We earn commission when you buy through affiliate links.
This does not influence our reviews or recommendations.Learn more.
Operating systems like Debian and Ubuntu are also commonly utilized for these purposes.
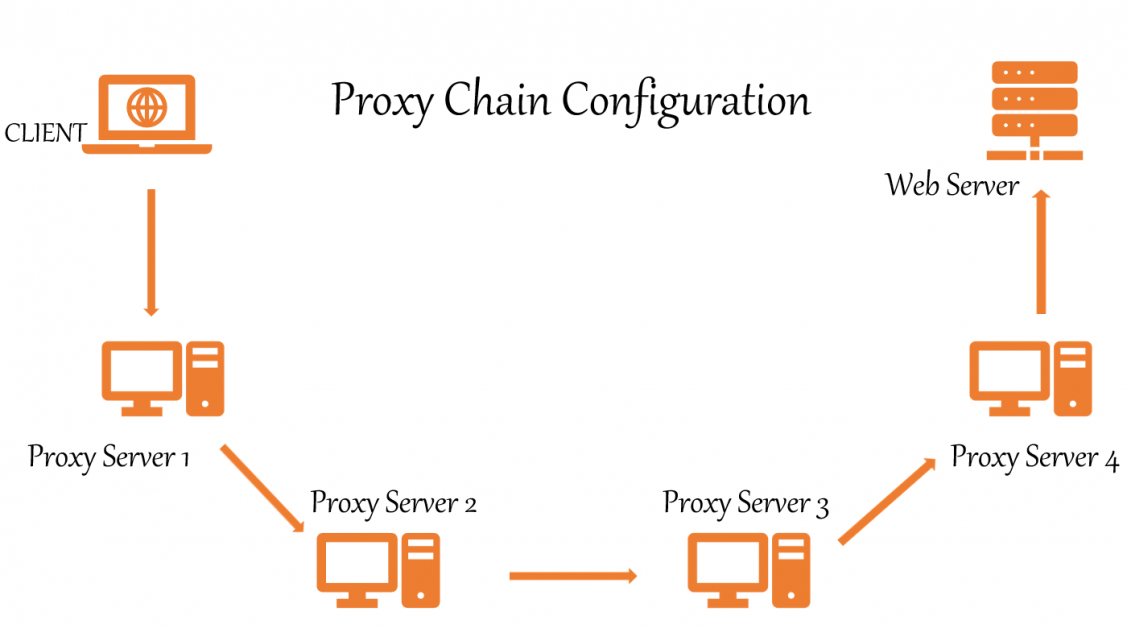
As a result, ProxyChains hides your genuine IP address by using many proxy servers.
Remember that the more proxies you use, the slower your Internet connection will become.
What are ProxyChains?

Proxychains is a UNIX program that allows us to mask our IP address by redirecting data pipe traffic.
It routes our TCP traffic through a variety of proxies, including TOR,SOCKS, and HTTP.
Proxy chaining is simple and may be accomplished by anyone, as demonstrated in this article.

This guide will show you how to set up Tor and Proxychains on Linux for anonymity.
In our case, its going to be 9050 and thats the default with the tor service.
Based on the above result, we can notice that the ProxyChain config file is located in /etc/.

We need to make some adjustments to ProxyChains configuration files.
launch the config file in your favorite text editor like leafpad, vim, or nano.
Here I am using nano editor.
The config file is opened.
#1.Dynamic chain should be removed from the remark comment.
All you have to do is to remove a # in front of dynamic_chain.
Put the comment in front of random_chain and strict_chain.
Just add # in front of these.
#3.Max times it includes the proxy-DNS uncomment, double-check that it is uncommented.
You will avoid anyDNSleaks that may reveal your true IP address in this manner.
#4.Add socks5 127.0.0.1 9050 in the proxy list the last line.
Here socks4 proxy will be already given.
you should probably add the socks5 proxy as shown above.
And finally, save the config file and exit the terminal.
Its great, right?
After running ProxyChains, you will notice that Firefox has been loaded with a different language.
In the DNS leak test, youll see a variety of outcomes, as illustrated below.
Again you’ve got the option to see that my location has shifted from Pakistan to Russia.
This is how dynamic chain proxies work.
It increases the chances for more anonymity while hacking.
Conclusion
We learned how to remain anonymous on the internet and protect our online privacy while pentesting.