We earn commission when you buy through affiliate links.
This does not influence our reviews or recommendations.Learn more.
Do you know most of the security vulnerabilities can be fixed by implementing necessary headers in the response header?
attacks then this guide will help you.
Notes:
Using WordPress?
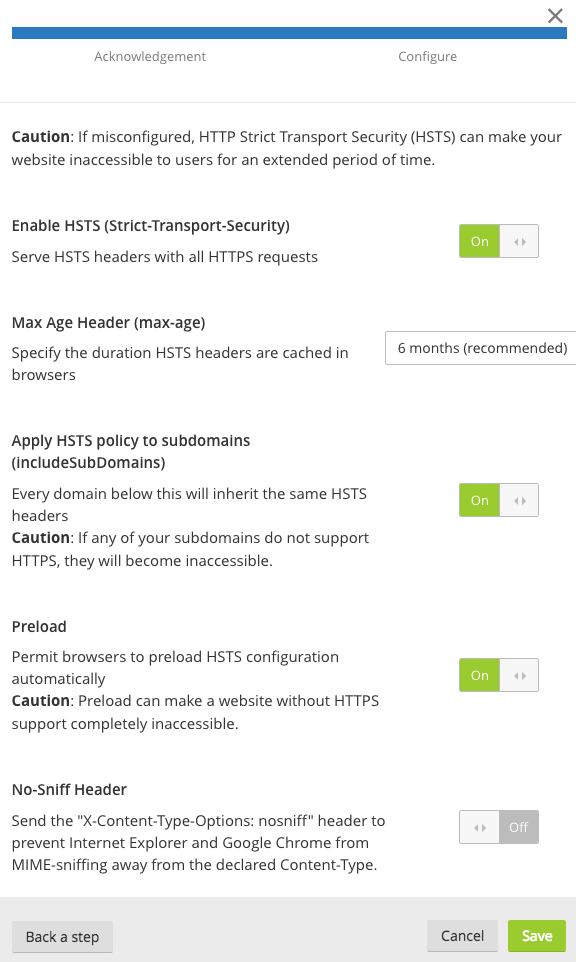
This prevents HTTPS click-through prompts and redirects HTTP requests to HTTPS.
There are three parameters configuration.
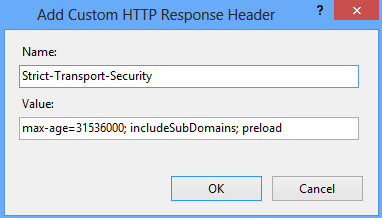
So lets take an example of having HSTS configured for one year, including preload for domain andsub-domain.
choose the tweaks the one you need, and changes will be applied on the fly.
Restart the site
X-Frame-Options
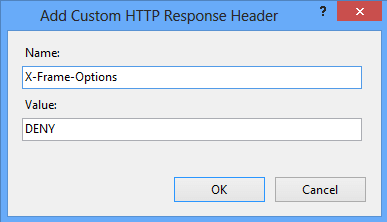
Use the X-Frame-Options header to preventClickjackingvulnerability on your website.
By implementing this header, you instruct the net internet ride not to embed your web page in frame/iframe.
This has some limitations in surfing app support, so you got to check before implementing it.
you’re free to configure the following three parameters.
Lets take a look at how to implement DENY so no domain embeds the web page.
Apache
Add the following line inhttpd.confand restart the webserver to verify the results.
Add the following innginx.confunder server directive/block.
You dont need to restart anything, changes are reflected in the air.
WordPress
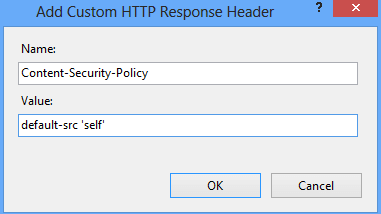
you’re able to get this header implemented through WordPress too.
Add the header by going to HTTP Response Headers for the respective site.
Restart the site to see the results.
X-Content-throw in-Options
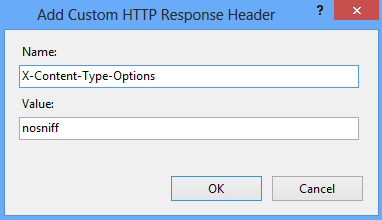
PreventMIMEtypes of security risk by adding this header to your web pages HTTP response.
Having this header instructs net surf tool to consider file types as defined and disallow content sniffing.
There is only one parameter you got to add nosniff.
Lets see how to advertise this header.
Add the following line innginx.conffile under server block.
As usual, you got to restart the Nginx to check the results.
Allbrowsers dont support CSP, so you got to verify before implementing it.
There are three ways you’re free to achieve CSP headers.
If you are still using the deprecated one, then you may consider upgrading to the latest one.
However, lets go through the two most used parameters.
The following example of loading everything from the same origin in various web servers.
Get the following added inhttpd.conffile and restart the webserver to get effective.
This is an advanced version of X-Frame-Options.
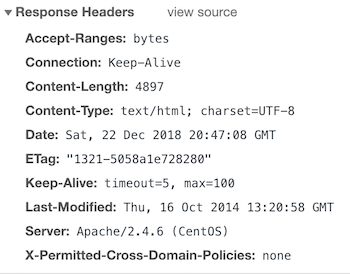
X-Permitted-Cross-Domain-Policies
Using Adobe products like PDF, Flash, etc.?
By implementing this header, you restrict loading your sites assets from other domains to avoid resource abuse.
There are a few options available.

If you dont want to allow any policy.
You should see the header like the following.
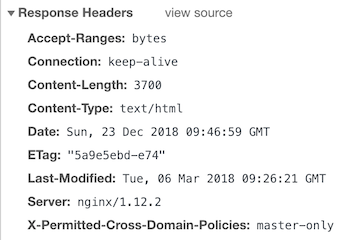
And, lets say it’s crucial that you implement master-only then add the following innginx.confunderserverblock.
Referrer-Policy
Looking to control the referrer-policy of your site?
There are certain privacy and security benefits.
Referrer-Policy supports the following syntax.
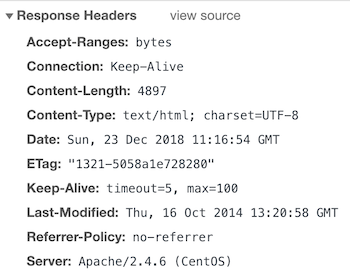
you’re able to add the following if you want to set no-referrer.
And after the restart, you should have in the response headers.
Lets say it’s crucial that you implement the same origin, so you got to add the following.
Once configured, you should have the results below.
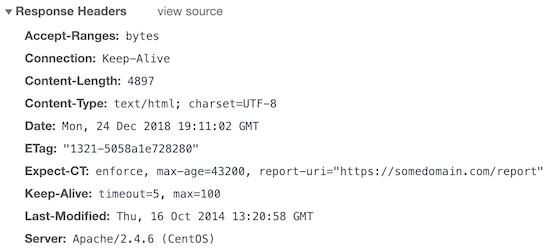
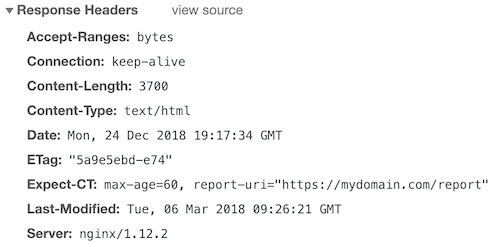
This project by Google aims to fix some of theflaws in the SSL/TLS certificatesystem.
The following three variables are available for the Expect-CT header.
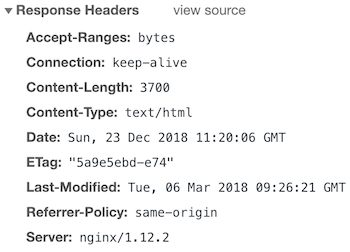
And, here is the result.
What if you want to report and cache for 1 hour?
The output would be.
Permissions-Policy
Earlier known as Feature-Policy, it is renamed as Permissions-Policy with enhanced features.
you’ve got the option to check outthisto understand the big changes between Feature-Policy to Permissions-Policy.
to enable or disable within a web tool.
How about adding multiple features in a single line?
Restart Apache HTTP to see the result.
The above code will instruct the online window to disable fullscreen and microphone.
You may also deactivate the feature entirely by keeping the allowlist empty.
For example, it’s possible for you to add the following to shut down the geolocation feature.
This would output on the online window like below.
Lets take another example disable vibrate feature.
Or, disable geolocation, camera, and speaker.
Here is the output after restarting Nginx.
All the Nginx configuration goes underhttpblock innginx.confor any custom file you use.
This gives you more control over how you want to store the websites data in the web client.
Lets say you want to wipe the origin cache, it’s possible for you to add below.
Which will output HTTP response as below.
or, to clear everything.
Lets set Nginx to clear cookies.
And, you will see the output below.
The good thing about SUCURI is it offers both security and performance.