We earn commission when you buy through affiliate links.
This does not influence our reviews or recommendations.Learn more.
Hence, every individual and organization must understandsocial engineeringtechniques and how evil twin attack aids in social engineering.
This article will explain the evil twin attack and its detection and prevention.
What are Evil Twin Attacks?
The Evil Twin Attack is a wireless LAN version of aphishing attack.

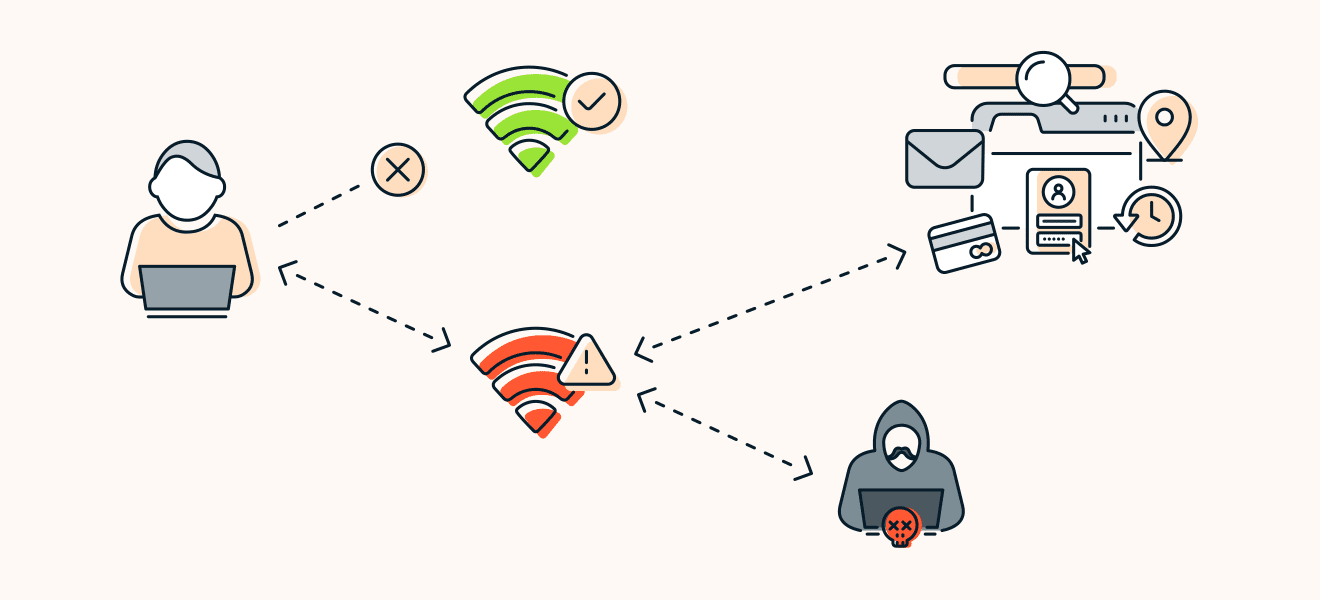
An evil twin attack is a rogue WiFi access point that seems genuine but eavesdrops on wireless communication.
This malicious WiFi access point deceives the user into connecting to it.
The evil twin attack leads to data theft, unauthorized access, and other cyber crimes.

How Does the Evil Twin Attack Work?
The hacker ensures that these places have multiple access points where the WiFi has similar names.
Step II
The hacker checks the available internet and then sets up an account.

They may also use WiFi pineapple for a broader range and deceive the unaware user into connecting to it.
Step III
The fake access points are wireless cards.
They are difficult to trace and may get shut off instantly.

The attackers sometimes use WiFi pineapples help to create a more robust web connection.
The hackers have unauthorized access to the devices once the unaware user logs into their evil twin internet.
The evil twin attacks can be dangerous as thehackeraccesses the users bank details and social media accounts.

More data theft happens if the user uses the same login credentials for other sites.
Effects of Evil Twin Attacks
The evil twin attacks not only individuals but also organizations significantly.
It exploits users trust in public WiFi networks.
#2.Unauthorized Data Access
Unauthorized data access can lead to fraudulent activities like breaches.
The attacker can steal and alter the information and send messages or emails on behalf of the victim.
He may transfer money, use services, or sell the account credentials.
#4.Malware Attack
Cyber attackers can also distributemalwareto the system and steal data.
The victims can unknowingly download the malicious virus while connecting to the data pipe.
These viruses can hamper the overall health of the system or gadget.
How to Detect Evil Twin Attack or Fake WiFi
Check for duplicate networks.
If networks have identical names, an evil twin is likely mimicking a legitimate connection.
If you find an Evil Twin online grid, always check its signal strength.
The Evil Twin web connection will always have a stronger signal than the legitimate web connection.
Use web connection security software and web connection scanning applications.
This software and applications detect and notify the user if they find any suspected WiFi threats.
They also warn you if any malicious activity or web link is detected.
Lets give a shot to know them.
Examples of an Evil Twin Attack
Lets take an example of an Evil Twin Attack.
He checks the available networks and finds two WiFi networks with a similar name.
One of the networks out of the two is an Evil Twin web link trying to deceive the user.
The unaware user connects with the Evil Twin connection due to its strong connection signal.
The hacker gets unauthorized access to his machine once the unaware user connects to the rogue internet.
Best Practices for WiFi Security
Here are some best practices to keep your WiFi connection secure.
Some of these practices are similar to the Evil twin attack prevention methods.
Use a Firewall:Firewallsblock incoming unauthorized traffic and protect your equipment from cyber-attacks.
Use MAC Filtering:MAC filtering allows devices with MAC addresses to connect to your internet.
This filtering prevents unauthorized access and malicious practices.
Disable Remote Management:Turning off the routers remote management prevents attackers from accessing the routers parameters.
Next, check out how to prevent attack vectors on your connection.