We earn commission when you buy through affiliate links.
This does not influence our reviews or recommendations.Learn more.
Cybercriminal activities are making headlines today.

It has become easier for hackers to access business systems and email accounts in this technological age.
And one of the essential components of email security isPGP Encryption.
What is PGP Encryption?

Cybercriminals often target emails to forge data and messages using the users name or identity.
PGP encryption solves this issue and enhances email security by encrypting email data and making communication more private.
It scrambles the data to make it unreadable to those without the means to decode it.
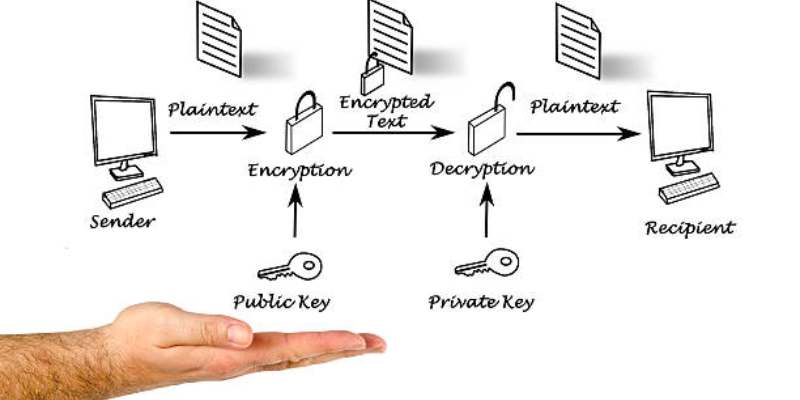
This encryption system was first developed and designed in 1991 by Pual Zimmerman.
Later, the system was supported and standardized for other applications, like email.
Thus, in simple terms, PGP provides cryptographic authentication and data privacy for online communication.

How Does PGP Encryption Work?
On a technical level, it uses a combination of data compression, cryptography, and hashing techniques.
Thus, it uses private, public, and session keys to protect data.

Once the receiver receives the encrypted message or the email, they decrypt it using the private key.
It compresses the plaintext data, saving disk space and transmission time and reinforcing cryptographic security.
The PGP encryption uses efficient algorithms that help create a mathematical summary called hash to send digital signatures.

The hash code can be digital data like a username encrypted by the email senders private key.
However, it comes with many risks related tomalware, data breaches, and cybersecurity attacks.
PGP encryption eliminates unauthorized access issues using its secure data and information exchange process.
Digital signatures use an algorithm combining the senders key with the message they want to send.
The recipient can then decrypt this message using the senders public key.
Even if one of the messages characters has been changed during the transit, the recipient can determine it.
How to Set up PGP Encryption?
Setting up and using PGP encryption includesdownloading an add-on for your email clientor program and following the installation instructions.
Add-onsare available for email clients, includingOutlook, Thunderbird, Apple Mail,and more.
In addition, several online email systems, like ProtonMail, also consist of PGP by default.
Hence, in such cases, you need not download an additional add-on.
Here are a few tips for selecting an appropriate PGP software from multiple options that best meet your needs.
This results in a usability issue, making PGP implementation difficult at both GUI and the command line.
#2.Key Management
Managing PGP keys can be a challenge.
This can create difficulty in using PGP encryption to communicate with those without PGP encryption or other encryption methods.
This makes it easier to compromise the information, leaving it vulnerable to interception.
#6.Trust
PGP encryption heavily relies on the involved partys trustworthiness.
However, at the same time, online email security doesnt start and end with PGP encryption.
Next, check outhow much is your personal information worth on the dark web.