We earn commission when you buy through affiliate links.
This does not influence our reviews or recommendations.Learn more.
Identifying SQL injection vulnerabilities can be done through manual and automated testing.
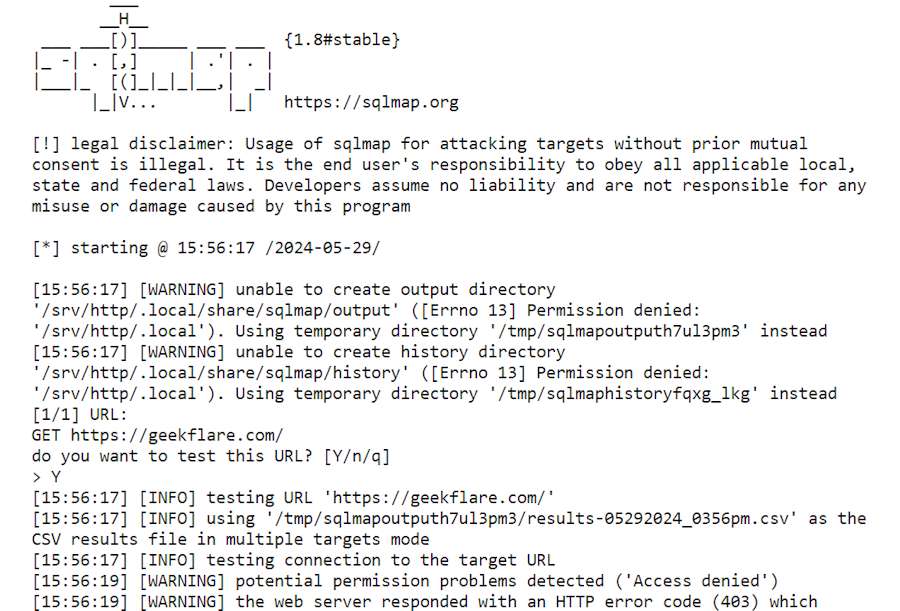
These processes include checking error messages, reviewing input validation procedures, etc, to identify any potential vulnerabilities.
suIP.biz
suIP.biz is a popular SQL injection scanner that supports all leading database management systems.
Super IP is a free tool.
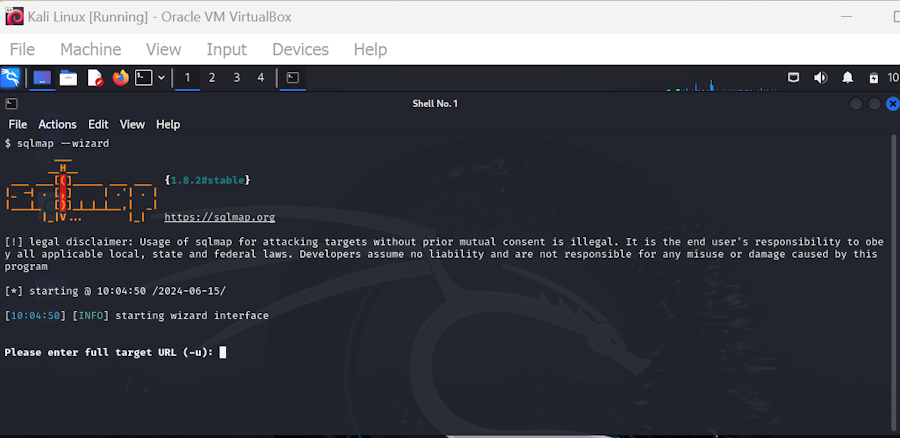
SQLMap is a free tool, and you might download it from Git.
Pentest Tools SQL Injection Scanner
Pentest Tools SQL Injection Scanner is powered by its proprietary scan engine.
It crawls and performs a deep inspection of your applications web pages and parameters to discover vulnerabilities.
A good thing about Pentest Tools SQL Injection Scanner is that it makes reading vulnerability reports easier.
Pentest Tools SQL Injection Scanner allows you to see visual representations of risk ratings.
This feature helps you prioritize tasks in vulnerability management.

InsightAppSecs Universal Translator can normalize traffic from different formats, protocols, and modern development technologies.
Acunetix detects 7000+ web vulnerabilities.
This feature enhances your web servers security.

Additionally, Acunetix can work as a vulnerability assessment tool.
It classifies identified vulnerabilities and reports them with details about possible security implications and fixes.
Acunetix is available as an on-premises and cloud-based service.

The on-premises service is available for Linux, Windows, and macOS.
It has built-in compliance reports for various security audits, such as HIPAA and PCI DSS.
Acunetix follows a custom pricing plan.
it’s crucial that you communicate with the company to get the cost estimation for your requirements.
Probely
Probely is a comprehensive discovery and vulnerability scanning tool.
With Probely, you might detect around 3000 types of vulnerabilities, including SQL injections and XSS.

Probely offers a detailed report of the findings, including tips for fixing vulnerabilities.
It allows you to automate security testing efficiently by integrating it with your software development lifecycle.
Then, it tries to inject payloads to find out the vulnerable scripts.
Wapiti can scan your web tool for multiple SQL attack techniques, including time-based, boolean-based, and error-based.
Wapiti is free to use.
It can generate reports in HTML, CSV, XML, TXT, and JSON.
you’ve got the option to use it to scan single-page and multi-page applications.
Whats more, Intruder SQL Injection Scanner allows you to scan behind-login pages easily by adding authentication.
It can identify SQL injection vulnerabilities and 75+ other security issues found in web applications.
Its Pro Plan comes with a free 14-day trial.
The filter and tag findings feature also helps you prioritize vulnerabilities.
Its crawler can scan single-page applications and JavaScript-heavy applications equally.
Detectify offers two pricing models: the Full EASM solution and the Small Attack Surface.
Detectify offers two plans: Surface monitoring at 275 and utility Scanning at 82 monthly.
What Is SQL Injection?
SQL injections often happen when your web app includes user-generated inputs in SQL queries without proper validation or sanitization.
Needless to say, SQL injection attacks are one of the most common web app injection attacks.
In-Band SQL Injection
It is one of the most common forms of SQL injection.
Here are two types of in-band SQL injection attacks that are widely prevalent.
Instead, the attacker infers information based on the applications behavior or error messages to the attackers payload.
Here are two subdivisions of inferential SQL injections.
This is particularly useful when the software is not able to return data directly due to security measures.
Preventing SQL Injection Attacks
Here are some ways to prevent SQL injection attacks.
Additionally, you should do proactive database monitoring to discover any security issues before they can do any harm.
Combining manual testing with automated testing is the most effective way to identify all potential SQLi vulnerabilities.
Using third-party applications such as Securi is a must to enhance your utility security.