We earn commission when you buy through affiliate links.
This does not influence our reviews or recommendations.Learn more.
Port scanning is a technique to explore a web connection by checking specific ports for openness.

It helps identify potential vulnerabilities and weaknesses in a systems security.
It helps identify active services and assess the security posture of a system or internet.
Pentest-Tools is a cloud-based toolkit for offensive security testing focused on web applications and online grid penetration testing.
Pentest-Tools Pros
Offers rapid and comprehensive scanning of target networks to identify open ports and services.
Detailed reports on discovered ports, aiding in vulnerability assessment and connection hardening.
Requires some technical knowledge to use effectively.

API endpoints are available over HTTPS, ensuring secure data processing with 256-bit TLS encryption.
Developer-friendly API documentation for easy integration.
Siterelic Cons
Only available to paid users.

Siterelic Pricing
Siterelic API plans start at 10,000 API calls for $9.99 monthly.
HackerTarget Pros
Access advanced scanning capabilities with Advanced Nmap options for a thorough online grid security assessment.
Schedule daily scans and set up automated alerts to stay informed about any changes or threats in real-time.

Utilize a suite of 27 Vulnerability Scanners and IP Tools for comprehensive scanning and analysis.
HackerTarget Cons
A subscription is needed to access advanced features.
The free version only scans the common ports.
HackerTarget Pricing
HackerTarget offers two plans: Standard Plans and Enterprise Options.
The Enterprise Options are Enterprise-1 at $100 monthly and Enterprise-2 at $200 monthly.
WhatIsMyIP Cons
Advanced functionalities are available only for Gold membership users.
IPVoid offers a detailed view of open TCP ports using the Nmap port scanner for accurate and quick scans.
It can scan IPv4 and IPv6 addresses, allowing users to scan common or define custom ports.
IPVoid Pros
Offers an intuitive interface for efficient internet diagnostics.
The user-friendly design of IPVoid makes it a top choice for quick troubleshooting and analysis tasks.
IPVoid Cons
An excessive number of ads can detract from the overall user experience.
It does not support simultaneous scanning or scanning IP address ranges.
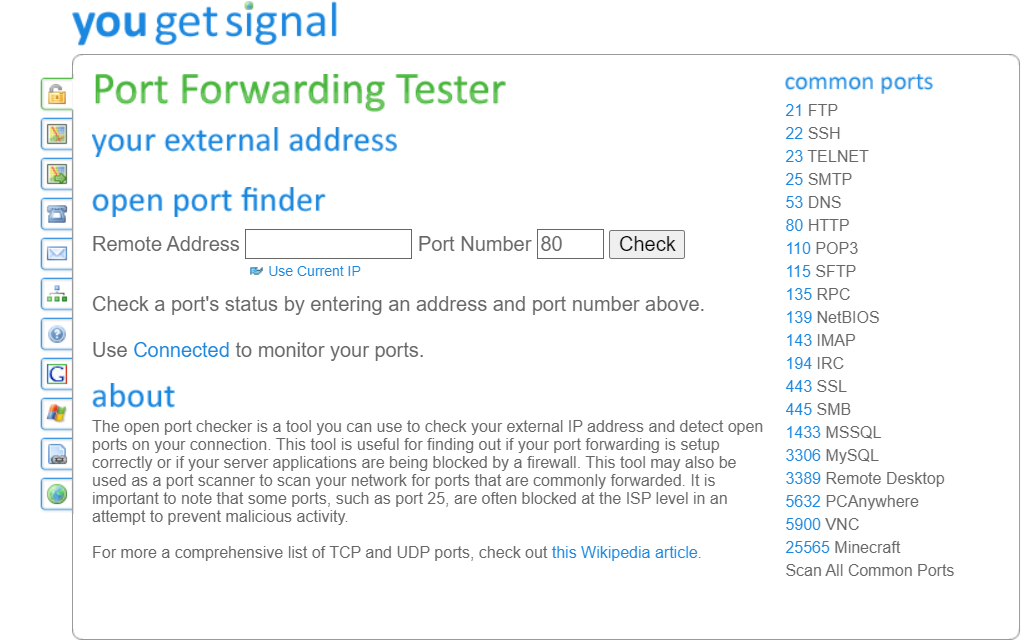
Users can verify port forwarding and performWHOIS lookupsthrough the user-friendly interface.
DNSChecker provides a free custom port scanning feature, allowing users to define their own ports for scanning.
It offers a user-friendly interface, enabling users to perform various online grid diagnostic tasks quickly and efficiently.
YouGetSignal Cons
Only one port can be scanned at a time.
Does not have advanced scanning capabilities.
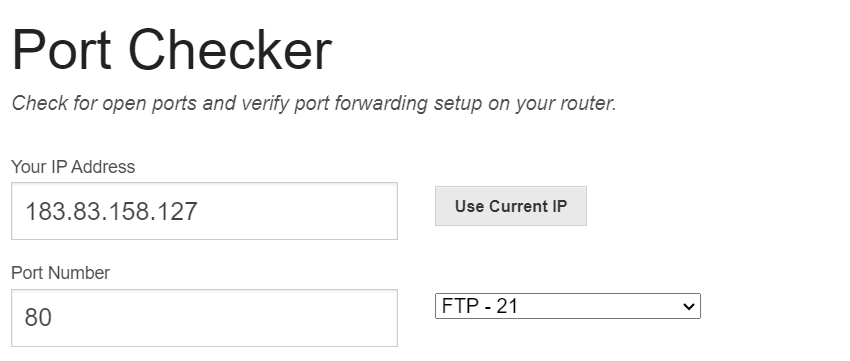
PortChecker Pros
Provides quick tests for single port checks.
Users can remain anonymous as no account is necessary.
PortChecker Cons
Limited to scanning one IP address per scan.
What is a Port Scanner?
It is used by security professionals and web link administrators toidentify web link vulnerabilitiesand troubleshoot web link issues.
Should Port Be Open or Closed?
Ports should be closed unless required, as open ports can expose systems to security risks.
Only essential ports should be opened and secured with firewalls and access controls.
Regular monitoring and updating of systems is necessary to patch vulnerabilities.
Unnecessary ports should be closed for security reasons, such as those associated with vulnerable protocols.
How Do Cyber Criminals Use Port Scanning to Prepare for Cyberattacks?
Cybercriminals frequently use port scanning during the reconnaissance stage of a cyberattack.
In this stage, they scan the web connection to identify active devices and their open ports.
This helps them gather information about running applications and potential weaknesses that could be exploited.
Port scanning aids attackers in selecting specific attack vectors and understanding how active security measures could be bypassed.
Tools like IP scanning, Nmap, and Netcat are commonly used for these tasks.