We earn commission when you buy through affiliate links.
This does not influence our reviews or recommendations.Learn more.
You receive a digital ransom note demanding payment for their release.

This is not just terrifying but a harsh reality that thousands of people have faced.
What Is a Ransomware Attack?
Then comes the demand: pay up or bid your data goodbye.

Its a sudden and shocking moment that can occur via harmful links, email attachments or compromised websites.
These attacks dont discriminate they hit individuals and businesses, causing chaos and data loss.
So, prevention is key.

The types of ransomware are:
We talk about them in detail later in the article.
Cybercriminals are continuously enhancing their tactics and targets, extending beyond individuals to businesses and organizations.
According to Statista, around70% of organizationsworldwide suffered some kind of ransomware attack.
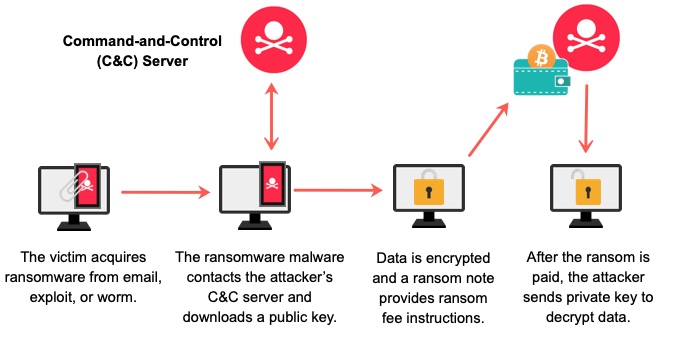
These attacks typically exploit system vulnerabilities and are often spread through email attachments or malicious websites.
Importance of Understanding Ransomware Attacks
Understanding ransomware attacks is crucial for your digital safety.
Here are four reasons why:
Knowledge about how ransomware works empowers you to take preventive steps.

you’re able to identify suspicious emails, links, or attachments and avoid falling victim.
For businesses, ransomware can cause operational disruptions and result in financial losses.
In case youre targeted, knowing about ransomware gives you the upper hand.

How Do Ransomware Attacks Work?
Ransomware attacks usually start with malicious software, frequently concealed as seemingly harmless emails or downloads.
Once triggered, the ransomware locks your files, rendering them unreachable.

Ransomware exploits vulnerabilities in your systems software or your own actions, like clicking on suspicious links.
It has the ability to rapidly propagate across networks, impacting not only individuals but also businesses and institutions.
Ransomware attacks come in various forms, each with its own tricks and tactics to hold your data hostage.

Here are the most common types of ransomware attacks and their examples, prevention, and responding to them.
Encrypting Ransomware
This is a form of harmful software that uses encryption to lock your files.
These attacks commence when you unknowingly download infected attachments or visit compromised websites.

The encryption process renders your files unreadable until a ransom is given.
Its a hostage situation for your digital stuff.
It is like a digital lock that cyber criminals put on your files.

It enters into your gadget and encrypts your important documents, photos, and data.
You cant open or use them anymore.
They require payment from you in exchange for providing the key to unlock your files.

It aims to scare you into paying money to remove the supposed threats.
This ransomware messes with your mind.
It throws fake alarms and scary messages on your screen, making you think your gadget is under attack.
But heres the trick: its all fake.
The attacker wants you to pay to remove these made-up threats.
Stay cool, dont fall for the scare.
Keep your software updated and trust reliable security tools to keep you safe.
This ransomware means you are being locked out of your machine.
It takes over your machine, making everything inaccessible your files, apps, everything.
They ask you to make a payment to regain access.
It blocks your system from starting up until you pay a ransom amount.
It goes deep into your rig.
It targets a crucial part that starts up your system.
When infected, your gear wont even start.
Petya and NotPetya are examples.
Its like the digital hijacking of your gadget.
Once it sneaks in, it locks your screen or encrypts your files.
They demand payment to undo the damage.
So, protect yourself by staying updated and not clicking on suspicious links.
Dont let these attackers hold your mobile hostage.
It is like a criminal marketplace.
Cybercriminals are the ones creating ransomware and renting it out as an asset to others.
Anyone can rent it from them without being a hacker; simply pay and use it.
This spreads the threat wider.
Understand that this criminal service makes ransomware accessible to anyone, making it even more crucial to protect yourself.
So, be vigilant against phishing emails and keep your security strong.
Petya is distributed via email attachments or compromised websites.
To protect yourself from it, avoid clicking on suspicious links.
Install reliable antivirus software, use strong passwords, and explore more about online threats.
Answer:Yes, law enforcement agencies can track down ransomware attackers.
They collaborate with cybersecurity experts and use digital forensics to trace the origin of attacks.
Explore other options like restoring from backups or seeking professional help to remove the ransomware and recover your files.
Conclusion
Understanding ransomware and its potential risks is crucial for your digital security.
By remaining vigilant and proactive, you could effectively protect your digital environment from constantly evolving threats.
You may also explore thecyber attack simulationtools to improve security.