We earn commission when you buy through affiliate links.
This does not influence our reviews or recommendations.Learn more.
We will also see how criminals can use the gadget illegally to steal sensitive information from unsuspecting users.

So, lets start.
What is Wi-Fi Pineapple?
Wi-Fi Pineapple is a portable, penetration-testing gadget for identifying vulnerabilities in wireless networks.
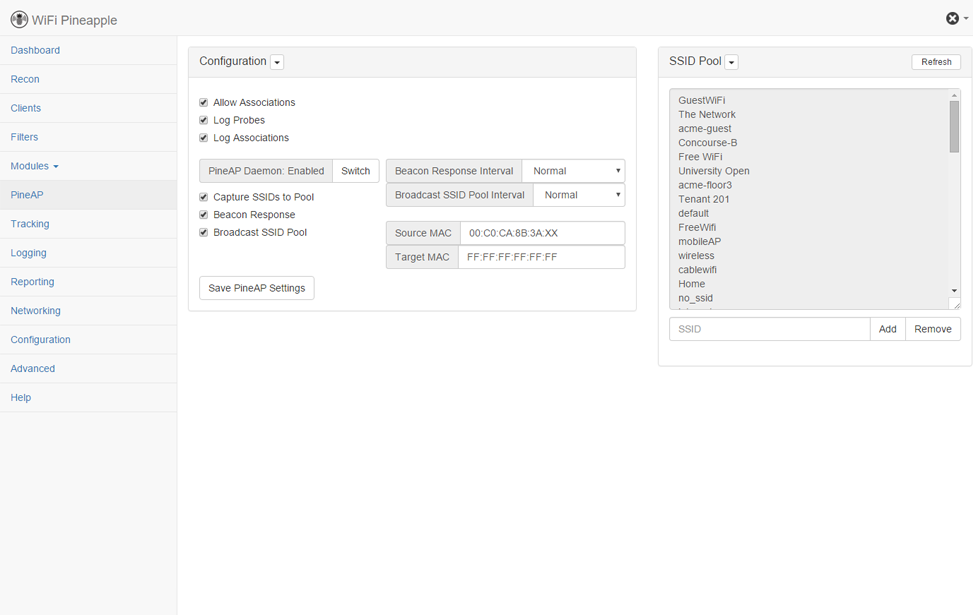
The Wi-Fi pineapple devices are almost similar to standard wireless access points.
However, they have more power, longer ranges, and a higher number of supported devices.
The devices have additional features designed to perform penetration testing and connection auditing.
This allows them to identify and address vulnerabilities in wireless networks.
Generally, the equipment is readily available, easy to use, and inexpensive.
Penetration testers, ethical hackers, and cybercriminals can use the pineapple unit for various reasons.

When used legitimately, the equipment provides a powerful data pipe auditing tool.
Usually, a Wi-Fi-enabled unit will continuously broadcast some information as it attempts to find available Wi-Fi networks.
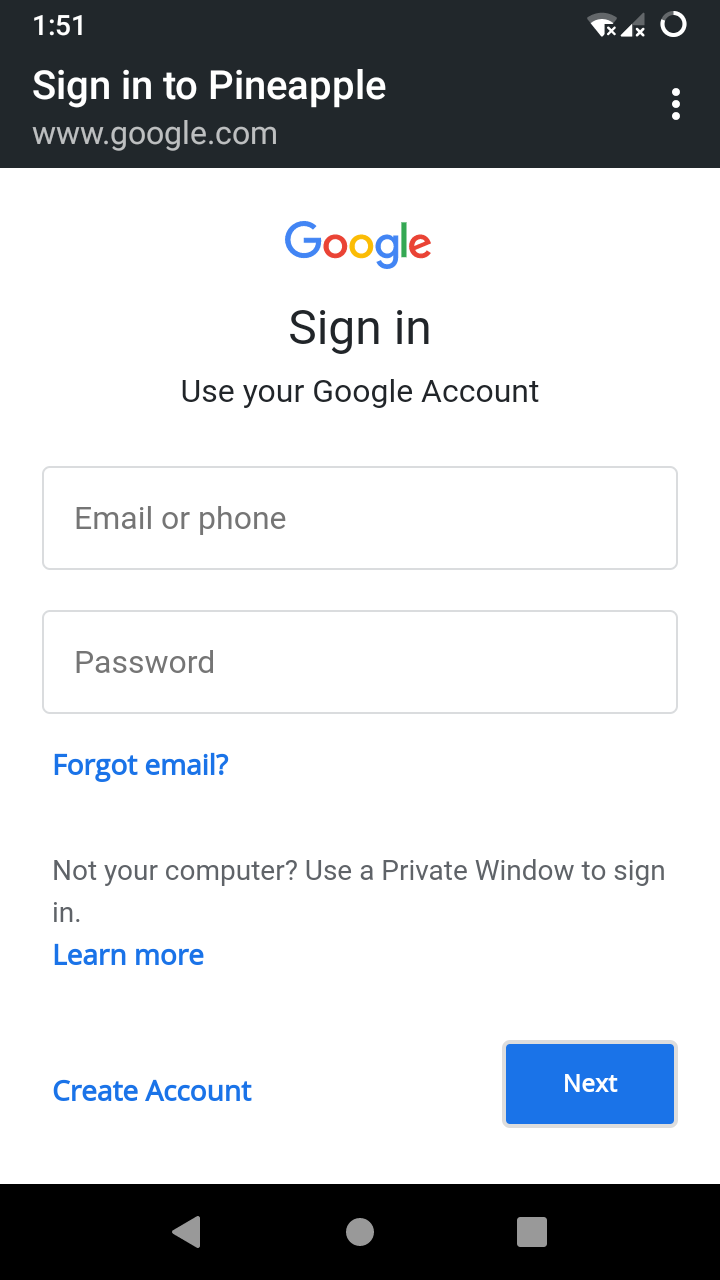
However, these are fake wireless access networks with the same name.

The user will then connect to the fake data pipe, usually without providing a password.
It usually pops up if users send unencrypted data over wireless networks.
The idea of the Wall of Sheep is to shame users and help them practice safe online practices.
However, attackers can use the same strategy to steal private information and compromise the affected accounts and devices.
The evil portal emulates popular and trustworthy websites, login pages, and other platforms accessible over the internet.
Additionally, they can infect the users machine withmalwareor viruses.
The attacker then connects the user to the less secure HTTP version of the website.
The Wi-Fi Pineapple has an easy-to-use interface and severaldownloadable modulesto audit wireless networks and identify vulnerabilities.
Penetration testing is an authorized hacking practice that organizations can use to detect and address security vulnerabilities.
Ideally, the pineapple allows ethical hackers to perform penetration testing and audit the security systems.
What to do if compromised in a Wi-Fi pineapple attack?
Conclusion
The Wi-Fi Pineapple devices provide a powerful and effective web connection auditing tool.
It can monitor online grid traffic, simulate several cyberattacks, and help security professionals identify vulnerabilities.
Usually, it is very easy to fall victim to Wi-Fi pineapple attacks unless one is very careful.
One way to remain safe is to avoid public Wi-Fi networks.
Next, check out the bestWi-Fi analyzer softwarefor small to medium business networks.