We earn commission when you buy through affiliate links.
This does not influence our reviews or recommendations.Learn more.
Have you ever thought of outplaying hackers in their own game?

Or perhaps you are tired of defending against bad tech guys.
In either case, it is time to consider using honeypots and honeynets.
When talking about honeypots, you refer to specially designed computer systems that lure attackers and record their moves.

Think of this as an intelligence collection system.
Currently, there are over 1.6 million sites today.
Hackers continuously scan through internet addresses for poorly protected systems.

A honeypot is a deliberately vulnerable possiblehackerdestination invoking penetration yet fully instrumented.
This article builds on honeypots and honeynets, diving into its core to educate you on this cybersecurity domain.
By the end, you should have a solid understanding of the area and its role in security.
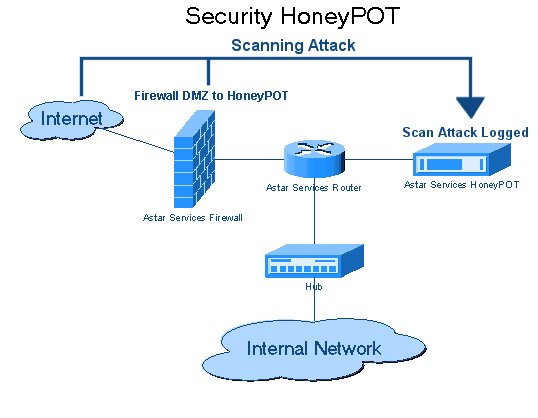
Honeypots aim to deceive the attacker and learn their behavior to improve your security policies.
What Is a Honeypot?
A honeypot is a security mechanism used to set traps for attackers.

So, you intentionally compromise a computer system to allow the hacker to exploit security vulnerabilities.
Your organizations security team can use honeypots to investigate cybersecurity breaches gathering intel on how cybercrime is conducted.
Unlike traditional cybersecurity measures that attract legitimate activity, honeypots reduce the risk of false positives.

Honeypots vary from one design to another.
However, they will all narrow down to looking legitimate, vulnerable, and attracting cybercriminals.
Why Do You Need Honeypots?
Honeypots in cybersecurity have two primary uses, research and production.
Honeypots are efficient and cost-saving.
Honeypots Designs
Honeypots are classified according to their aims and levels of interaction.
Next, we will explore types of honeypots.
Here is a breakdown of the available models.
#1.Email Traps
Alternatively known as spam traps.
This key in places fake email addresses in a hidden location where only automated address harvesters can find them.
you’ve got the option to analyze the malware characteristics to develop anti-malwaresoftware or address vulnerable API endpoints.
Honeypots can also be viewed in another dimension based on interaction levels.
Heres a breakdown:
How Do Honeypots Work?
In other cases, your honeypot may take after a database with dummy trade secrets or valuable information.
And whether you use compromised information or photos, the idea is to lure attackers interested in collecting intel.
This knowledge is then used to improve the overall defenses strengthening the online grid.
To lure a hacker into your system, you must create some vulnerabilities they can exploit.
you could achieve this by exposing vulnerable ports that provide access to your system.
Unfortunately, hackers are also smart enough to identify honeypots diverting them from real targets.
To ensure your trap works, you must build an attractive honeypot that draws attention while seeming authentic.
There is also an associated risk.
If the attacker successfully exploits the honeypot, they could proceed to hack your entire production connection.
Your honeypot must be successfully isolated to prevent the risk of exploiting your production systems.
As an improved solution, you could combine honeypots with other technologies to scale your security operations.
Advantages of Honeypot
Next, we will explore some of the disadvantages of Honeypot.
Disadvantages of Honeypot
Now, explore the dangers of Honeypots.
A threat may exist, yet not directed to the honeypot.
This operation model leaves you with another responsibility to monitor other system parts.
In successful honeypot operations, honeypots deceive hackers that they have accessed the central system.
However, if they identify its honeypots, they could avert to your real system leaving the traps untouched.
Honeypots vs. Cyber Deception
The cybersecurity industry often uses honeypot and cyber deception interchangeably.
However, there is a key difference between the two domains.
As you have seen, honeypots are designed to lure attackers for security reasons.
With many companies working with digital products, security professionals spend significant time keeping their systems attack free.
you could imagine having built a robust, safe, and reliable connection for your company.
However, can you be sure that the system cannot be breached?
Are there weak points?
Would an outsider get in, and if they did, what would happen next?
Worry no more; honeynets are the answer.
What Are Honeynets?
Honeynets are decoy networks containing collections of honeypots in a highly monitored web link.
For instance, you’re able to have windows, a Mac, and a Linux honeypot machine.
Why Do You Need Honeynets?
Honeynets come as honeypots with advanced value-added features.
it’s possible for you to use honeynets to:
How Do Honeynets Work?
If you want to build a realistic hacker trap, you agree it isnt a walk in the park.
Honeynets rely on a series of elements that work together seamlessly.
You have also learned about honeypot types and designs and their roles in the business niche.
You are also aware of the benefits and associated risks.
If you are wondering which overpowers the other, the valuable part is the greater one.
Now, check out theintroduction to cyber securitybasics for beginners.