We earn commission when you buy through affiliate links.
This does not influence our reviews or recommendations.Learn more.
you’re able to do some crazy hacking stuff just by searching on Google!
Yes, you heard that right.
It is called Google Hacking or Google Dorking.
As a content writer, I have used Google Dorks several times for SEO and research purposes.

It helps me find specific posts from my competitors and lock down underserved topics for my content strategy.
Similarly, you might use the Google Dorking commands as per your requirement.
Also, you should probably know where to draw the line.
Google Dorking is not illegal as long as the information collected is used for research purposes.
And Google doesnt like that.
It even penalizes the IP address from where the Dorking commands are coming.

And you could face a criminal charge, too, so beware.
What is Google Dorking?
Google Dorking is a search technique to find information not generally shown in Google search results.
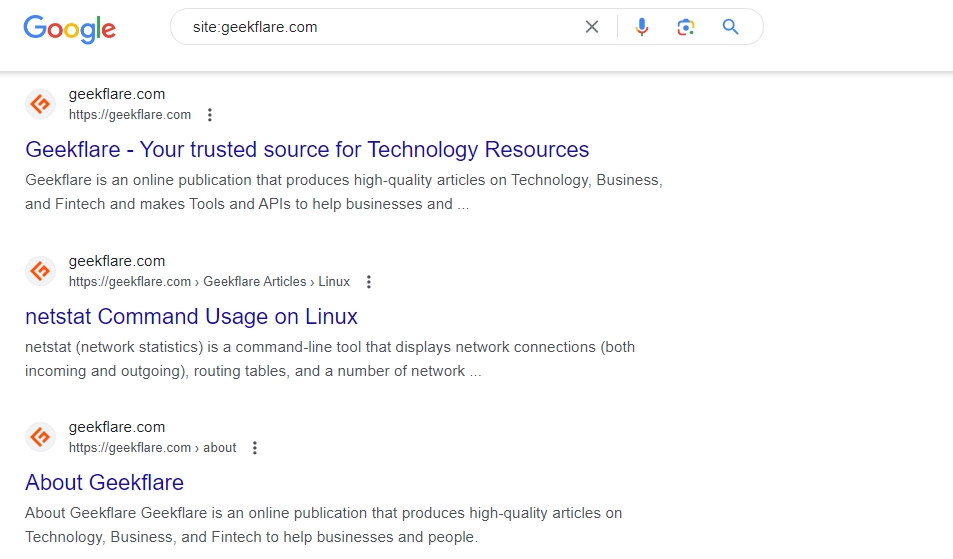
It is done using advanced search operators and strings called dorks.
How Google Dorking Works?
Individuals like you and me can use Google Dorking for research purposes.
However, it is mostly used by cybersecurity experts to understand the loopholes in the system.
These are mostlyethical hackers, also known as white-hat hackers.
Evenblack-hat hackersuse Google Dorking to identify websites with security vulnerabilities.

They find sensitive data and files about their targets and use them maliciously.
Robot fan, anyone? )
Since the early 2000s, search engines have been used as a tool for Google Dorking.

And Googles widespread web crawling capabilities facilitate Dorking.
This means businesses are targeted almost every day.
Hackers may also sell this data to other criminals on the dark web for large sums of money.

From confidential documents to usernames and passwords, all the hackers can find.
This stage is also known as recon, footprinting, or even fingerprinting.
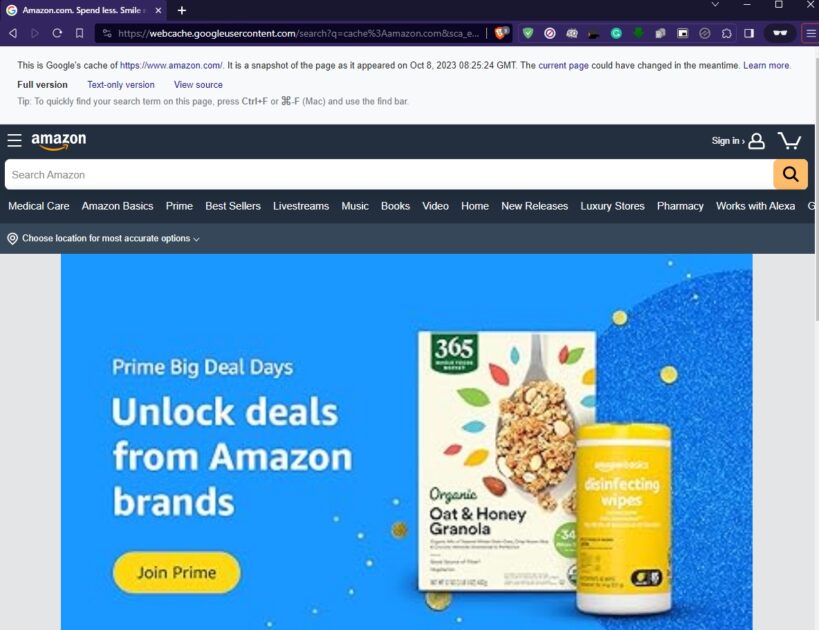
Google Dorking is a way ofpassive recon, meaning hackers access publicly available files online.
The publicly available files could be accidentally made online.
The hacker removes all exploits and back doors and clears the logs.
Beyond this phase, you may be accountable for computer crimes punishable by law.

So, click with caution and good faith.
I use some of these Google Dork queries such as allintitle, inurl, filetype, etc.
all the time when doingSERP analysisfor a topic.
This helps me put down the exact content strategy for that particular topic.
I will share some of the most common and useful Google Dork queries.
I will share the querys function, results, and how to use the findings to your advantage.
Here are some of the most common operators used in Google Dorking.
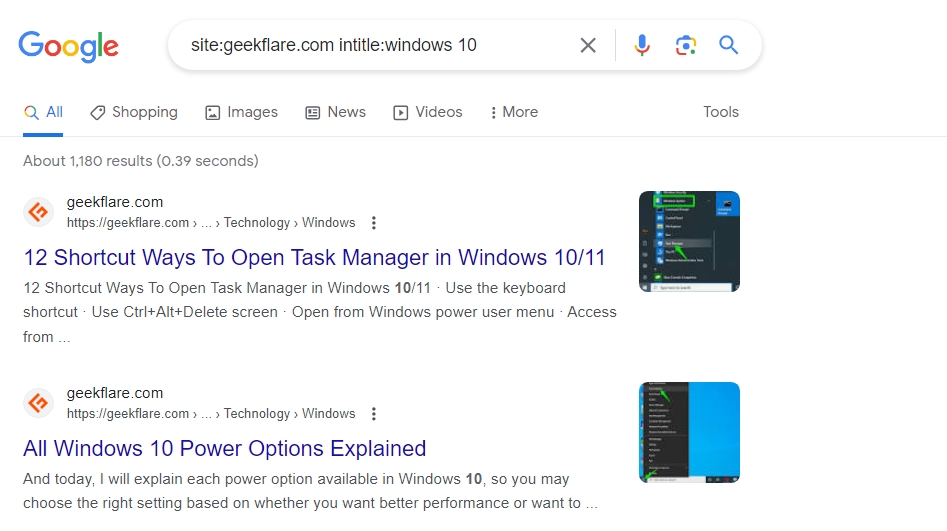
This query restricts your search to a particular website, top-level domain, or subdomain.
This query will show you the public web pages of that particular website, top-level domain, or subdomain.

you’re able to even combine it with site: query to get even specific results.
This Google Dorking method is really useful when you want to find results around a specific search term.
If you combine it with other queries, it’s possible for you to drastically improve your SERP analysis.

Then, you’re able to use allintitle: query instead of intitle:.
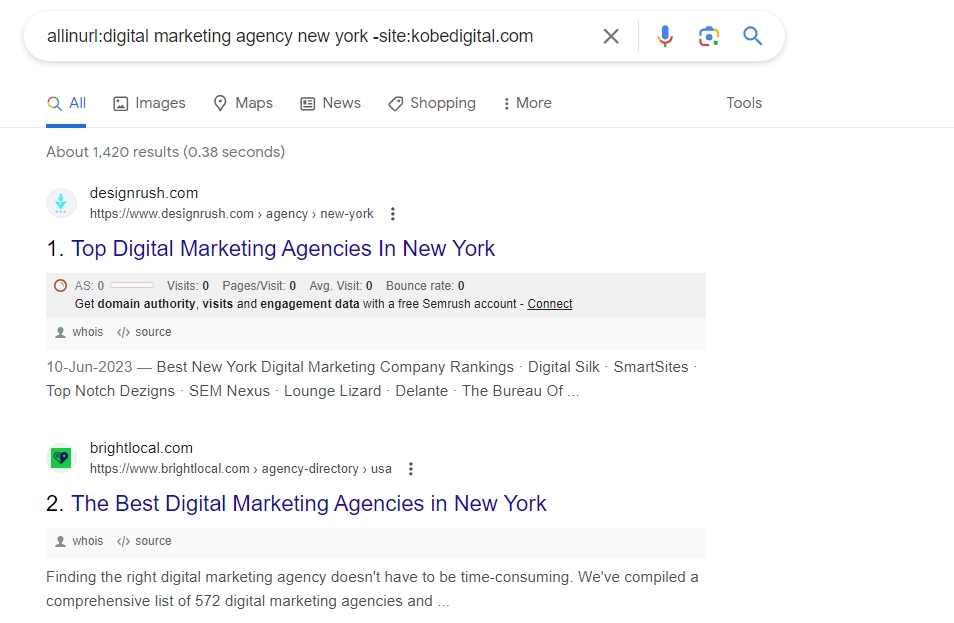
#3.Inurl/Allinurl
The inurl: dork command is very similar to intitle: command.
The only difference is that this query looks for a particular search term in the URLs of the websites.
This query will give you URLs with all the search terms present in it.
you might even include an additional operator like - (minus) to exclude results from a particular source.
you could do the same with allintitle: query.
#4.Intext
The intext: Dork query finds websites/webpages with the search term in their texts.
It is really useful for SEO experts tofind competitors web pageswith the search term a certain keyword.
It is one of the Google search tricks that most SEO experts use.
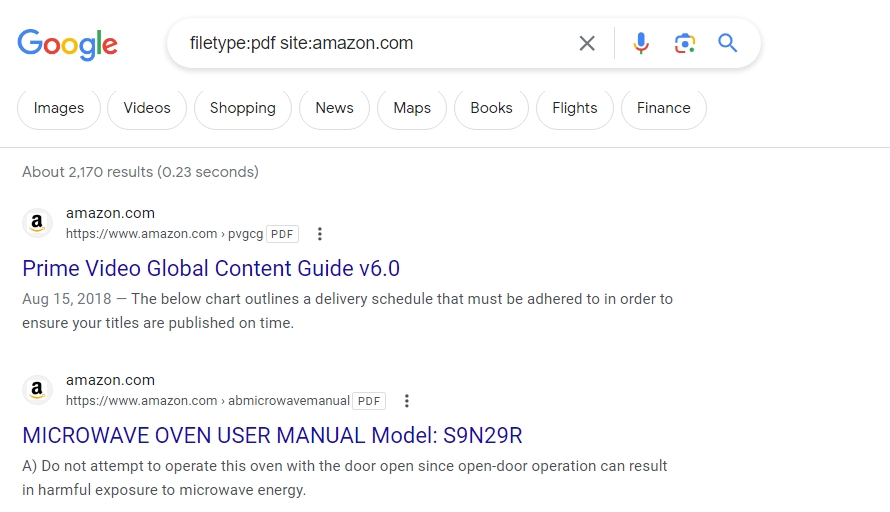
This search query is extremely useful if you are looking for specific reports, manuals, or studies.
These documents might contain sensitive information such as IP addresses, passwords, etc.
Hackers use this information forpenetration testing(pentesting) and to bypass paywalls to access resources.
Its useful for rediscovering a website before its downtime or latest update.
#8.Map
Using the map: Dorking command lets you find a map of the given location.
Google Search will show you the map directly instead of the web pages.
On macOS, you may see a prompt to kick off the Maps utility.
This query is useful to find a particular locations map quickly.
How to Protect Yourself from Google Dorking?
Whether youre an individual or a business, you must protect yourself from Google Dorking.
you could take the following steps to ensure that your data on the internet is safe.
However, if used unethically, it can gather the attention of law enforcement authorities.
Most of the time, Google will warn you when you overdo the Dorking.
It will start verifying your search queries.
If you still go overboard, Google can even ban your IP address.
To Dork or Not to Dork?
Forpenetration testers, its their everyday job.
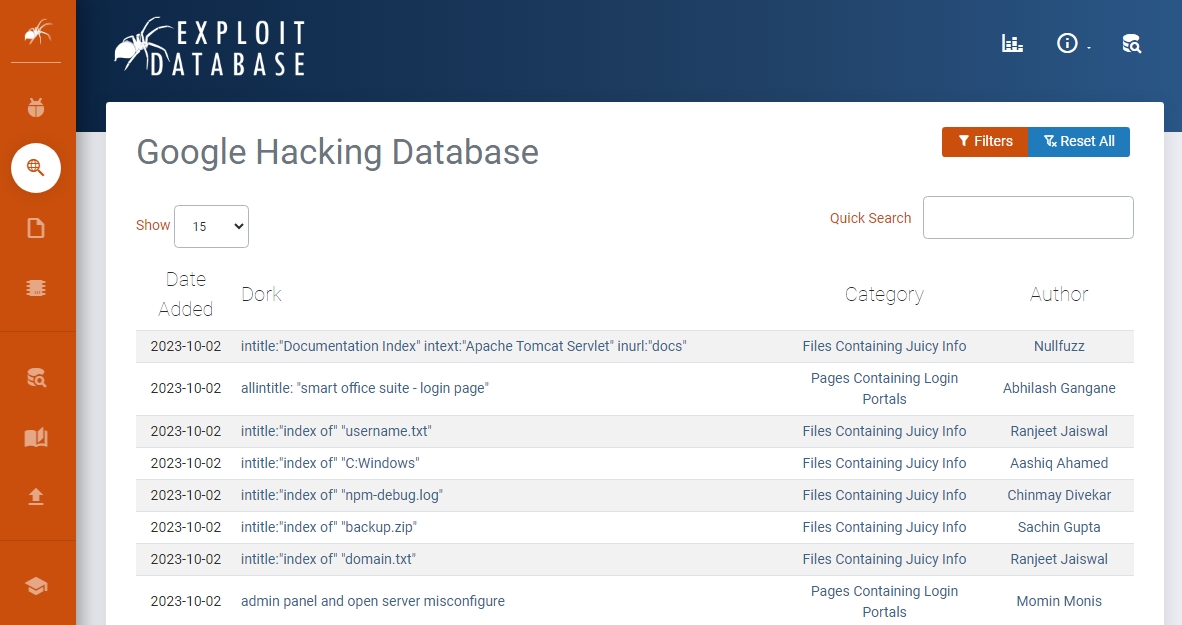
Also, with the Google Hacking Database, you get a collection of pre-made Google Dorks.
However, Id again like to remind you to use Dorking ethically and with permission.