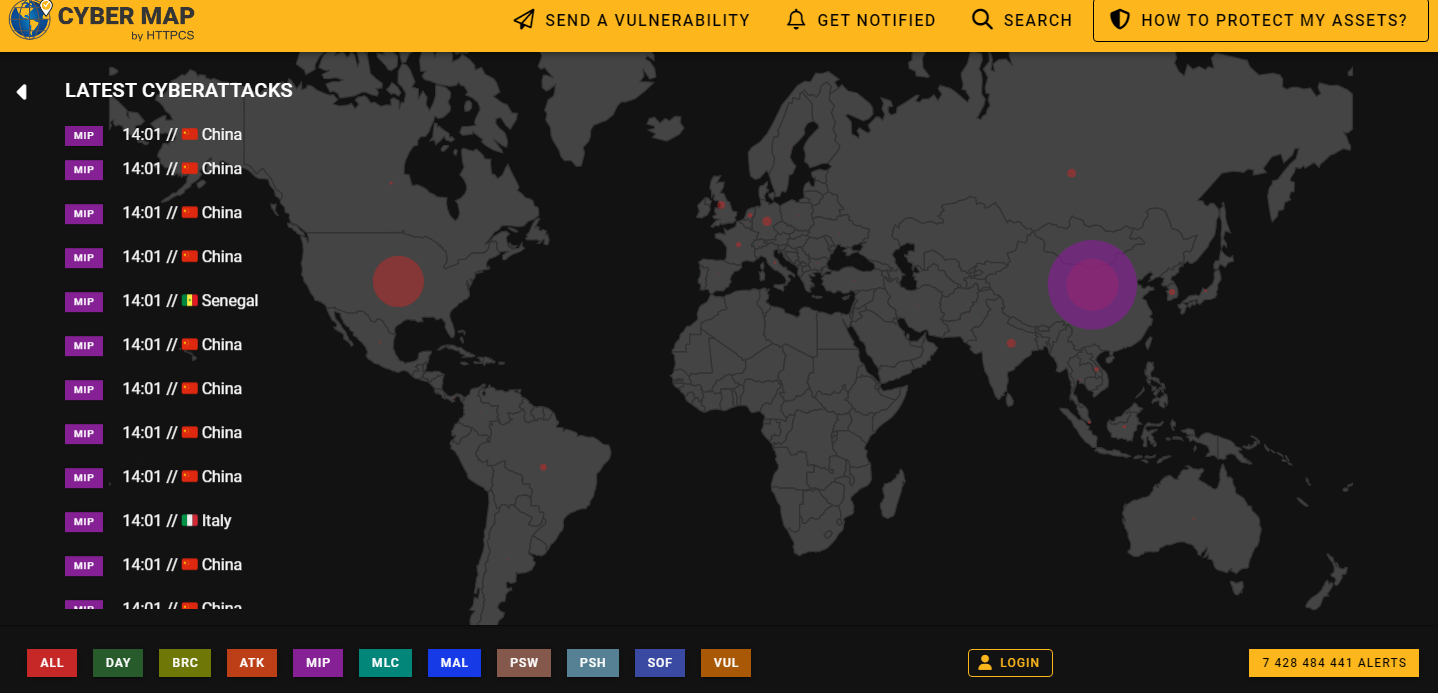
HTTPS Cyber Map Highlights
What is a Cyber Threat?
The number of attacks continues to increase as bad actors devise new ways to identify and exploit security vulnerabilities.
A study by Bromium established that cybercriminals make over 1.5 trillion dollars of illicit money from their victims annually.
One way of determining the current and previous threats is to look at the cyber threat maps.
The cyber-attack map visualizes the global threats in real time showing the volumes, source, and target countries.
Some maps may add IP addresses and color-code the attacks by severity.
How Do Cyber Threat Maps Work?
The cyber threat map shows a visual representation of the near real-time threats and/or historical threats across the world.
The details on the map may vary from one map provider to the other.
Most maps include types of threats, severity, volumes, source, and target countries.
The cyber-attack map is real and shows current threat activities across the world.
However, the display may not represent the cyber threats in real-time.