We earn commission when you buy through affiliate links.
This does not influence our reviews or recommendations.Learn more.
How are you securing your API?

Its the age of the digital economy explosion, and massive data loads are being piped through APIs.
Business, gaming, education, weather, science, arts.
You name it, everything works on APIs.

For a world so fundamentally reliant on APIs, theres surprisingly little focus on security.
For system admins, the default security offered by their infrastructure or service provider is what they rely on.
Not a pretty sight at all, if you ask me.

Needless to say, theres a lot at stake, which we realize only when somethingtruly terriblehappens.
But be cautioned that at the end of the day, no security strategy is perfect.
The below API protection tools can increase your API security manyfold, so they are recommended.
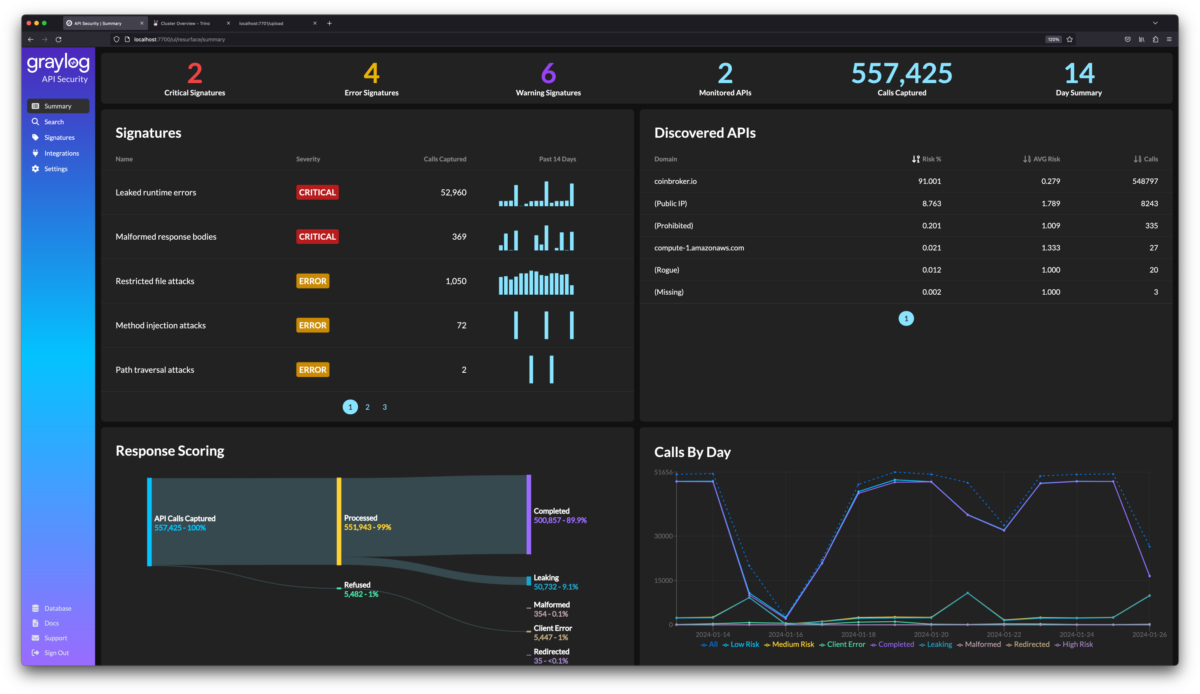
Cloudflares extensive worldwide data pipe facilitates the transmission of vast amounts of traffic through its API gateway.
Cloudflare API Gateway protects against OWASP API risks.
It is the only self-managed API solution that captures the full payload of both API requests and responses.

Invicti
Invicticomes with a USP of proof-based scanning.
It offers OAuth 2.0 authorization and is designed for both mobile and web applications.
It is also compatible with third-party API management services.

It offers you extra flexibility so that you dont have to secure your APIs using extra gateway instances.
Okta encompasses identity-driven policy to control different types of users and services under one roof.
Define access depending upon user profiles, networks, groups, consent, and clients.
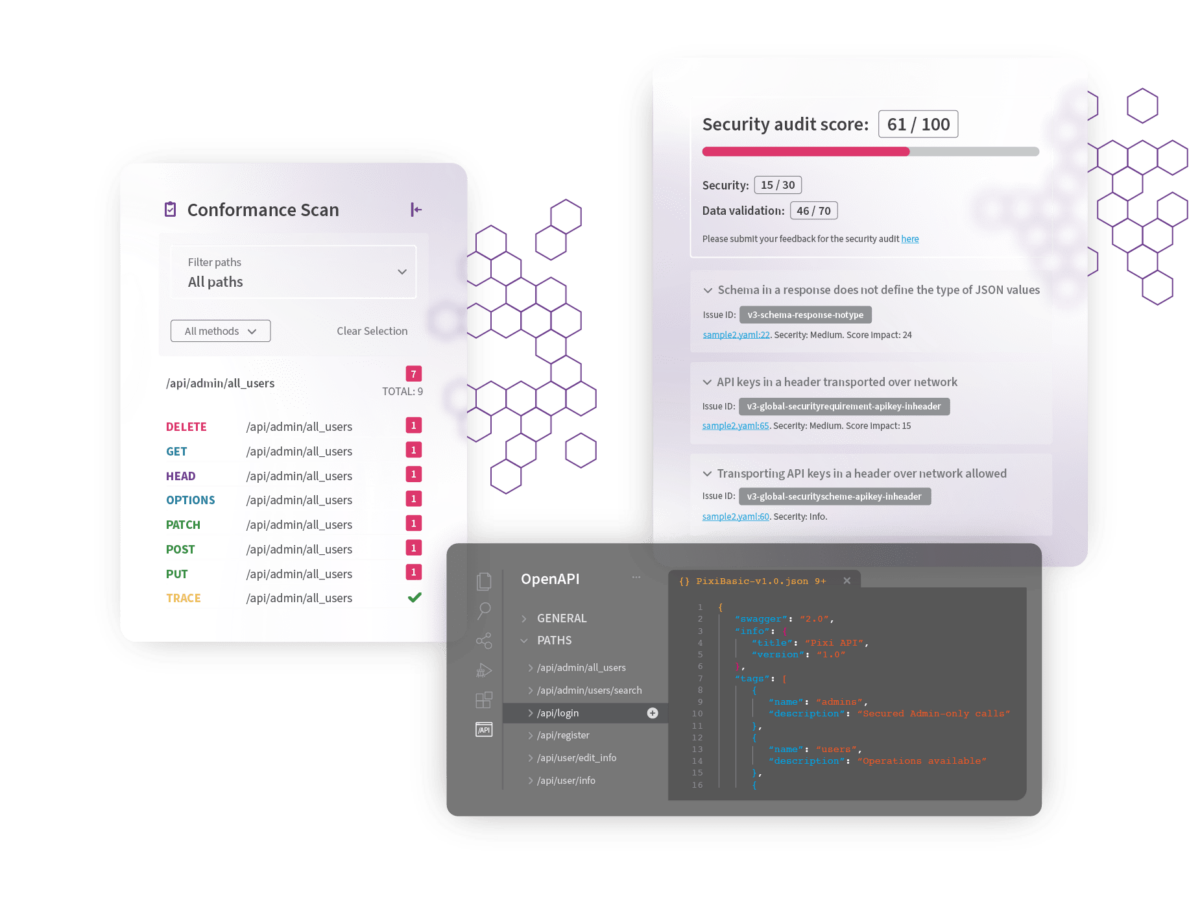
Extend tokens using dynamic data from your internal systems to enjoy faster integration and seamless migration.
It facilitates a centralized administration for APIs and lets you protect API resources.
Okta focuses on security by allowing you to safeguard access between different micro-services.

The platform is trusted by top brands like Verizon, Ford, Bridgestone, Allianz, etc.
The company claims to be the only platform that ensures security governance and compliance from design to runtime.
More than 800k developers adopt 42crunch API tools.
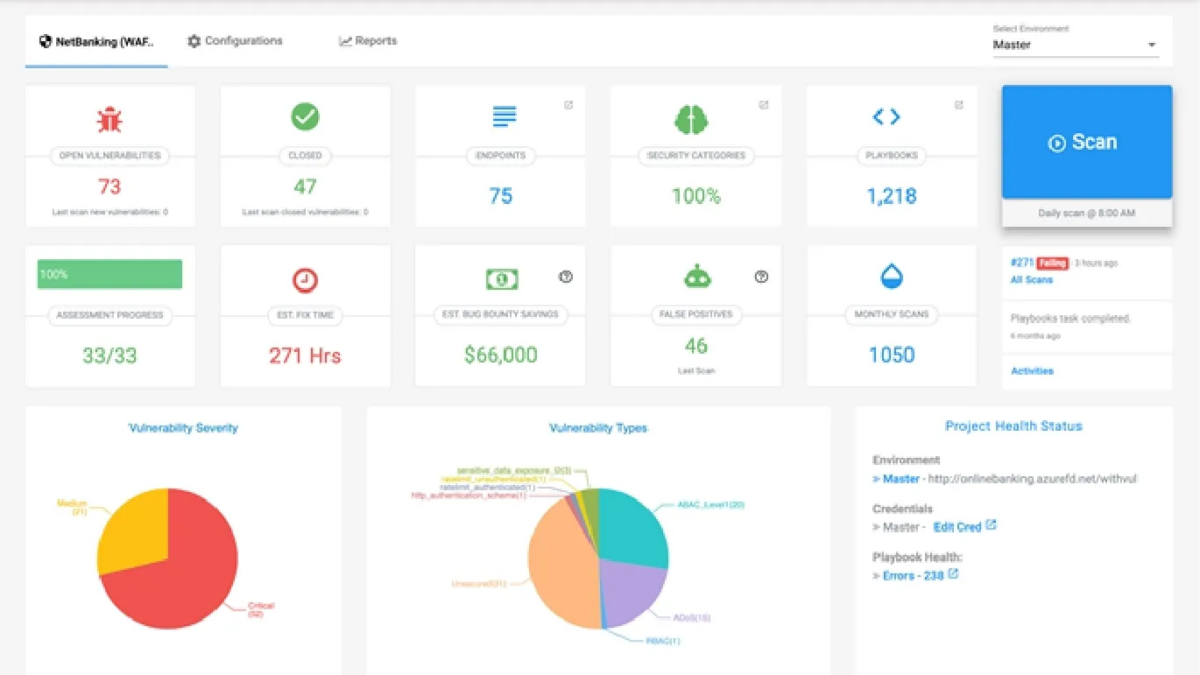
It scans web apps and APIs, finds vulnerabilities, and offers detailed reports on how to resolve them.
Probely provides a documented API and adapts vulnerability severity according to context.
It ensures compliance with standards like PCI-DSS, OWASP TOP 10, ISO27001, HIPAA, and GDPR.

Try it free for 14 days.
APIsec
APIsecprovides an automated platform for proactive and continuous API security testing.
It builds client trust by thoroughly testing updates and releases to ensure a secure production environment.

The platform automates comprehensive security testing for APIs throughout the software development lifecycle (SDLC).
It enables API discovery, analysis, and execution of customized attack scenarios before production.
APIsec helps to get rid of repetitive manual third-party testing by automating the API security testing.
APIsec seamlessly integrates with CI/CD, ticketing, and communication platforms, ensuring a smooth workflow.
Cequence
Cequenceis a multi-award-winning platform for API discovery, inventory, compliance, and dynamic testing.
The platform can be easily integrated with your existing API and security infrastructure.
Cequence claims to have saved millions of dollars and billions of users while also ensuring the security of transactions.
The platform offers freeAPI security assessment.
Why should we secure API endpoints?
We need to secure endpoints because, thats what the business depends on.
Not securing the API endpoints leads to the below undesirable consequences for the business.
Business loss
This is the obvious one.
If someone succeeds in messing with your API endpoints, it will bring everything to a screeching halt.
Imagine a currency exchange being down for a few minutes!
So much so that it might even spell the end of your business.
Well, not quite.
Should this happen enough time, youll have a culture on your hands that youll regret letting develop.
Competitors gains
So lets say there was a breach, but there was no actual loss.
Once again, good luck trying to convince the market.
All in all, there are consequences to security breaches that go beyond losing money.
Heres what most security experts recommend.
So, always makehttpstheonlyoption available.
No matter how trivial an endpoint might seem, connecting overhttpshouldnt even be an option.
The only suggested option is asymmetric (or one-way) encryption algorithms for storing passwords.
Validate input
This sounds like a no-brainer, but youll be surprised how many APIs fall for this.
Trying to accept and parse ridiculously large inputs will only serve to blow up the API.
Try a few of them from the list and see what works best for your requirements.