We earn commission when you buy through affiliate links.
This does not influence our reviews or recommendations.Learn more.
For instance, an attacker might use targeted psychological tricks to persuade a victim to share confidential information.
Threat actors require time, skills, and advanced tools to breach your secured corporate devices.
However, tricking your unsuspecting employees into sharing login credentials is much easier.
So, it is crucial to prevent social engineering attacks.
This article will explore social engineering, its various types, and how to prevent social engineering attacks.
What Is Social Engineering?
Were doing urgent maintenance, and your account needs to be reset.
Can you like share your password so I can make the updates?
If the employee shares the password, the hacker may have access to the companys systems.
Social Engineering Attack Process
Cybercriminals use a structured process to carry out social engineering attacks.
They often collect information about potential targets before communicating with them.
Lets explore the types of social engineering next.
Here are key types of social engineering attacks, categorized by their techniques.
Phishing
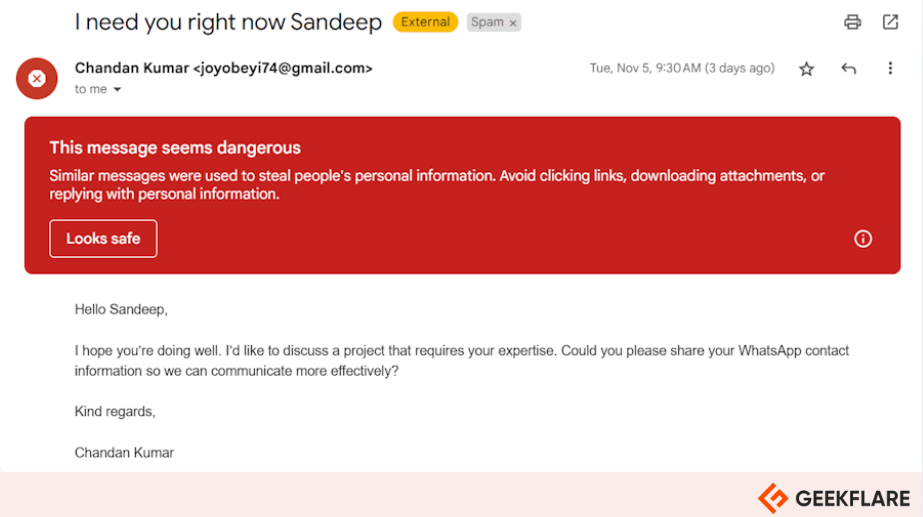
Phishing is the most common key in of social engineering attack.
These actors most often rely on email to run phishing campaigns.
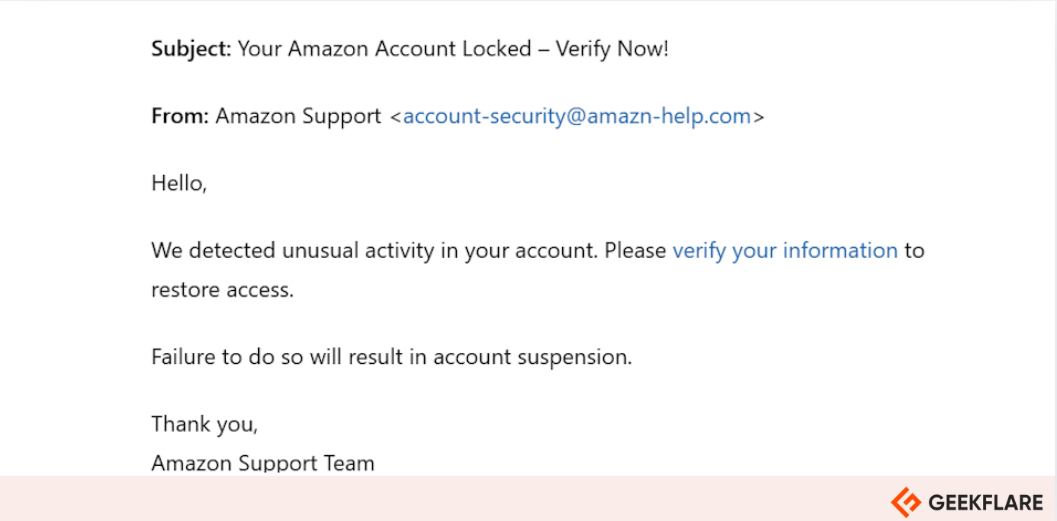
Here is an example of a phishing email.
Phishing attacks can come in various forms, such as vishing, smishing, and whaling.
Lets explore various types of phishing attacks below:
2.
Cybercriminals tell their stories using legitimate-looking images, wording, and tones to increase the success of pretexting attacks.
Pretexting attacks can occur online, in person, or on the phone.
For example, an attacker might leave a USB flash drive labelled Confidential in a public place.
This often occurs in places like office buildings or secure facilities.
To blend in, they may impersonate delivery or maintenance workers.
Later, the attacker can use the personal details to carry out future malicious campaigns like phishing attacks.
The attacker typically gains access to orspoofs a legitimate business email account.
Instead, they create a problem or situation that leads the victim to believe an issue needs resolution.
Scareware, which creates a fake security warning, is an example of a reverse social engineering attack.
For example, a cybercriminal wants to target a companys finance team.
Knowing they often visit a specific industry blog, the attacker infects this website with malware.
Lets explore the following real-world examples below.
He and his team then sent fraudulent invoices, successfully swindling$100 millionfrom these tech giants.
The fraudster used AI-based voice cloning technology to spoof his bosss voice.
CEO Fraud Against FACC
Austrian aerospace parts company FACC lost42 millionin a cyber-fraud scheme.
Belgian Bank Whaling Attack
A Belgian bank lost over70 millionin a whaling attack.
How To Spot a Social Engineering Attack
Identifying a social engineering attack is not rocket science.
All social engineering attacks have telltale signs if you look for them closely.
Here are some quick social engineering prevention techniques.
Educate Employees
Social engineering attacks exploit human psychology rather than vulnerabilities in your systems and networks.
So, training your employees on various types of social engineering attacks can help them become more vigilant.
You should also run simulated attacks to assess their preparedness to fight social engineering campaigns.
Encourage your employees to always confirm through a separate communication channel if there is a request for sensitive data.
Instead, they should verify by calling the CEO directly or sending a message on an internal platform.
This simple step helps confirm the request is legitimate and keeps sensitive data secure.
Limit Information Sharing
Cybercriminals leverage publicly available information to build their narratives and manipulate individuals.
The more information they have about their targets, the more sophisticated their attacks will be.
So, you should encourage your staff to limit sharing personal information online.
As a result, employees are less likely to fall prey to social engineering attacks.
Insights gathered through reporting can help your security team implement the righttypes of security controlsto block social engineering attacks.
Use Anti-Phishing Tools
Phishing is the most common pop in of social engineering attack.
Implementing one of thebest anti-phishing toolsin your organization can significantly reduce the risk of these attacks.
Enforce Physical Security
Strong physical security can help prevent unauthorized personnel from entering your premises.
By controlling who enters your premises, you might easily thwart tailgating attacks.
Conclusion
Social engineering poses a significant cybersecurity threat because it exploits human behaviour.
With AI advancements, cybercriminals can now craft even more convincing phishing campaigns.
Your defence against social engineering attacks is only as strong as your employees vigilance.