We earn commission when you buy through affiliate links.
This does not influence our reviews, ranking, or recommendations.Learn more.
What is Cybersecurity?

Thus, users cannot access their files by any software.
But such attacks have no guarantee of recovery of data even after paying the ransom.
Botnets Attacks
Botnets were initially designed to carry out specific tasks within a group.
Through this attack, the hackers can control many devices and compromise them for their evil motives.
Along with financial losses, Social engineering attacks can download other destructive threats to the concerned system.
Cryptocurrency Hijacking
Cryptocurrency hijacking is the new addition to this cyber world.
As digital currency and mining are becoming popular, so it is among cybercriminals.
Cryptocurrency investors and traders are the soft targets for this attack.
Cryptocurrency hijacking is also known as Cryptojacking.
It is a program designed to inject mining codes silently into the system.
To avoid this, you should learn more about phishing email campaigns and their preventive measures.
One can also use email filtering technologies to avoid this attack.
This attack leverages the trust between business partners, and hence, it is difficult to defend.
Zero-day Attacks
These attacks exploit vulnerabilities in software that the software vendor is unaware of.
Zero-day attacks are often used by sophisticated attackers targeting high-value targets like government agencies or critical infrastructure.
These disrupt online services, causing financial losses and reputational damage.
Eavesdropping
Eavesdropping involves secretly listening to phone calls or intercepting e-communications, such as emails or DMs.
Eavesdroppers use various techniques to capture confidential information that they utilize for identity theft or other fraudulent activities.
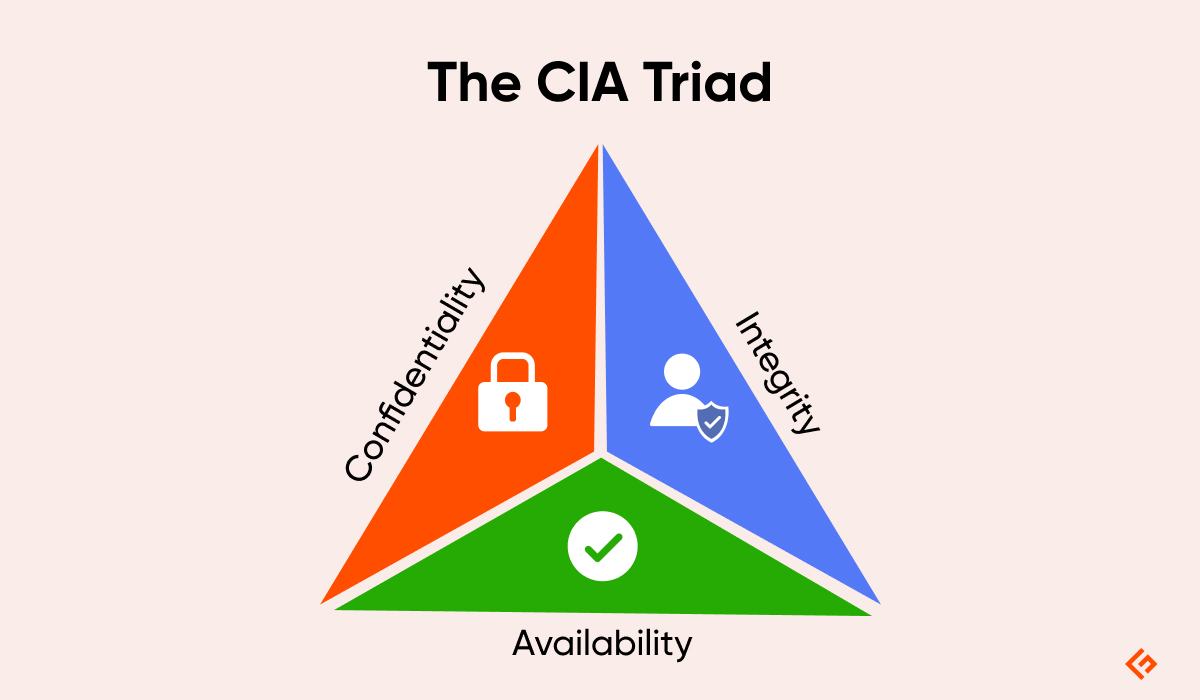
It consists ofConfidentiality,Integrity, andAvailability.
This model is designed to guide the organization with the policies of Cybersecurity in the realm of Information security.
Confidentiality
It defines the rules that limit access to information.
Confidentiality takes on the measures to restrict sensitive information from being accessed by cyberattackers and hackers.
They are also given proper training about the sharing of information and securing their accounts with strong passwords.
They can change the way data is handled within an organization to ensure data protection.
Integrity
This assures that the data is consistent, accurate, and trustworthy over its period.
Proper measures should be taken in an organization to ensure its safety.
File permissions and user access control are the measures controlling the data breach.
Furthermore, tools and technologies should be implemented to detect any change or a breach in the data.
Various organizations use a checksum and even cryptographic checksum to verify the integrity of data.
To cope with data loss or accidental deletion, or even cyberattacks, regular backups should be there.
Cloud backups are now the most trusted solution for this.
This will ensure the smooth functioning and access of Data without any disruption.
Also, providing constant communication between the components through providing enough bandwidth.
It also involves opting for extra security equipment in case of any disaster or bottlenecks.
What is Vulnerability Management?
Vulnerability management is the process that identifies, prioritizes, and addresses flaws in computer systems and software.
Vulnerability management constantly searches for these vulnerabilities, assesses their severity, and patches or fixes them.
Thus, businesses can protect themselves from cyberattacks.
All technology-based organizations need this to proactively prevent security incidents.
Tools perform automated scans to compare systems to the databases of known weaknesses.
After the assessment, organizations set their priorities and create a plan to address the risks.
The plan usually involves patching software, implementing security configurations, and isolating vulnerable systems.
Once the actions are done successfully, the whole process starts from the beginning.
Effective vulnerability management helps companies prevent these costly incidents.
It attracts clients and partners who value strong security posture and data protection.
Vulnerability and Threat Detection Solutions
Web Penetration Testing Tools
Metasploit, Indusface, Tenable Nessus, …
Vulnerability Management Software
Tenable Nessus, Rapid7 InsightVM, Heimdal, …
Managed Detection and Response Solutions
Cybereason MDR, Heimdal, Sophos MDR, …
Monitoring is the security approach of constantly watching the IT systems of an organization.
Once it identifies any anomaly, users can stop the threats before they cause any damage.
Monitoring software plays a key role in monitoring security by automatically collecting data and checking it against predefined criteria.
Whenever it detects something abnormal, it alerts the responsible person of a potential issue.
Hence, organizations can take proactive intervention before the problems impact the users or become a severe issue.
Continuous monitoring is essential for smooth organizational operation and data-driven decisions.
In such cases, organizations have to bear with less operational costs and loss of productivity.
It attracts clients and partners who prioritize a mature security culture and continuous system monitoring.
Security is also integrated throughout the development process after identifying weaknesses with testing tools scanning.
Combining all these strategies, web software security creates a strong defense against cyber threats.
If companies fail to comply with these, there will be legal repercussions, such as fines and penalties.
Robust web program security minimizes the risk of cyberattacks and these associated costs.
By securing web applications, organizations strengthen their entire security infrastructure.
web link security is the defense system that protects a web link and its data.
This approach safeguards the connection from unauthorized access, disruptions, misuse, alteration, or destruction.
The first line of defense is firewalls that filter incoming and outgoing traffic based on configured security rules.
Encryption makes data unintelligible to anyone without the decryption key.
web connection security software constantly screens data to fight malware and other threats.
Together, all these online grid security methods create a flawless defense against ever-evolving cyber threats.
Hackers can steal customer data by breaching the connection, affecting numerous people.
Businesses face hefty fines as they fail to safeguard the data.
For this reason, online grid security is vital for businesses.
This benefits eCommerce companies, financial organizations, and businesses handling sensitive user data.
It enables users to focus on their tasks without any worry.
Thus, companies can avoid penalties and other legal repercussions associated with data breaches.
Data recovery is the process of getting back information from a storage gadget.
This approach is used when data is deleted, corrupted, damaged, or formatted.
How Does Data Recovery Work
The data recovery process involves two major techniques for information retrieval.
For hardware problems or any physical damage to storage devices, data recovery demands physical intervention.
Loss of such data leads to operational downtime and financial setbacks.
When users know that they have a data recovery plan in place, they get peace of mind.
When a business has a data recovery plan, it maintains a competitive edge over the competitors.
Antivirus software protects devices and systems from viruses, malware, Trojan, and many more.
These malicious elements infect a computer through downloads, email attachments, or even clicks on links.
Antivirus software constantly monitors to stop these from entering or using the unit.
Besides identifying and blocking known threats, it detects suspicious activity.
Antivirus applications have a large database of known malware signatures or unique identifiers.
The antivirus software compares it to these signatures to see if there is a match.
It flags any such suspicious activities for investigation or stops it.
In most cases, antivirus software uses these two methods to offer layered defense against evolving online threats.
It safeguards user devices from malware, such as spyware, ransomware, worms, and trojanware.
Keeping it without any antivirus software means leaving the system vulnerable to all kinds of hackers and cybercriminals.
Spam emails can contain phishing links and malware to trick users into giving away their personal information.
Most antivirus programs automatically install updates to enrich their databases with the knowledge of the latest threats.
Antivirus software prevents malware from infecting the computer to keep the system running smoothly.
Moreover, users do not have to install separate software for parental control.
User privacy in cyberspace is a complicated issue.
Maintaining privacy also involves the ability to choose what you want to share with the world.
Privacy ensures the autonomy and safety of the user, both online and offline.
With technological advancement, privacy has become a more complex concept.
How Does Privacy Work
Privacy in the digital world is an ongoing conversation.
They must implement strong security and comply with data privacy regulations around the world.
Governments of different countries should have laws and regulations like GDPR that give users more control over their data.
Thus, they have autonomy over their personal data.
They can also express themselves without any fear of judgment or surveillance.
Publicly sharing location data can make users vulnerable to stalking, leading to physical and emotional harm.
A degree of privacy allows them to do so without fear of immediate public exposure or criticism.
Privacy allows them a second chance and the freedom to move on from experiences.
What is Endpoint Security?
Hackers can easily use these devices as entry points to infiltrate a web link.
Endpoint security protects these endpoints from threats such as malware, phishing attacks, and unauthorized access.
In this method, companies usually install software to constantly monitor the activity of these devices.
With effective endpoint security, companies can prevent these disruptions and continue smooth operations.
IT teams can customize security policies for different user groups or unit categories.
Modern endpoint security solutions leverage threat intelligence feeds and machine learning to discover emerging threats and zero-day attacks.
Password management is the practice of securely storing and creating passwords for all your online accounts.
Remembering countless unique passwords is difficult, and reusing the same password across several sites poses a security risk.
Password management resolves all these issues.
These programs function as a secure vault where all the passwords and login credentials of different websites are stored.
Most of these applications offer an autofill feature, which automatically enters the login information on websites and apps.
Thus, it saves time and frustration for the users.
Besides passwords, some applications securely store notes and financial details.
Hence, they resort to using the same password for multiple accounts.
If the password of one account gets compromised, all other accounts become susceptible to hacking.
Password managers securely store the login credentials and free users from remembering them.
These offer an extra defense layer against cyberattacks by warning users about suspicious activities and websites.
Password managers ensure secure credential sharing, allowing employees access without compromising their passwords.
Authentication, Identity, and Access Management
Passwordless Authentication Solution
Okta, Authsignal, FusionAuth, … Cybersecurity utilizes a multi-layered approach that involves both prevention and response strategies.
This continuous process requires constant vigilance and adaptation to stay one step ahead of evolving threats.
Cybersecurity Protection
Cybersecurity Response
What Are Technologies Used in Cybersecurity?
Cybersecurity relies on a diverse range of technologies to defend against ever-evolving threats.
Is There a Job for Cybersecurity?
Yes, there are many jobs in cybersecurity.
This booming demand results in a wealth of cybersecurity jobs catering to individuals with various backgrounds and skill sets.
Most organizations actively recruit cybersecurity professionals to strengthen their defenses and protect vital data and systems from cyber-attacks.
How Does Cybersecurity Differ from Traditional Security Measures?
Traditional security protects physical or tangible assets through physical barriers and access control.
On the other hand, cybersecurity protects digital information, systems, and networks from cyberattacks.
Here is a breakdown of the key differences between traditional security and cybersecurity.
What Are Some Common Misconceptions about Cybersecurity?
The business world is full of misconceptions about cybersecurity.
The following list includes the most common myths that can lead to business risk.
What is the Role of Cybersecurity in Information Technology?
While IT is an indispensable part of todays digital world, it comes with a growing risk for cyberattacks.
The role of cybersecurity is highly critical in information technology (IT).
Lets explore how cybersecurity safeguards IT.
A data breach can lead to financial losses, reputational damage, and even legal repercussions.
Cybersecurity shields this data from unauthorized access, theft, or corruption.
Ensure System Availability
Cyberattacks often disrupt IT systems by preventing users from accessing critical applications and data.
Such outage cripples business operations and team productivity.
Cybersecurity approaches like firewalls and intrusion detection systems stop these attacks from happening and keep these systems available.
Maintain Data Integrity
Malicious elements tamper with IT systems to manipulate data or disrupt regular operations.
Cybersecurity ensures data integrity by protecting systems from unauthorized modifications.
This role is important for finance and healthcare industries, where the value of data accuracy is paramount.
Build Trust
Strong cybersecurity means the organization is committed to protecting sensitive information.
It builds trust with customers, partners, and investors while maintaining a good reputation.
Data empowers organizations to make informed decisions at every level of operations.
It does so by revealing trends, customer behavior, and room for improvement.
Furthermore, data analysis streamlines automated tasks and identifies cost-saving opportunities.
Ultimately, data acts as a starting point for innovation.
What Is Cybersecurity Mesh?
This approach is different from the traditional perimeter-based defense that builds a single wall around the entire data pipe.
In cybersecurity mesh, all controls communicate with each other to share threat intelligence.
Thus, organizations get a more dynamic and adaptable security framework.
Even if any part of the mesh is compromised, the others continue to function and limit the damage.
Cybersecurity mesh is most appropriate for modern, cloud-based environments where data and applications are located in different locations.
What are AI-Powered Cybersecurity Platforms That Can Be Integrated to Your Organization?
Organizations can integrate these AI cybersecurity platforms to protect data, applications, and services against cyberattacks.
What is the Difference Between Cybersecurity and Cyber Resilience?
Cybersecurity and cyber resilience focus on different stages of a cyberattack.
Cybersecurity utilizes relevant tools and best practices, like firewalls and encryption, to actively defend systems and data.
Unlike traditional cybersecurity, cyber resilience takes a broader approach.