We earn commission when you buy through affiliate links.
This does not influence our reviews or recommendations.Learn more.
app and API attacks have surged recently.
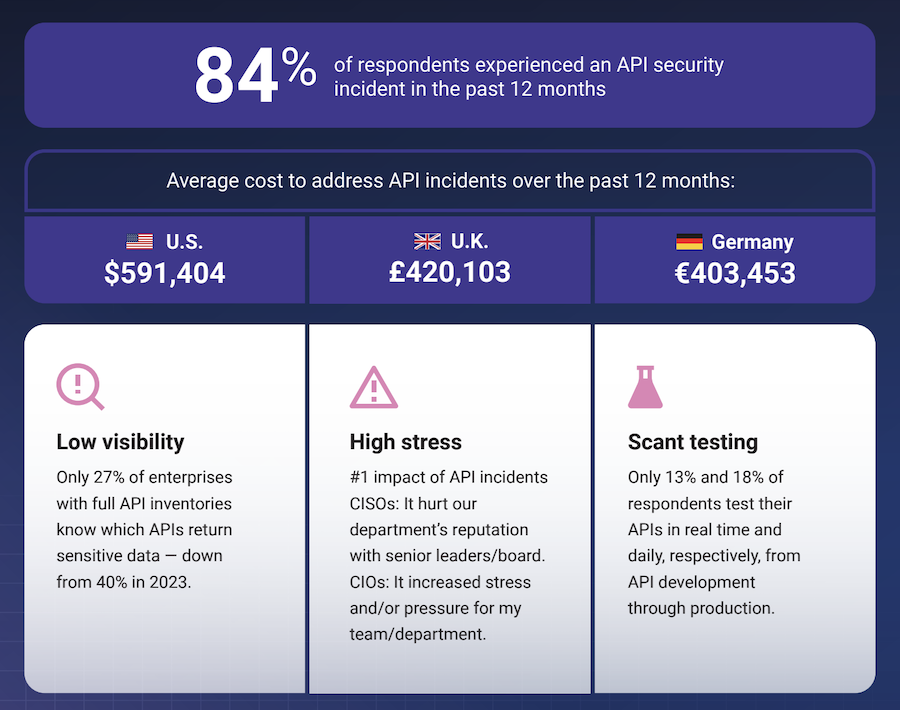
So, you must find and fix vulnerabilities in your App or API to prevent hackers from exploiting them.
However, finding the right DAST scanner can be tricky, especially when youre new to scanning tools.
Check out the list below!
it’s possible for you to trust Geekflare
At Geekflare, trust and transparency are paramount.
Probely
Probely is a trusted DAST scanner that automates and scales web applications and API security testing.
Its vulnerability scanner helps you identify around 30,000 vulnerabilities and provides a detailed report to fix them.
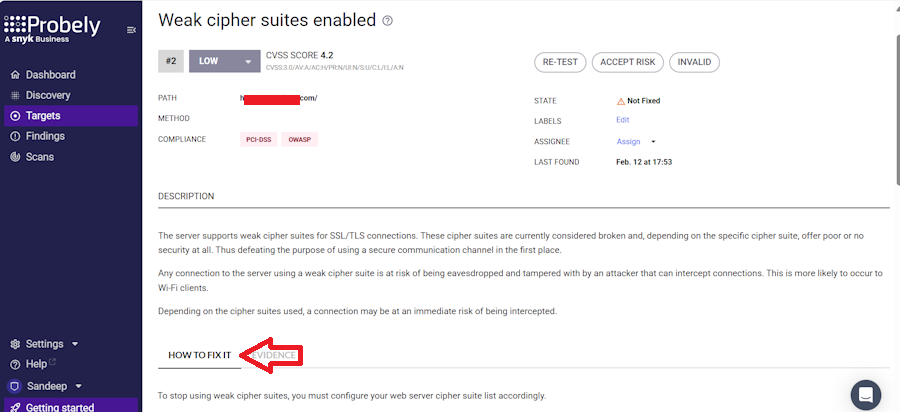
Its headless Chrome-based spider navigates through a web system like a human.
you could easily integrate Probely with CI/CD tools, issue trackers, and messaging apps.
As a result, you could quickly prioritize vulnerability management.
I also found the dashboard informative and easy to navigate.
Probely Pricing
It offers a forever-free plan with 5 free scan hours/month.
The Enterprise plan follows custom pricing.
Probely provides a free 14-day, fully-featured trial.
you could also request a demo to have a guided product tour.
It combines signature and behavior-based testing to ensure no vulnerability or security weakness goes unnoticed.
The platform identifies all of your open-source components and detects which components are vulnerable.
It helps you track the security posture of each software over time.
Invicti can be integrated with 50+ tools, including CI/CD, issue trackers, collaboration tools, and more.
The IAST sensor connects to the software runtime while the DAST engine scans for vulnerabilities.
When DAST finds an issue, IAST provides detailed insights, like file names and line numbers.
It is a good feature for fast vulnerability remediation.
Also, its proof-based scanning minimizes false positives.
Invicti Pricing
Invicti pricing is available on request.
A free demo is available to explore its features.
Indusface WAS
Indusface WAS offers you functions of DAST, malware scanning, and penetration testing.
And its AcuRisQ feature lets you prioritize security issues that pose the highest risks.
Indusface WAS Pricing
Indusface WAS pricing starts at $59/app/month.
It offers a 14-day free trial.
Rapid7 InsightAppSec
InsightAppSec by Rapid7 automatically assesses your web app with fewer false positives and missed security weaknesses.
Small or big, you could manage the security assessment of your program portfolio effortlessly with InsightAppSec.
The universal translator in InsightAppSec increases your tool coverage area.
Also, It offers custom checks to address issues and risks your app environment faces.
I liked that InsightAppSec enables you to collaborate at speed.
Its rich reporting and integrations make informing compliance and development stakeholders seamless.
you could easily tailor reports to several compliance regulations, such as HIPAA, PCI-DSS, and more.
InsightAppSecs scan engines support both on-prem and cloud-based deployment.
you might easily integrate InsightAppSec into your dev workflows.
It delivered the report in 29 minutes.
It tested my site for more than 95+ attacks, including OWASP Top 10, misconfiguration, and more.
I found its dashboard intuitive and liked its ability to schedule and blackout scans.
InsightAppSec Pricing
InsightAppSec pricing starts at $175/month per app.
The company offers a generous 30-day free trial.
you could also watch an online demo to understand the product better.
It is language agnostic and runs on any platform.
StackHawk is designed to focus on runtime and pre-production program security testing.
It allows your team to actively test your tool as part of their CI/CD workflows.
It offers 4 packages for users: Free, Pro, Enterprise, and Custom.
You also get to run technology-specific API Scan Configs.
StackHawk Features
During my research, I noted that StackHawk is customizable.
you might create custom test scripts to scan your app for any specific coverage.
It covers a wide range of vulnerabilities, including SQL injection, cross-site scripting, and various others.
StackHawk Pricing
StackHawk pricing starts at $42 per code per contributor (5 contributors minimum).
It offers a 14-day free trial.
The containerized solution runs in your environment with Docker.
It allows you to manage security issues via a unified web dashboard shared with SOOS SCA.
The platform leverages Industry-Standard Open Source ZAP Scanner with added features to offer your app broad security coverage.
It can also push issues to GitHubs Security Panel.
SOOS DAST Pricing
SOOS DAST pricing starts at $90 per month.
A free trial is available.
Veracode DAST has a <5% false positive rate.
Plus, the remediation guidance is informative.
As a result, you might fix vulnerabilities efficiently, while on-demand expertise offers support when needed.
Veracode DAST Pricing
Veracode DAST pricing is available on request.
The company offers a 14-day trial and product demo.
It can automate scanning in hard-to-reach, password-protected areas.
The platform offers an accurate view of your attack surface and assigns a score to vulnerabilities it detects.
This helps you prioritize vulnerability management.
Also, it allows you to scan multiple environments simultaneously.
Acunetix comes with SCA to scan open-source components of your web software.
Easy scan scheduling allows you to automate scanning.
Acunetix Pricing
Acunetix pricing is available on request.
The company offers a free demo.
The solution offers you a complete overview of vulnerabilities.
You will have expert remediation tips to address detected security issues.
you’re free to filter and tag findings to initiate the remediation process faster.
So you will have an up-to-date scanner to scan your utility.
Detectify Pricing
Detectifys system scanning pricing is quote-based.
It offers a 14-day free trial and a free demo to explore the product.
The platform allows you to schedule recurring scans at flexible intervals.
It automatically detects new vulnerabilities with proactive emerging threat scans.
The system prioritizes security risks intelligently and provides remediation advice, helping you focus on the most critical issues.
This ensures continuous scanning for vulnerability detection and remediation for your web applications with minimal manual effort.
It can also scan your API for security vulnerabilities.
For compliance support, you’re free to easily integrate Inrtuder with Drata.
Ive also verified from Intruders product documents that it supports unlimited users and unlimited ad-hoc scans.
Intruder Pricing
Intruder system scanner pricing starts at $99/month.
A free 14-day trial is available to explore its features.
Burp
Burp Suites Enterprise plan offers unlimited automated DAST scanning.
It provides you with complete visibility into the attack surface of your system or API.
It also supports custom Burp extensions, GraphQL API, and SSO for easy access.
you’re free to also track security changes over time by visually comparing deltas and updates.
This helps you understand how your attack surface evolves.
Another great feature is that it supports Role Based Access Control (RBAC).
Burp Scanner provides clear remediation advice for every detected issue.
PortSwigger Research and the Web Security Academy offer expert guidance, helping you fix vulnerabilities effectively.
The pricing is available on request.
A free trial is available to explore features.
Checkmarx DAST
Checkmarx DAST is a powerful web security scanner available in the Checkmarx One tool security platform.
A single platform enables you to run SAST and DAST scans, offering a seamless AppSec experience.
Additionally, it supports various languages and integrations.
you gotta hit up the company to get pricing details.
A free demo is available.
What Is DAST and How Does It Work?
DAST doesnt have access to the source code of an program.
So, it detects security vulnerabilities by carrying out simulated attacks.
In a sense, DAST tools perform automatedpenetration testingof your web app to identify security weaknesses in the app.
In other words, a DAST tool works like a security guard you appointed to protect your home.
This security guard is more than just an ordinary security guard.
Instead, the guard tries to assess your homes security by breaking into your house like burglars would.
In the process, the tool assesses system security posture.
This can include finding potential input fields within an program, forms, API endpoints, etc.
The DAST tool generates a detailed report on its findings, including identified vulnerabilities and recommendations for remediation.
Security professionals can use this report to address security concerns and improve system security.
Vulnerability Coverage
Vulnerability coverage is the most critical feature of a DAST scanner.
Automated Scan
A good DAST tool offers automated scanning, which reduces the hassle of manually initiating security scans.
So, verify the DAST scanner you are considering allows you to schedule scans.
Integrations
The tool must support standard integrations like CI/CD pipelines, issue trackers, and security platforms.
Broad and seamless integration support helps you enforce a secure app development culture.
Real-time Insights
Detailed reports and real-time alerts help your security teams respond quickly.
The DAST tool should also provide actionable insights through continuous and automated security checks for faster remediation.
Compliance Support
Meeting security standards like OWASP, GDPR, and PCI DSS is important to avoid legal liabilities.
These standards will also depend on the nature and location of your business.
So, pick a DAST tool that helps you meet various compliances applicable to your business.
It is easy to combine DAST with other web system security testing methods, such as SAST.
For DAST, you dont require access to the source code of an app.
The answer is both.
By combining these two app security testing methodologies, you might comprehensively assess your web tool security.
Conclusion
Web utility attacks are skyrocketing.
Hackers target web apps and APIs to steal sensitive data or deliver malware.