We earn commission when you buy through affiliate links.
This does not influence our reviews or recommendations.Learn more.
Lattice-based cryptography technique is an excellent method of securing information using a series of mathematical formulae.

Cryptography comes in multiple flavors.
In general, it uses a series of codes to encrypt your data.
For the longest time, cryptographic tools like encryption schemes followed ad-hoc designs.
Security was completely based on heuristics and intuition.
Another problem is that existing standards of cryptography are not that reliable.
The development ofquantum computerscan further break the standards, resulting in an increased feat among users.
Therefore, encryptingpersonal informationis essential for everyone.
Subsequently, there was a requirement for a new idea or technique that no one could break.
We needed improved standards that can secure data even after using quantum computers.

After a lot of brainstorming, a new method has evolved, i.e., Lattice-based Cryptography.
In this article, Ill discuss lattice-based cryptography, its importance, how it works, and more.
What Is Cryptography?

This will prevent unauthorized access to the data.
The term cryptography is created by combining two words crypt and writing.
Here, crypt means hidden and graphy means writing.

There are three types of Cryptography:
Whats Lattice-Based Cryptography?
Lattice-based cryptography is a simple term used for the building of cryptographic algorithms that involve lattices.
It is used for post-quantum cryptography to secure information.

Unlike known-public schemes, lattice-based schemes are more resilient and can withstand attacks from quantum computers.
This is not finite; instead, a lattice defines a pattern that keeps continuing infinitely.
However, the encryption scheme is not that hard to solve.

Since then, the follow-up work has continued to improve the efficiency of the original encryption scheme.
In 2009, Craig Gentry came up with the first homomorphic encryption scheme based on complex lattice problems.
Examples:CRYSTALS-Dilithium (digital signature algorithm) and CRYSTALS-KYBER (public key encryption and key establishment algorithm).

How Does Lattice-Based Cryptography Work?
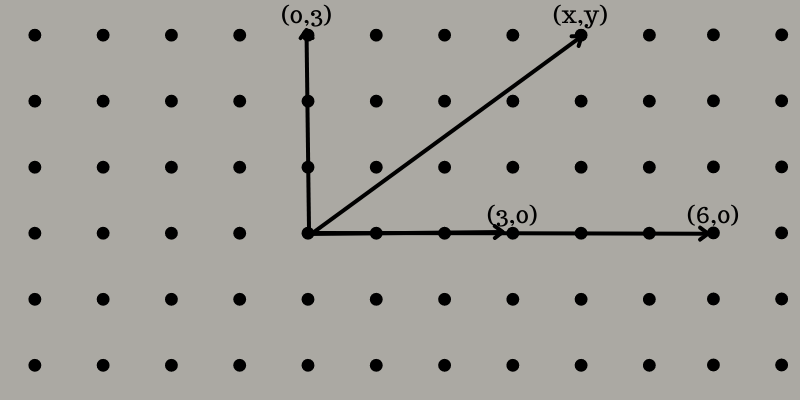
Here, you will find a grid of points on a flat surface like a piece of paper.
Lets choose two or more points that are not a single line going through the origin.

For example, you choose (3,0) and (0,3).
Add the result points to get (6,-3).
Thus, if you know the key, you’re free to easily decode the message.
Benefits of Lattice-Based Cryptography
Lattice-based cryptography offers a lot of benefits for individuals and businesses.
Lower Energy Consumption
Energy consumption increases with the increase in the usage of any system.
Despite being faster, lattice-based cryptography consumes less energy as compared to other encryption schemes.
This is because lattice-based cryptography is implemented in hardware, resulting in less power consumption.
For example, processors designed for cryptocurrency mining are more energy efficient than traditional processors when using lattice-based cryptography.
High-Speed Computation
Unlike other cryptography algorithms, the encryption scheme of lattices is computed much faster.
Easy to Implement and Flexible
Nowadays, businesses are looking for flexible options and saving time.
Lattice-based cryptography is easy to implement as it requires less amount of resources and is highly accessible.
you’re free to also implement it on off-the-shelf hardware easily.
Thus, it offers a lot of flexibility.
Thus, you’ve got the option to use these keys in standard protocols.
This gives assurance to individuals and professionals about their information security.
These are available online and can help you to become a pro in this security method.
Lets dive into these books and courses.
This book provides fundamental insights into the proper construction of the security layer from hard lattice problems.
This includes designing attribute-based encryption, digital signatures, key change, identity-based encryption, and public-key encryption.
#2.Lattice-based Public-Key Cryptography in Hardware
The book is written by Sujoy Sinha Roy and Ingrid Verbauwhede.
The devices can be tiny Radio Frequency Identification tags, desktops, and more.
The authors also investigate the implementation of post-quantum homomorphic encryption and public-key cryptography schemes.
In the thesis, the author proposed alternative cryptography based on the worst scenario of lattice problems.
Conclusion
Cryptography is a simple yet powerful tool to protect the information saved in your systems.
Lattice-based cryptography is one of the most secure security mechanisms that use simple linear algebra to encrypt the data.
It includes lattices, vectors, and basis that are used to construct a tough pattern.
If you have the key, it’s possible for you to easily decrypt data.
You may also read Cloud Cryptography.