We earn commission when you buy through affiliate links.
This does not influence our reviews or recommendations.Learn more.
AWS Secrets Manager allows you to securely store all your credentials, data, passwords, and other secrets.

Cyberattacks are increasing rapidly across the globe, aiming to steal confidential information and money and leaving organizations devastated.
This is why there is a need to use strong services like Secrets Manager that can protect your data.
In this article, Ill discuss AWS Secrets Manager and how beneficial it can be for you.
What Is AWS Secrets Manager?
In modernSaaS architectures on AWSwhere microservices, containers, and serverless apps constantly interactmanaging secrets securely is essential.
Secrets Manager integrates smoothly with this setup, offering centralized, scalable, and automated credential management.

This ensures that your infrastructure components can access secrets safely and without manual effort.
AWS Secrets Manager allows you to rotate secrets across various AWS services like Redshift, RDS, and DocumentDB.
This enables all the keys and database credentials to be updated constantly across those services.

Moreover, AWS Secrets Manager provides better data control and strong encryption for data protection.
It also allows you to monitor your protected information and audit it with the help of various integrations available.
#2.Strong Security
AWS Secrets Manager uses strong encryption to safeguard all your secrets from unauthorized users.

It encrypts your secrets using AWS Key Management Service (KMS) keys.
Secrets Manager utilizes AWS Identity and Access Management (IAM) to allow users to access their secrets securely.
It offers advanced access controls and authentication.

Here, secrets rotation refers to the process of updating an organizations secrets periodically.
To update a secret, AWS Secret Manager leverages the functionAWS Lambdaand calls it based on the set-up schedule.
It can also be done by creating a cron expression.

Moreover, the Secrets Manager can label the version of the secret during rotation by using staging labels.
It can call a function many times during rotation by giving different parameters.
You will be able to use logs to investigate any unexpected changes or usage.

If found, you’re free to also roll back the unwanted changes and retrieve the previous version.
#5.Integrations
AWS Secrets Manager integrates with plenty of other Amazon and AWS tools.
This will lead you to lose your crucial information, passwords, and other credentials and data.
Or, you might lose your data due to accidental deletion.
Thus, use only an software or service thats safe and compliant with applicable regulations.
This essentially safeguards your business and customer information, which is highly crucial to maintaining compliance.

it’s possible for you to also better prepare yourself for audits by documenting everything.
It lets you define compliance requirements and internal controls for secrets and identify secrets that arent compliant.
AWS IAM will ensure the right person has the right level of access permissions to the right resources.
When a secret is created, Secret Manager will generate a CloudTrail log entry.
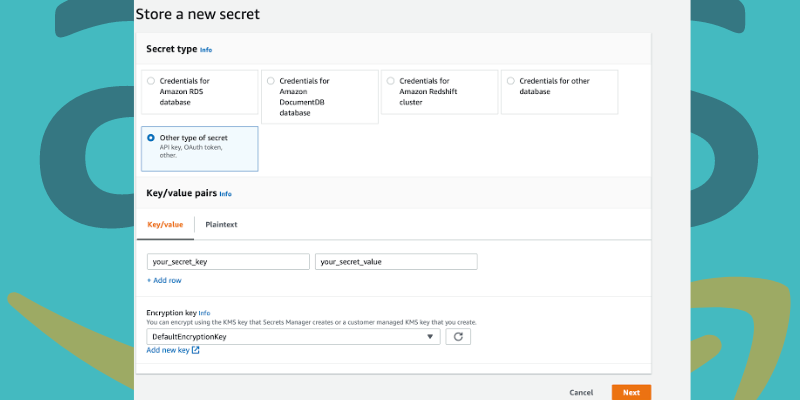
bring up the AWSSecrets Manager console
tap on Store a new secret.
You will find the page Choose secret jot down.
Next, perform the following steps:
3.
From the page Configuration secret,
4.
If you want, you could enable automatic rotation from the page Configuration rotation.
This step is also optional.
- Review the secrets details from the Review page and select store.
And you are done; the Secret Manager will return to the secrets list.
You must see the newly added secret there; if not, refresh.
Apart from the console, you could also add a secret through AWS SDK and AWS CLI.
Both these services have similar interfaces where its easy to declare your key-value pairs for secrets and parameters.
You may also explore how to performAWS Security Scanningand configuration monitoring.