We earn commission when you buy through affiliate links.
This does not influence our reviews or recommendations.Learn more.
Did you lately get an email from your CEO asking to transfer money to a vendor?

Its a CEO fraud or whaling phishing fraud.
Whaling phishing is a punch in of cyber-based attack where CEOs and senior executives are targets.
I have also highlightedhow to prevent whaling phishing fraud, after all, awareness is key!

Lets start this with a little background story.
CEO Fraud happened to me almost two months after I joined Geekflare as a full-time writer.
So, I responded to the initial I would like to assign you a task, are you free?
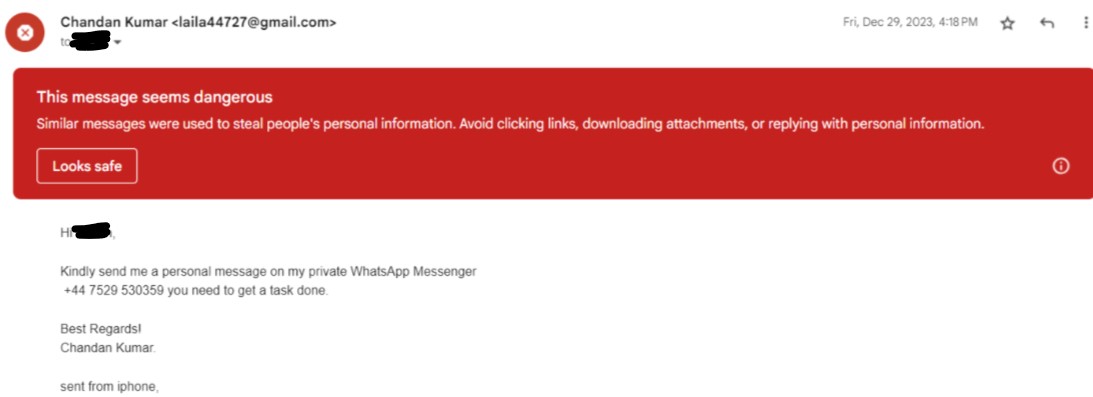
But we shouldnt rely on sheer luck; instead, know this upfront and educate others.
What is CEO Fraud or Whaling Phishing?
Email scams accounted for nearly $2.4 billion in losses in 2021, per the FBI Internet Crime Report.

, which accounted for nearly $2.4 billion in losses in 2021, per thisInternet Crime Report.
How Does Whaling Phishing Work?
Notably, CEO fraud doesnt need any technical skills or criminal know-how.

Lets check out a few ways bad actors do this currently.
And this one is easy to spot.
All you have to look for is the email address (and not the name).
Generally, the domain name (xyz@companyname.com) gives away fraud.
However, the email address may indicate a renowned organization (as it was in my case).
Heres a more obviously engineered example.
These awards added legitimacy to the scam, which may victimize an uninformed professional.
key in 2
Another more sophisticated technique uses video calls.
In this case, an organizations client gets an email to pay an invoice to specific bank accounts urgently.
This one has the highest success rate as its normally pulled off using a hacked company email address.
This psyche is the prime cause of perpetrators getting success easily with just a random email.
In addition to questioning financial requests, its best to ask for a video meeting before cooperating.
Moreover, in most cases, you just need to check the email address carefully.
This may not belong to your organization or may have misspelled versions of the company name.
Besides, an institution cant register all domain extensions.
So, you oughta beware of getting an email fromxyz@company.netwhen the official address should bexyz@company.com.
Lastly, you might be receiving emails from a company address operated from outside or a rogue internal member.
Because these fraudsters constantly evolve.
So, giving a single, one-time warning wont help your employees much.
Wrapping Up!
Unfortunately, we depend heavily on business emails, leaving big loopholes criminals often exploit.
This will help quickly confirm if anything seems suspicious and avoid such setbacks.
PS: If I were you, I would not miss this article coveringtypes of cybercrimesfor added internet literacy.