We earn commission when you buy through affiliate links.
This does not influence our reviews or recommendations.Learn more.
What is Passwordless SSH?
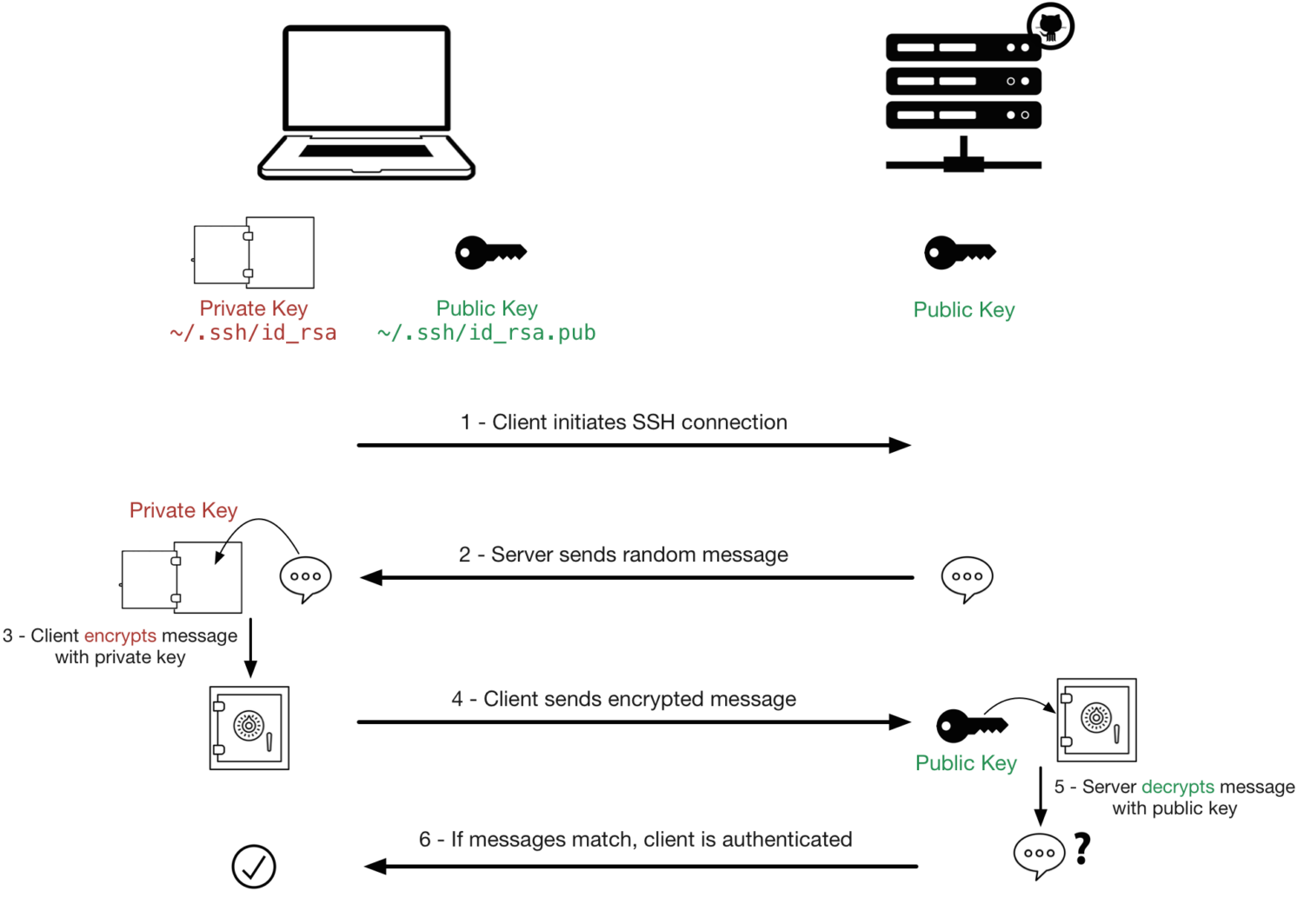
The way to achieve this is by using an asymmetric key pair.
If authorized, the authentication process continues.
If it is not authorized, the process ends, and you cannot dive into the server.
If the server authorizes the clients public key, the server encrypts a message with the clients public key.
Once the server has encrypted the message, it sends it to the client.
The client receives the message from the server.
Once the message is received, the client tries to decrypt this message with the private key.
Why use SSH Passwordless login
Passwordless SSH offers several benefits over traditional password-based login methods.
The process would be encrypted through SSH and completely automatic because you wont have to enter any password.
In addition, multiple git servers use SSH public key authentication.
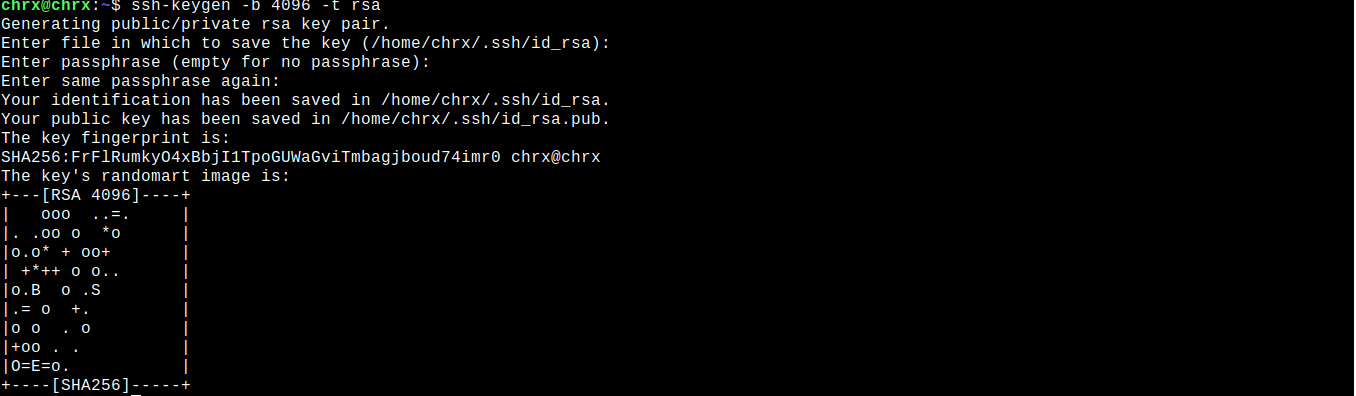
-b 4096: you are indicating that the asymmetric key to be generated has a size of 4096 bits.
Other sizes that you might choose, for example, are 1024 or 2048.
-t rsa: Indicates that the algorithm used to generate the key pair must be RSA.
Other algorithms that we can use are DSA, ECDSA, RSA1, and ED25519.
Just press the Enter key.
Next, you will be asked if you want to enter a password to encrypt the private key.
Finally, you are asked to re-enter the password.
Since we have not entered any password, press the Enter key again.
After performing these steps, the asymmetric keys will be created in the location ~/.ssh.
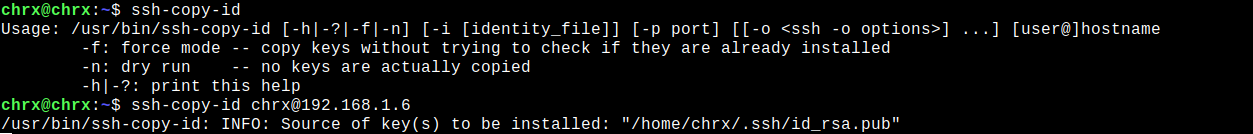
you oughta copy the public key to the remote server, either using the command ssh-copy-id or manually.
The typical syntax for the SSH public key copy command is as follows.
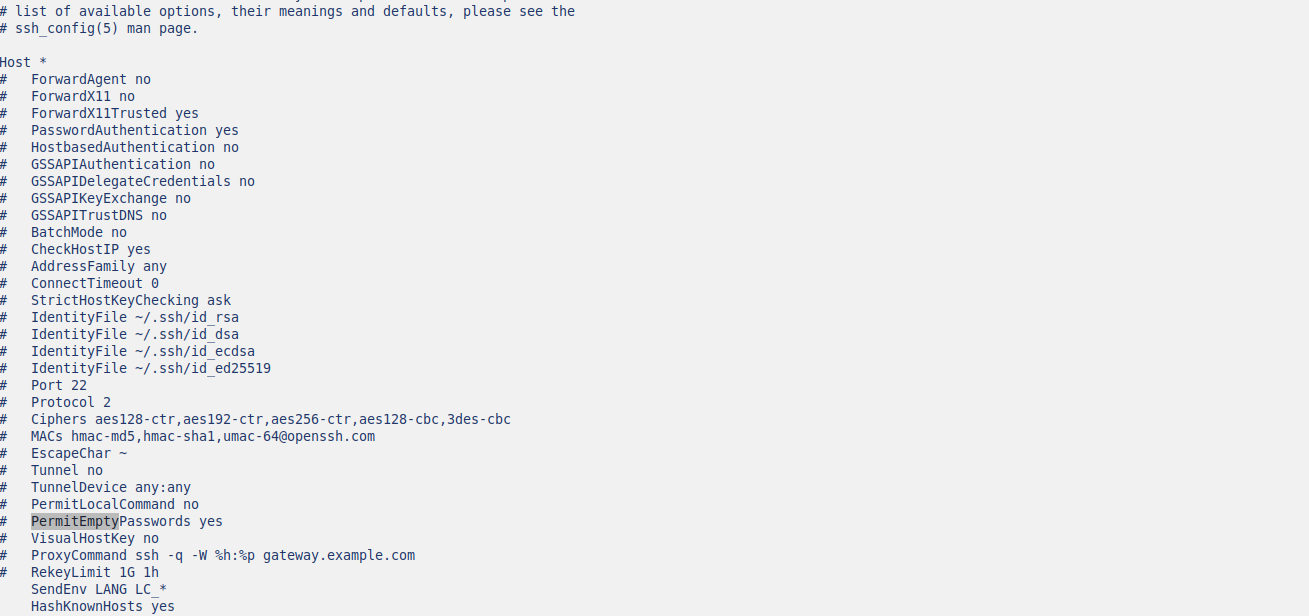
On most distributions, the configuration file is located at /etc/ssh/sshd_config.
Locate the line that readsPermitEmptyPasswordsyesand ChangePermitEmptyPasswords yestoPermitEmptyPasswords no.
Save the changes to the configuration file and exit the text editor.
You may also exploreSymmetric Encryption.