We earn commission when you buy through affiliate links.
This does not influence our reviews or recommendations.Learn more.
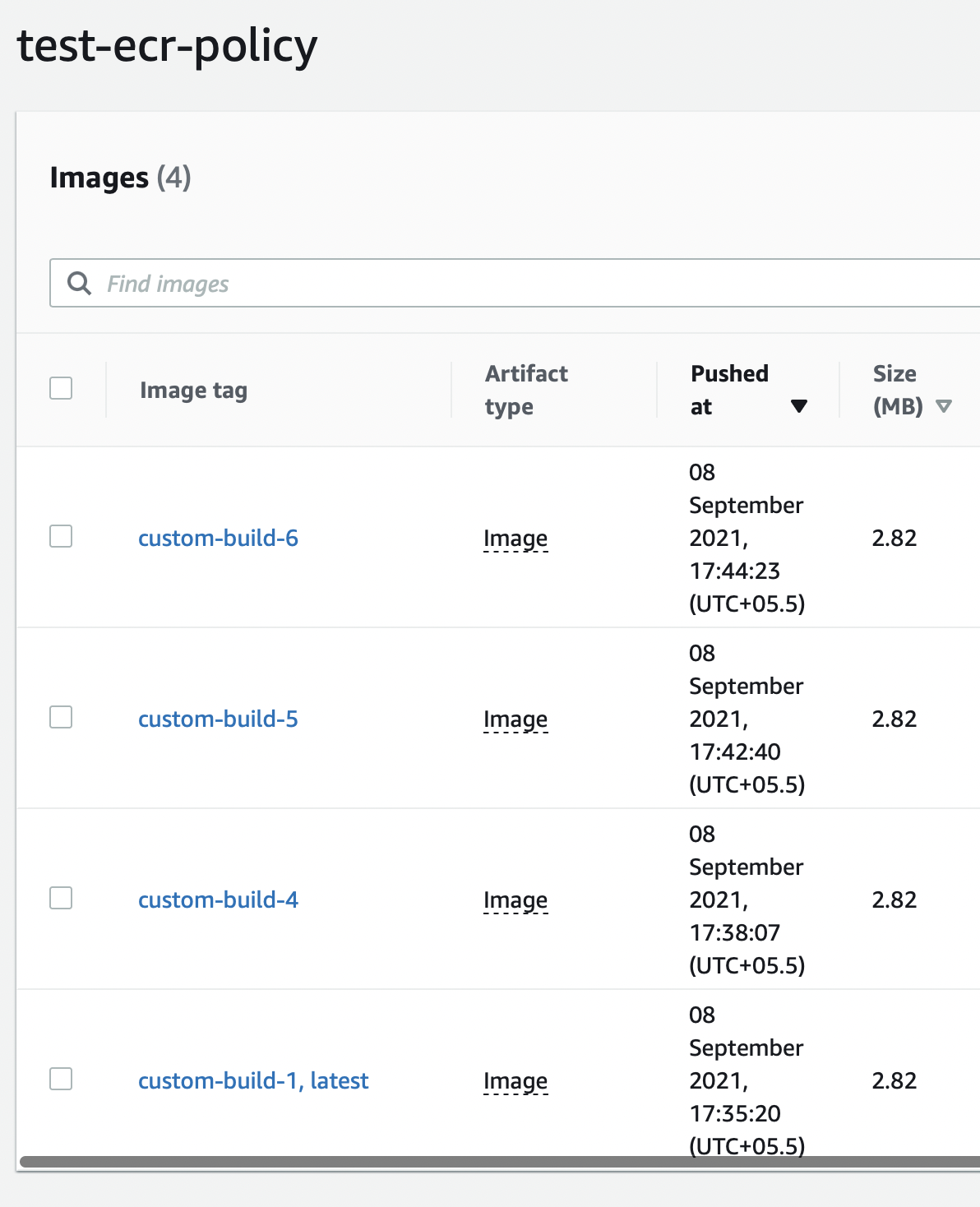
Its important to delete untagged and old images to maintain hygiene.
Today, applications run asmicro-service.
Containers are designed from a read-only template called an image.
These images need to be stored somewhere so they can be retrieved by any machine authorized to use them.
Thats where a container registry comes in.
Not long ago, folks used DockerHub to store these images and artifacts.
Every day, multiple AWS-hosted applications push and pull millions of images/system artifacts into/out of specific ECR repositories.
The Need: Delete Untagged and Old Images Now!
The primary reason for cleaning ECR repositories is development hygiene.
At any time, no one would want to keep images older than ten deployments in their ECRs.
In simpler terms, any image/artifacts more than five deployments old are useless.
Across the industry, tagging is used to specify the most stable latest or last five latest images.
In situations like this, where images/artifacts are large, it will also add storage charges on ECR.
This price might look small to you, but as they say, drops make up the ocean.
Why keep it and pay for it?
Deleting AWS ECR Images Manually
Method 1: The GUI Way!
The other tags that you see can be called untagged.
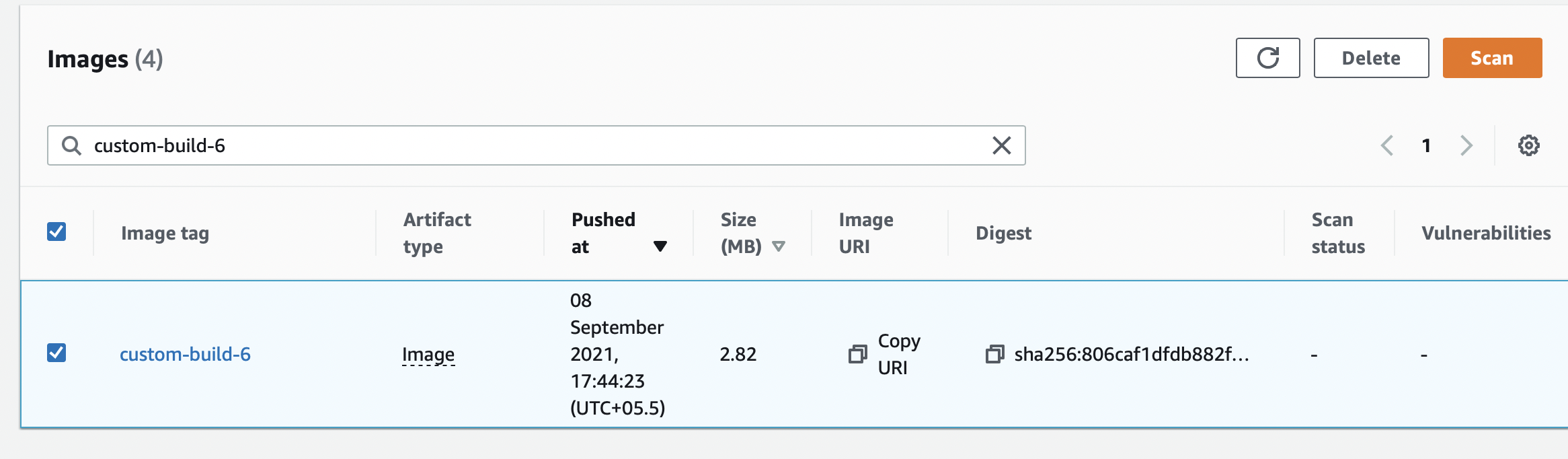
To delete, we just need to snag the image and click delete.
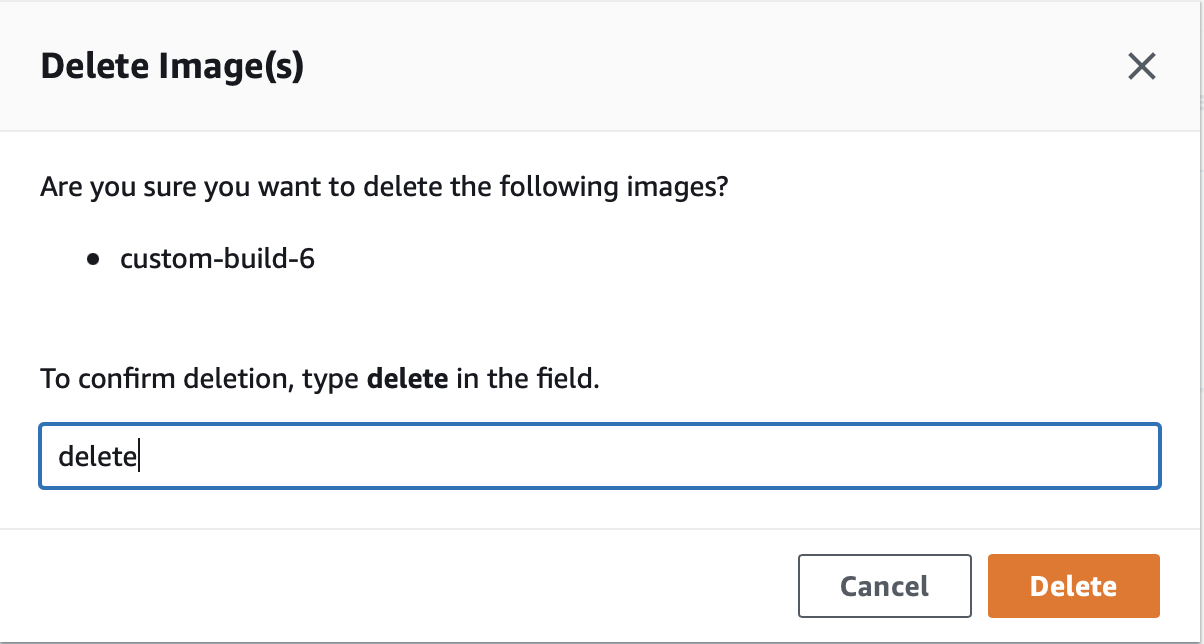
Step 3: Confirm to Delete
Method 2: The CLI Way!
In this case, we have already configured it.
you’re able to do it from theAWS configuration basics guideif you havent already.
If unsure that you have configured AWS CLI on your machine, use the following command to verify.
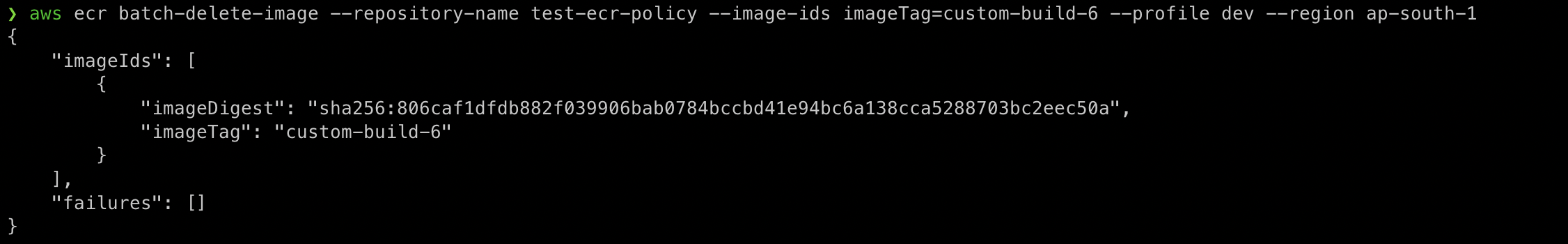
Here we are doing something similar to what we did in the GUI.
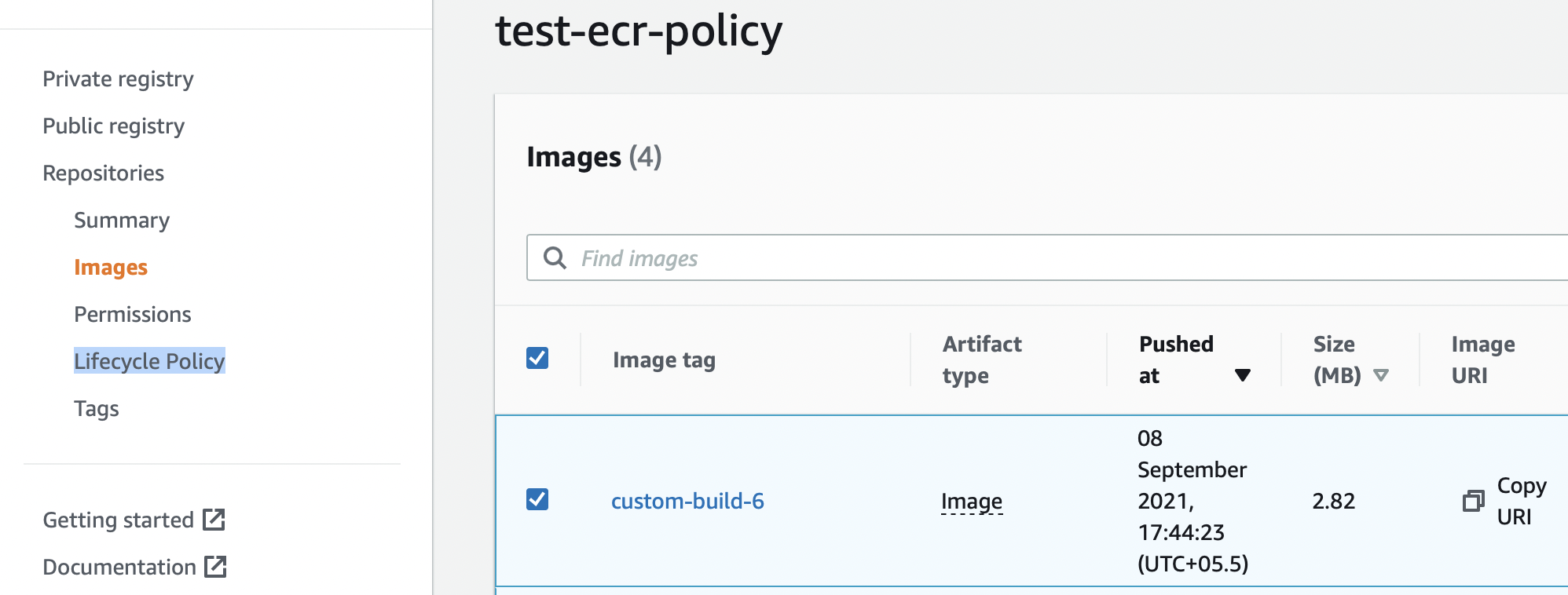
We will delete the image tagged as custom-image-6 residing in the repository test-ecr-policy.
Method 3: The Scripting Way!
The prerequisite for this method is having an AWS Access key configured in the machine you are running on.
Script to delete untagged images.
Lets see how to do it.
Step 1:Head over to the repository where you want to set the Lifecycle policy.
On the left panel, you’ve got the option to see the Lifecycle Policy.
you’re able to press it to get started.
Step 2:you might press it and create your first rule.
Lets see how it is done.
Choose according to your use case.
Dont forget; you’re able to increase these numbers to the number of your choice.
Save to trigger the Lifecycle Rule.
The AWS ECR CLI command to set lifecycle policy isput-lifecycle-policy.
Lets see how to do it.
For this, you must create a JSON file listing the policy conditions.
you might name it policy.json or any name of your choice.
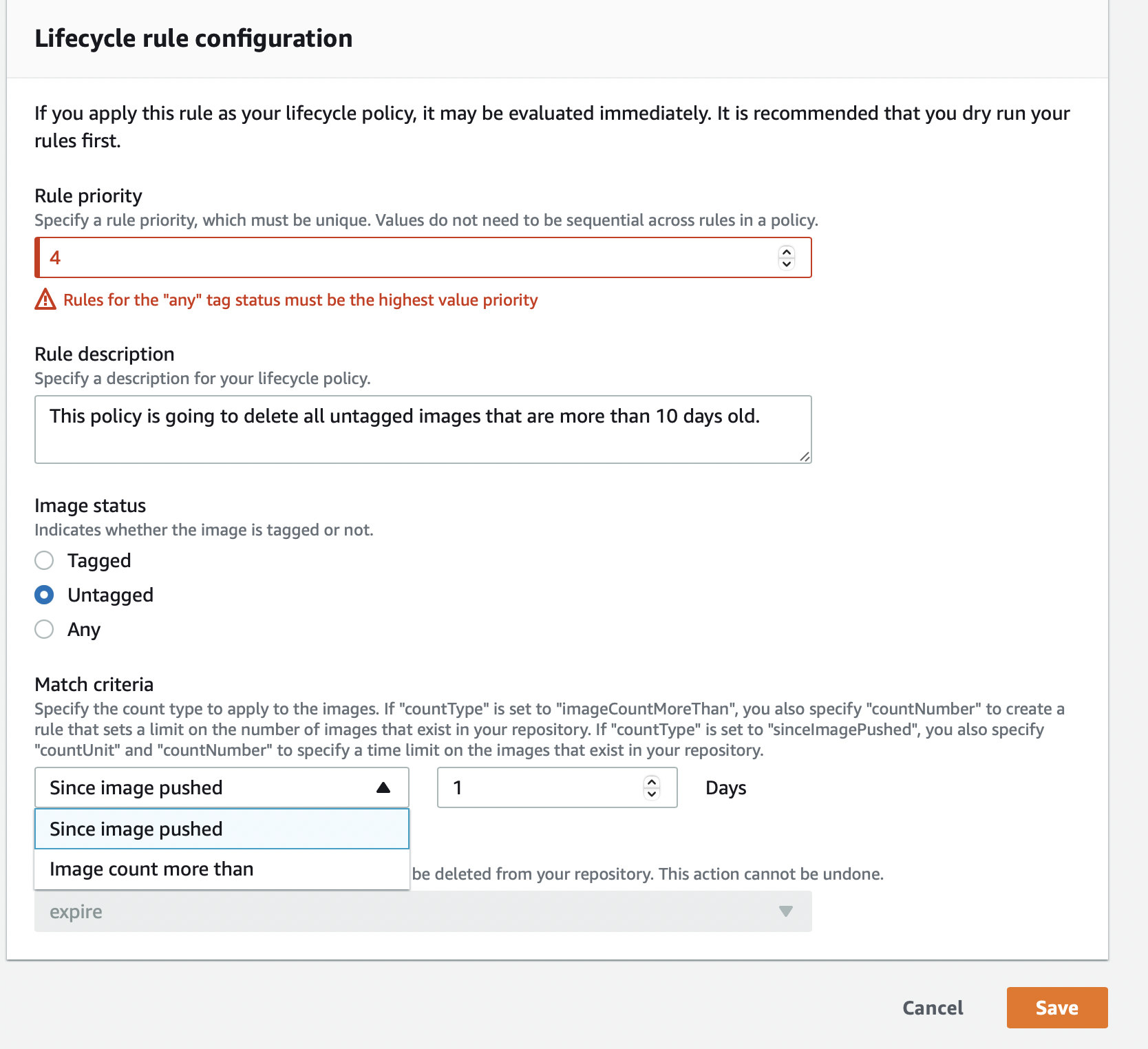
But before that, lets look at the lifecycle policy elements.
Lifecycle policy rules with priority one are applied first, then 2, etc.
Lifecycle policy rules must each have a unique rule value.
Policy rules dont need consecutive values.
Any-tagged rules must have the highest rulePriority and be reviewed last.
Explains what a rule in a lifecycle policy is for.
It checks if the added lifecycle policy rule specifies an image tag.
Tagged, untagged, or any is OK.
If none is specified, all images are evaluated.
Tagged requires a tagPrefixList value.
Untagged requires omitting tagPrefixList.
If tagStatus is tagged, your lifecycle policy requires a comma-separated list of image tag prefixes.
Multiple tags pick only images with all tags.
Specify countNumber if countType is imageCountMoreThan to limit the number of images in your repository.
Specify countUnit and countNumber if countType is sinceImagePushed to limit the repositorys images.
Only specify a count unit when countType is sinceImagePushed; otherwise, an error occurs.
Positive integers only (0 is not an accepted value).
If countType is imageCountMoreThan, the value is the maximum number of photographs to keep.
Using sinceImagePushed as the countType determines the maximum image age.
Choose a pop in of action.
The value that can be used is expire.
Here is my policy.json.
According to your organizations requirements.sinceImagePushedcan be replaced withimageCountMoreThan.
We can use the same policy.json to set this up.
Below is the used code snippet.
How do Apply a Single Policy Across Multiple ECR Repositories?
Often, there are questions on how to apply the same policy across multiple repositories.
It is a repetitive and boring task to set policies manually.
AWS provides extensive documentation as well as samples of lifecycle policies.
You may also explore someAWS Key Terminologiesthat advance your AWS Learning.