We earn commission when you buy through affiliate links.
This does not influence our reviews or recommendations.Learn more.
In email spoofing, cybercriminals dont have to hack systems to get inside your IT web link.
They just need one employee to click a link in a spoofed email.
That single click can install malware, paving the way for them to access your online grid.
So, it is important to defend against email spoofing attacks to strengthen your cybersecurity posture.
Threat actors often exploit SMTP to spoof email addresses because it lacks security features like encryption or authentication.
An email has three parts: the envelope, the header, and the body.
The email header visible in your inbox shows the senders name, subject line, and timestamp.
The body of the email is the content sent as a message.
And recipients dont see the SMTP envelope.
The goal of email spoofing is often to manipulate users into trusting malicious content.
While DMARC addresses SMTP vulnerabilities, many domains remain unprotected, leaving them open to spoofing attacks.
We will discuss these security measures later in this article.
Lets first explore different types of email spoofing.
Below, we have listed three commonly used email spoofing techniques attackers use for email spoofing.
Sender Spoofing
Sender spoofing is the simplest pop in of email spoofing and requires no technical expertise.
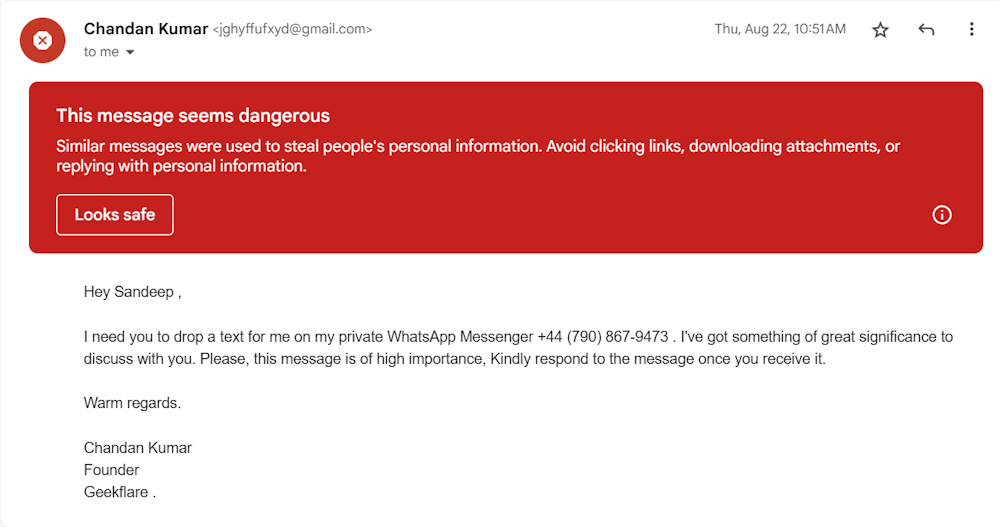
Here is an example of a sender spoofing email in which the attacker impersonated our founder.
As you’re able to see, the attacker just forged the display name in this email.
Sender spoofing emails can pass all spoofing countermeasures because they come from legitimate emails.
In the above example, the threat actor used Gmail to send a spoofed email.
Instead, they simply check whether the company has implemented security protocols like DMARC using specialized tools.
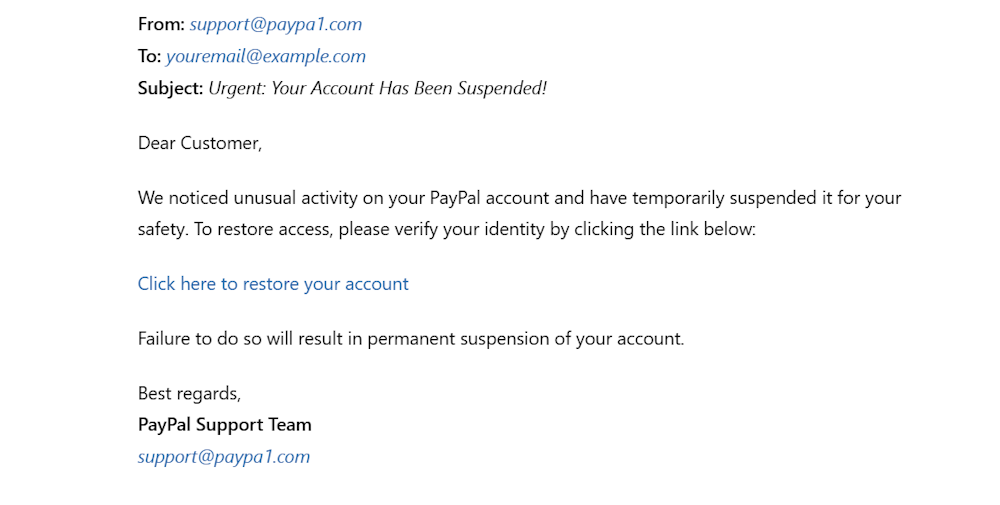
For example, they might register paypa1.com, which closely resembles the legitimate domain paypal.com.
The only difference is that the spoofed domain has 1 instead of l in the spelling of PayPal.
Unaware recipients might overlook slight spelling differences.
A single punch a malicious link in a spoofed email can install malware.
Despite training employees on email spoofing, many organizations continue to face the threat of email spoofing.
Here are the critical challenges of email spoofing.
As SMTP was designed to offer simplicity and efficiency, it lacks built-in email authentication.
confirm to implement email authentication protocols like SPF, DKIM, and DMARC.
These add layers of verification, making it harder for attackers to spoof emails.
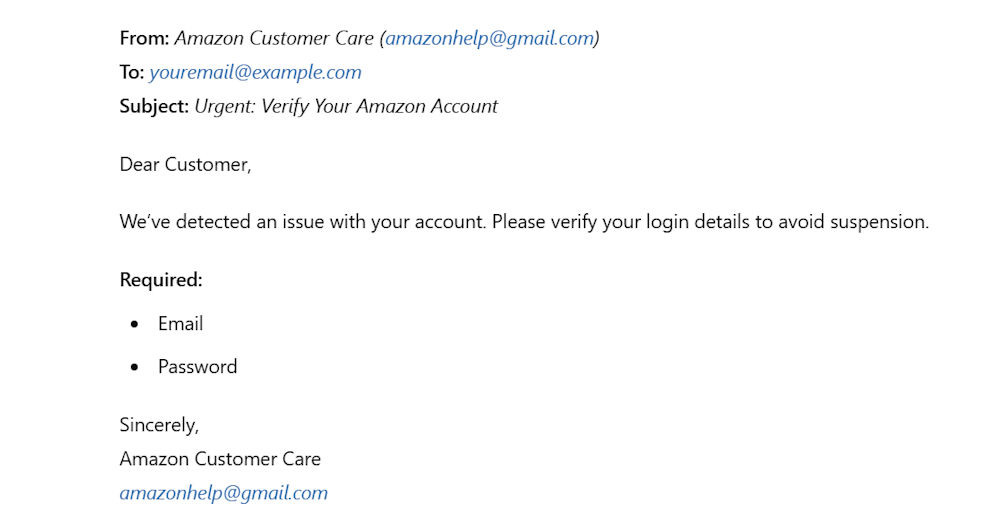
For example, a threat actor can create a Gmail address under the name Amazon Customer Care.
Subtle changes to email addresses or logos can easily deceive even vigilant users.
You should also use email security tools that highlight spoofed or suspicious senders.
Raising awareness helps prevent users from falling for deceptive messages.
Therefore, you should make a policy of conducting regular training on recognizing spoofed emails and cybersecurity best practices.
This makes it difficult to curb the menace of email spoofing.
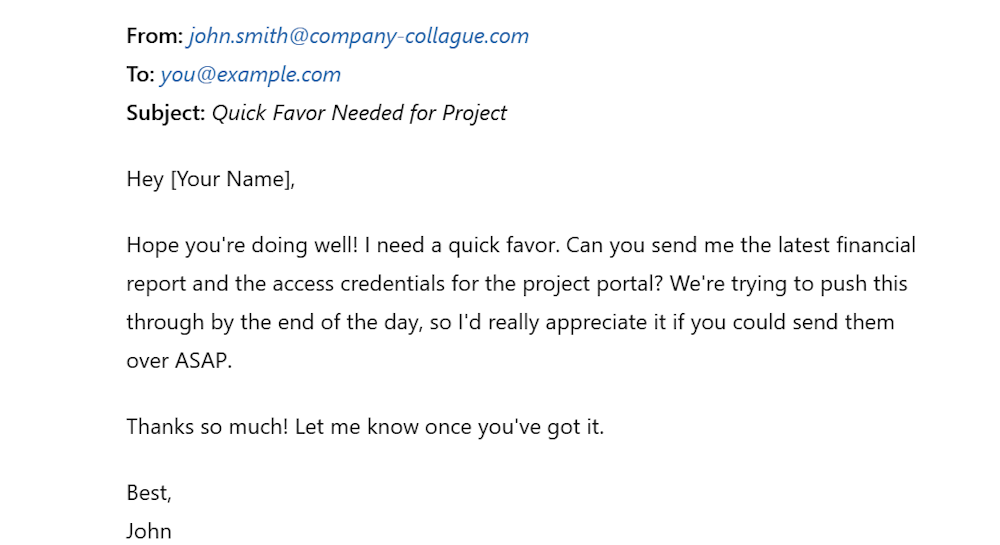
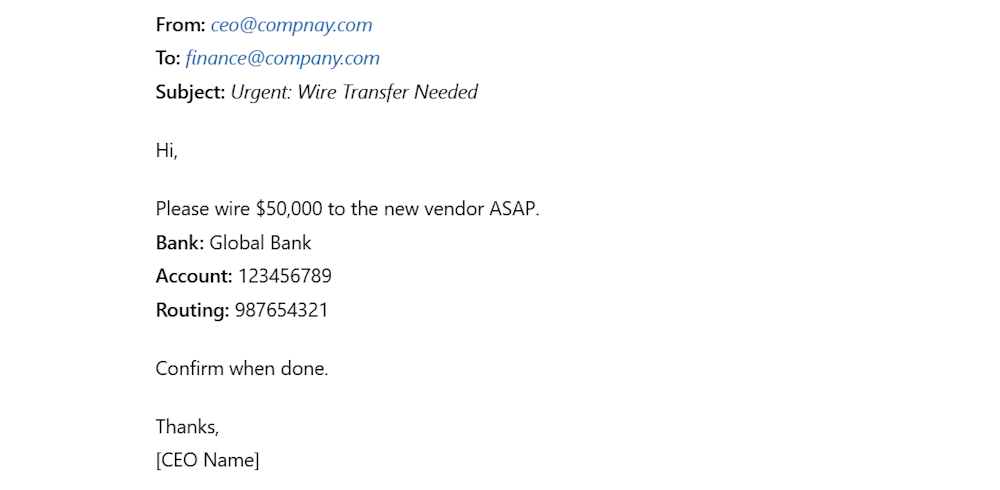
For example, you receive an email from John Smith, the CFO of your company.
He is asking you to transfer funds to a vendor urgently.
Tell them to double-check requests for sensitive actions like fund transfers.
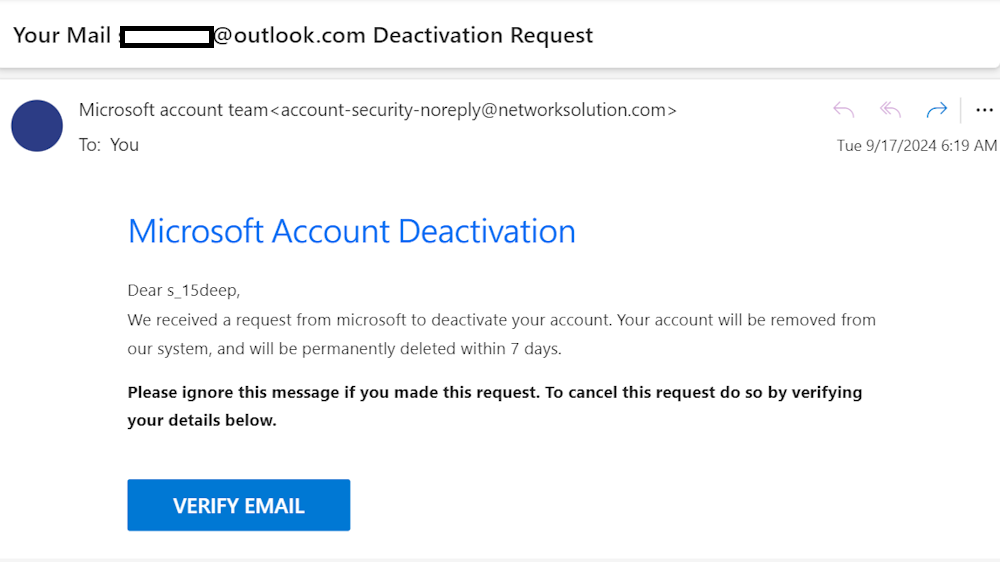
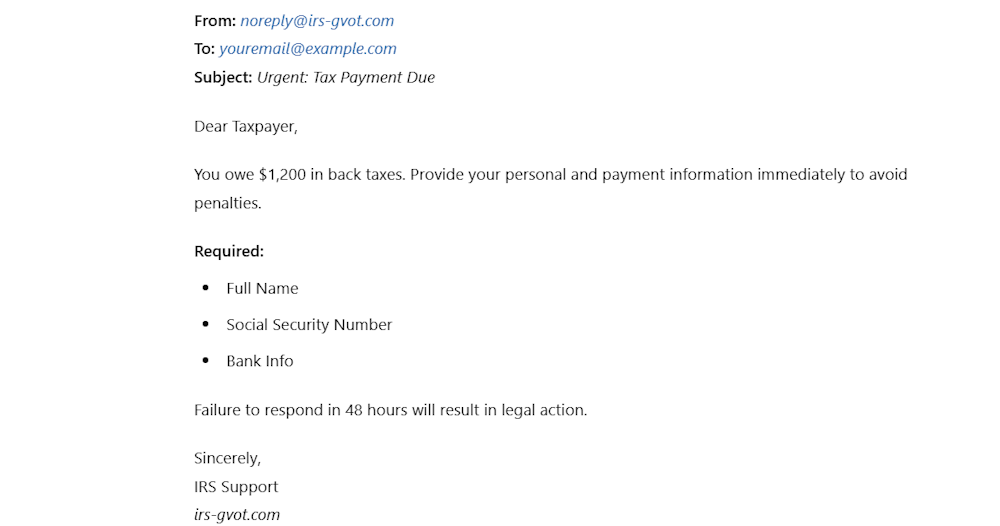
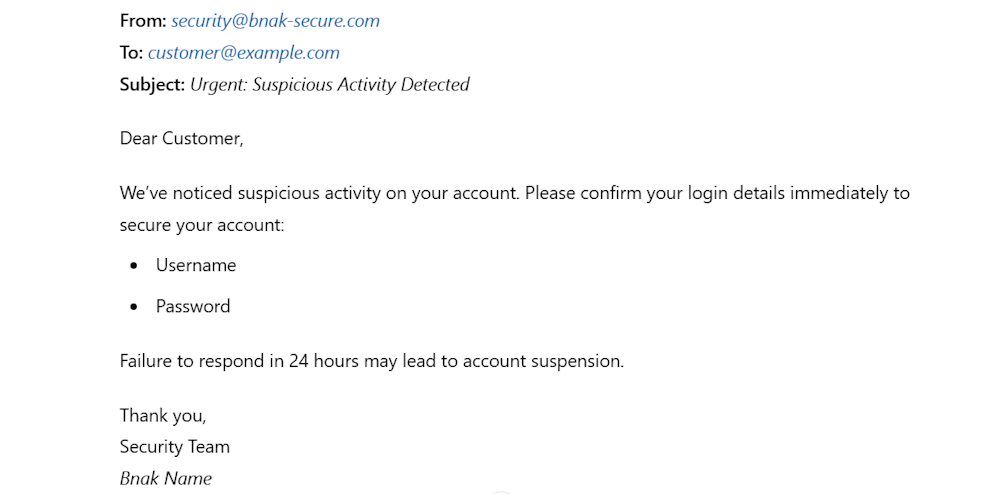
For example, a spoofed email might claim that an account is compromised and requires immediate action.
You should also encourage them to pause and verify any email that urges immediate action or requests sensitive information.
How To Identify a Spoofed Email
Identifying a spoofed email doesnt require technical expertise.
Here are some tips to identify a spoofed email.
Also, you should analyze the email header.
It should pass SPF, DKIM, and DMARC authentication.
If it fails any of those, you should be extra cautious about handling the email.
Email spoofing is an attack vector often used across multiple phishing attacks.
Various legal authorities and regulations have made rules against email spoofing.
For example, The CAN-SPAM Act prohibits deceptive email practices in the U.S.
The UK Fraud Act 2006 provides users protection against phishing emails.
India also has a strict law to prevent email spoofing.
The Indian IT Act 2000 has various provisions against cyberattacks, including phishing.
Countries worldwide are working hard to prevent email spoofing, but hackers continue to target users with spoofed emails.
As a business owner, its your responsibility to protect sensitive data from your customers and vendors.
Adata breachdue to email spoofing can result in significant financial and reputational damage.
To minimize the risk, you should strengthen your defenses and take proactive steps to mitigate email spoofing attacks.
Can I Use ChatGPT to Spoof Emails?
No, you cannot use ChatGPT to spoof email.
OpenAI ChatGPT is an ethical Generative AI chatbot that helps users generate content based on prompts.
This will help employees recognize and avoid potential threats.
These reasons include installing malware on victims devices, bypassing block lists, stealing identity, and more.
Lets explore common reasons for email spoofing.
Anonymity
Spoofing displays names and addresses in emails and provides threat actors with a cloak of anonymity.
This way, the threat actor will get to know the victims login credentials without exposing their true identity.
The email could contain phrases that mimic the colleagues usual communication style to make the email more convincing.
Identity Theft
One of the primary goals of email spoofing is to facilitate identity theft.
Once the attacker has this information, they can commit fraud or open accounts in the victims name.
Bypassing Block Lists
Most email providers allow users to block or mark suspicious emails as spam.
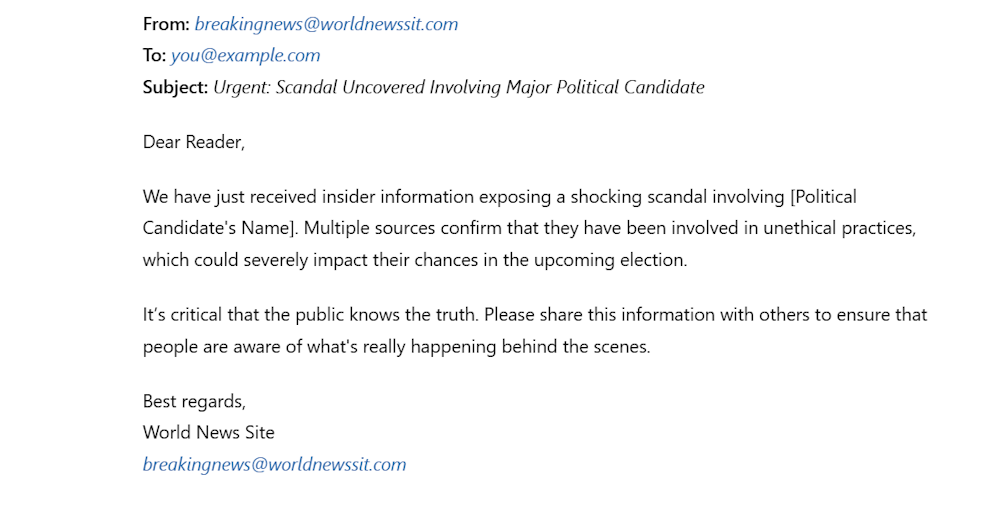
Phishing
Email spoofing is a common tactic used in phishing attacks.
These spoofed emails often appear legitimate, making it easier for cybercriminals to manipulate victims into harmful actions.
The email appears legitimate, complete with the CEOs signature and company branding.
They do so by sending out false or damaging messages under the guise of a trusted sense.
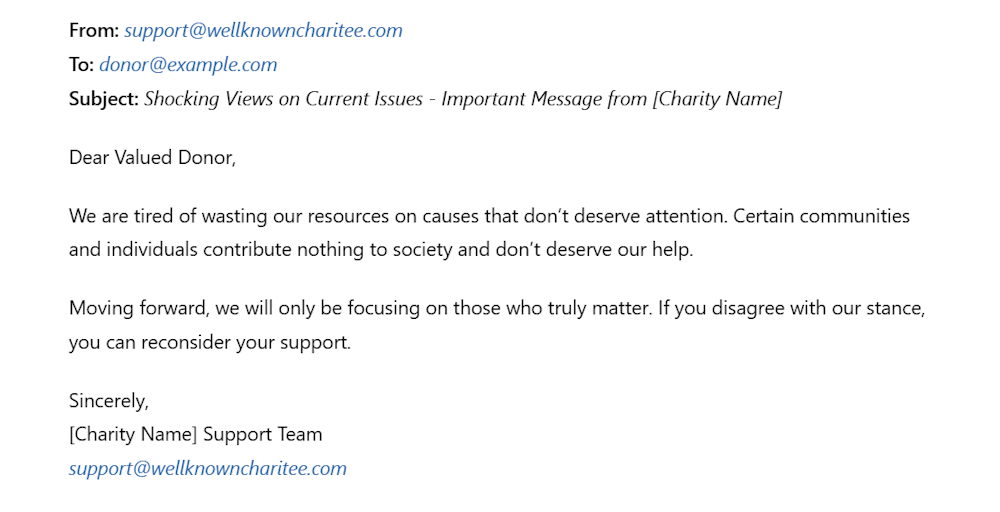
This tarnishes the charitys image, even if they had no involvement.
Manipulate Opinions
Hackers can employ email spoofing to change peoples opinions.
To do so, they send fake emails that seem to come from trusted sources.
How Can You Protect Against Email Spoofing?
Lets explore these methods in detail.
If not, the email may be flagged as spam or a phishing attempt.
SPF helps prevent spammers from using your domain to send fraudulent emails.
DKIM is an authentication method that uses digital signatures to ensure emails authenticity and integrity.
Here is how the process works.
The recipients server uses the senders public key to decrypt the hash and verify the emails authenticity.
It combines SPF and DKIM, instructing email servers to reject or quarantine suspicious messages.
Inspect Email Headers
Analyzing message headers can reveal inconsistencies between the display name and the sender address.
So, you should encourage your employees to inspect the headers of suspicious emails that require immediate action.
Here are some tips to help.
Any significant inconsistencies, such as different domains or unrelated addresses, are a red flag for spoofing.